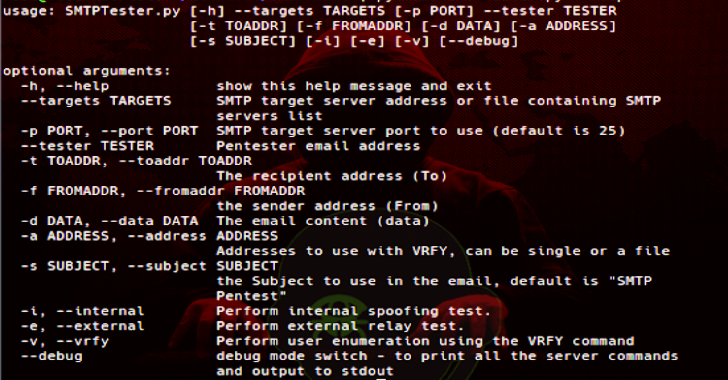
SMTPTester : Small Python3 Tool To Check Common Vulnerabilities In SMTP Servers
SMTPTester is a python3 tool to test SMTP server for 3 common vulnerabilities: Spoofing - The ability to send a mail on behalf of an internal userRelay - Using this SMTP server to send email to other address outside of the organizationUser Enumeration - using the SMTP VRFY command to check if specific username andor email address exist within the...
Tylium : Primary Data Pipelines For Intrusion Detection, Security Analytics & Threat Hunting
Tylium is a primary data pipelines for intrusion detection, security analytics and threat hunting. These files contain configuration for producing EDR (endpoint detection and response) data in addition to standard system logs. These configurations enable the production of these data streams using F/OSS (free and / or open source tooling.) The F/OSS tools consist of Auditd for Linux;...
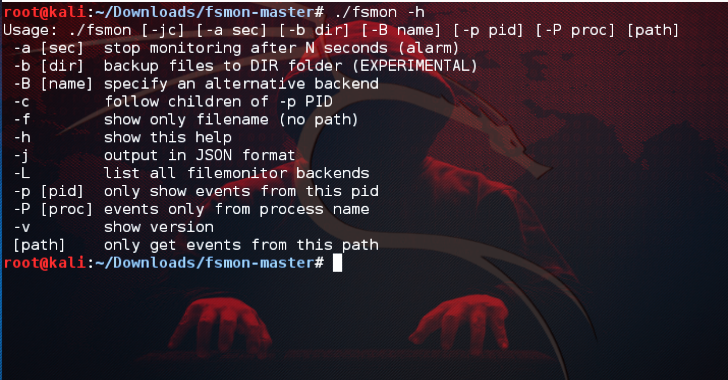
FSMon : Monitor Filesystem On iOS / OS X / Android / FirefoxOS / Linux
FSMon or FileSystem Monitor utility that runs on Linux, Android, iOS and OSX. Brought to you by Sergi Àlvarez at Nowsecure and distributed under the MIT license. Usage The tool retrieves file system events from a specific directory and shows them in colorful format or in JSON. It is possible to filter the events happening from a specific program name or process...
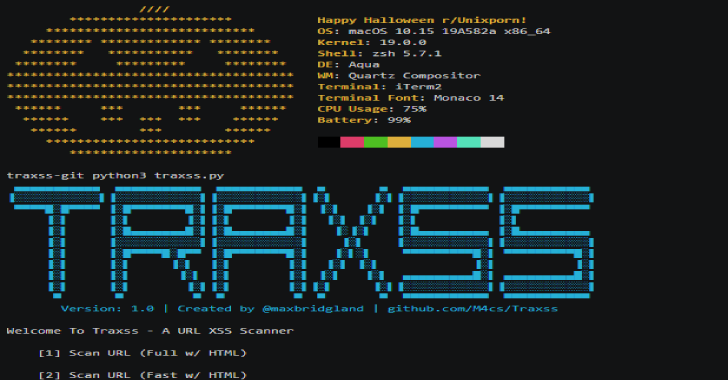
Traxss : Automated XSS Vulnerability Scanner
Traxss is an automated framework to scan URLs and webpages for XSS Vulnerabilities. It includes over 575 Payloads to test with and multiple options for robustness of tests. View the gif above to see a preview of the fastest type of scan. Getting Started Prerequisites Traxss depends on Chromedriver. On MacOS this can be installed with the homebrew command: brew install cask...
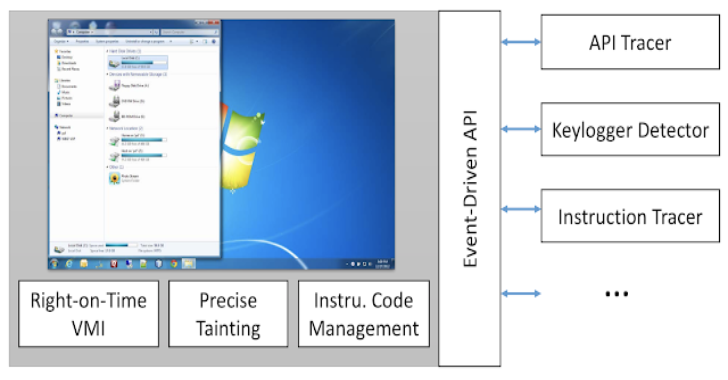
DECAF : Dynamic Executable Code Analysis Framework
DECAF (short for Dynamic Executable Code Analysis Framework) is a binary analysis platform based on QEMU. This is also the home of the DroidScope dynamic Android malware analysis platform. DroidScope is now an extension to DECAF. DECAF++, the new version of DECAF, taint analysis is around 2X faster making it the fastest, to the best of our knowledge, whole-system...
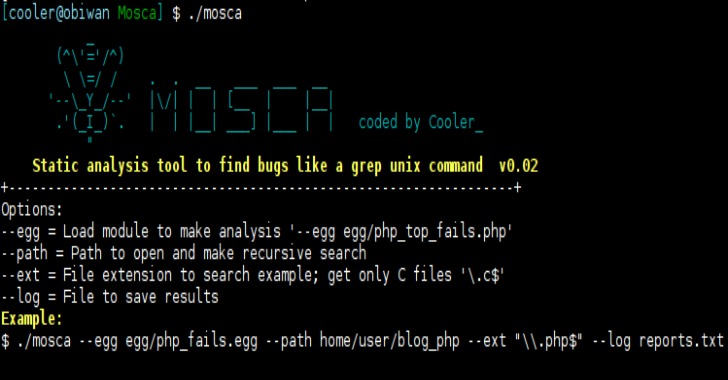
Mosca : Manual Search Tool To Find Bugs Like A Grep Unix Command
Mosca is a manual analysis tool to find bugs like a grep unix command and since it is not dynamic the uses static code to search don't confuse with academic views hahaha don't have graph here or CFG which is a simple "grep" egg modules is a config to find to vulnerabilitiesyou can use at C, PHP, javascript, ruby etcSave...
MalConfScan : Volatility Plugin For Extracts Configuration Data Of Known Malware
MalConfScan is a Volatility plugin extracts configuration data of known malware. Volatility is an open-source memory forensics framework for incident response and malware analysis. This tool searches for malware in memory images and dumps configuration data. In addition, this tool has a function to list strings to which malicious code refers. Supported Malware Families It can dump the following malware configuration data, decoded...
ISPY : Eternalblue/Bluekeep Scanner & Exploit
ISPY V1.0 is a eternalblue(ms17-010)/bluekeep(CVE-2019-0708) scanner and exploit ( Metasploit automation ) . How to install? git clone https://github.com/Cyb0r9/ispy.git cd ispy chmod +x setup.sh ./setup.sh Also Read - B2R2 : A Collection of Algorithms, Functions And Tools For Binary Analysis Screenshots Tested On Parrot OSKali linux Demo https://www.youtube.com/watch?v=WCa5N5_zKgw&list=UUv9HdZbTOo0iBG5X2qaqmqg Disclaimer Usage of ispy for attacking targets without prior mutual consent is illegal. ispy is for security testing purposes...
Zeek : A Powerful Network Analysis Framework
Zeek is a powerful network analysis framework that is much different from the typical IDS you may know. Key Features In-depth Analysis it ships with analyzers for many protocols, enabling high-level semantic analysis at the application layer.Adaptable and Flexible it's domain-specific scripting language enables site-specific monitoring policies and means that it is not restricted to any particular detection approach.Efficient it targets high-performance networks...
Maryam : Open-source Intelligence(OSINT) Framework
Maryam is a full-featured open-source intelligence(OSINT) framework written in Python. Complete with independent modules, built in functions, interactive help, and command completion, provides a command-line environment for used forensic and open-source intelligence(OSINT). Maryam is a completely modular framework and makes it easy for even the newest of Python developers to contribute. Each module is a subclass of the "module"...