Deployment Instructions – Setting Up The PinguCrew Project With Docker, Python, And Node.js
At the moment the default configuration when the run_server butler command uses docker containers to run the MongoDB, rabbit-mq and minio services. It is mandatory to have docker service installed in case the the fault configuration is used. To install docker you can refer to the official installtion instructions Install Docker Engine: Python To run the backend server and the Pingu bot it is...
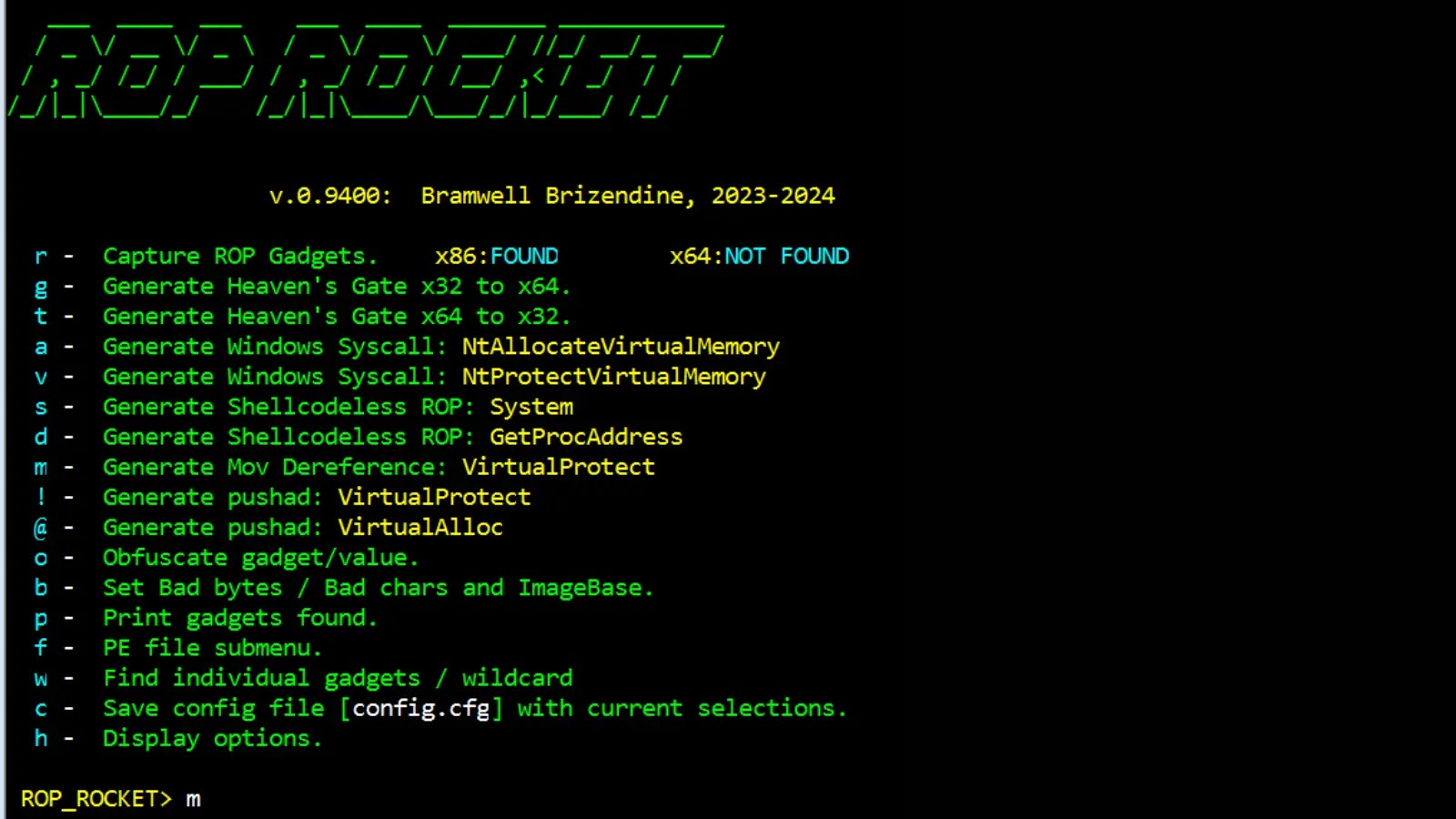
ROP ROCKET – The Next Evolution Of ROP Chain Generation
This new, advanced ROP framework made it debute at at DEF CON 31 with some unprecedented capabilities. ROCKET generates several types of chains, and it provides new patterns or techniques. Please note that this is still a work in progress, with some updated and enhanced capabilities to be added. Updates should be regular. If you encounter issues, please put them...
ANDROPHSY – Comprehensive Forensic Tool For Android Smartphones
ANDROPHSY is an opensource forensic tool for Android smartphones that helps digital forensic investigator throughout the life cycle of digital forensic investigation. Services provided by ANDROPHSY includes Digital forensic case and evidence management Raw data acquisition – physical acquisition and logical – file system level acquisition Meaningful evidence extraction and analysis support Evidence presentation License Information Please read license agreement carefully here. Disclaimer Notice Before go further from...
App Metadata – A Comprehensive Guide To iOS, Android, And UWP Application Metadata Extraction
This package has been deprecated, and is not being maintained by MSFT anymore. This library helps you retrieve the most frequently extracted metadata and icons within iOS, Android and UWP applications. Usage Import import { Extract } from 'app-metadata'; usage let results = await Extract.run(pathName); Results The library will return the information most relevant for the supported platforms. For a better understanding of the details retrieved refer...
Check-If-Email-Exists : A Tool To Verify Email Addresses Without Sending Emails
This is open-source, but I also offer a SaaS solution that has check-if-email-exists packaged in a nice friendly web interface. If you are interested, find out more at Reacher. If you have any questions, you can contact me at amaury@reacher.email. Get Started 3 non-SaaS ways to get started with check-if-email-exists. 1. HTTP Backend Using Docker (Popular Method ) This option allows you to run a HTTP backend using Docker,...
IPGeolocation – A Comprehensive Guide To The IPGeoLocation Tool
IPGeoLocation is a powerful tool designed to fetch detailed geolocation information for any given IP address or domain. Utilizing the comprehensive services of ip-api, this Python-based application offers extensive functionality including proxy support, multiple output formats, and integration with Google Maps. Ideal for cybersecurity professionals and enthusiasts, IPGeoLocation streamlines the process of IP analysis and geolocation retrieval. A tool to...
Firefox Decrypt – Mastering Password Recovery For Mozilla Applications
As of 1.0.0 Python 3.9+ is required. Python 2 is no longer supported. If you encounter a problem, try the latest release or check open issues for ongoing work. If you definitely need to use Python 2, Firefox Decrypt 0.7.0 is your best bet, although no longer supported. Table Of Contents About Usage Advanced Usage Non-Interactive mode Ouput formats CSV/Tabular Pass - Password Store Troubleshooting Windows MacOSX Testing Derived works About Firefox Decrypt is a tool to extract passwords from...
Face Recognition – Mastering Facial Recognition With Python
Recognize and manipulate faces from Python or from the command line with the world's simplest face recognition library. Built using dlib's state-of-the-art face recognition built with deep learning. The model has an accuracy of 99.38% on the Labeled Faces in the Wild benchmark. This also provides a simple face_recognition command line tool that lets you do face recognition on a folder of images from the command...
PowerForensics – PowerShell Digital Forensics
The purpose of PowerForensics is to provide an all inclusive framework for hard drive forensic analysis. PowerForensics currently supports NTFS and FAT file systems, and work has begun on Extended File System and HFS+ support. All PowerForensics documentation has been moved to Read The Docs. Detailed instructions for installing PowerForensics can be found here. Public API PowerForensics is built on a C# Class Library (Assembly)...
GasMasK – The Comprehensive OSINT Toolkit
GasMasK is a versatile open-source tool designed for extensive information gathering and OSINT (Open Source Intelligence) operations. It seamlessly integrates various functionalities to probe domains, social media, and more, using a multitude of data sources like Shodan, Censys, and DNS records. Licensed under GPLv3, GasMasK v2.0 offers a robust framework for cybersecurity professionals and researchers. Dive into the capabilities...













.webp)
.webp)


.webp)
