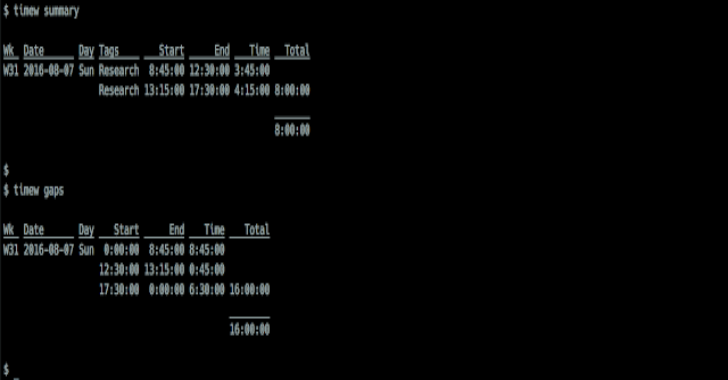
Timewarrior is a time tracking utility that offers simple stopwatch features as well as sophisticated calendar-based backfill, along with flexible reporting. It is a portable, well supported and very active Open Source project. Installing From Package Thanks to the community, there are binary packages available here. Building Timewarrior Building Timewarrior yourself requires gitcmakemakeC++ compiler, currently …
Tag Archives: Commandline
Paramkit : A Small Library Helping To Parse Commandline Parameters
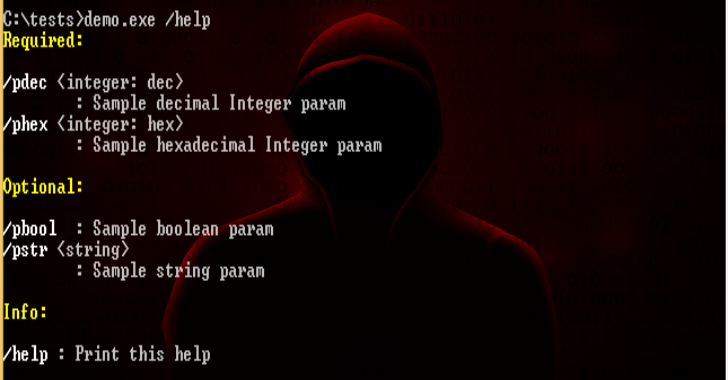
Paramkit is a small library helping to parse commandline parameters. Objectives “like Python’s argparse but for C/C++” compact and minimalistic easy to use extendable Also Read – WiFiPumpkin3 : Powerful Framework For Rogue Access Point Attack Demo Print help for each parameter: Easily store values of popular types, and verify if all required parameters are …
Continue reading “Paramkit : A Small Library Helping To Parse Commandline Parameters”