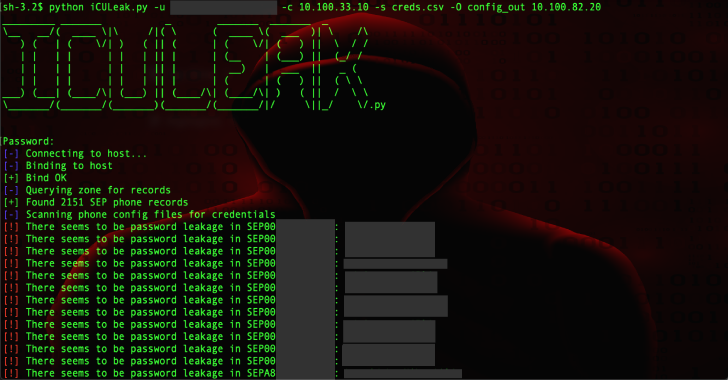
iCULeak (iCULeak.py) is a tool to find and extract credentials from phone configuration files in environments managed by Cisco’s CUCM (Call Manager). When using Cisco’s CUCM (Call Manager), phone configuration files are stored on a TFTP server. These VoIP phone configuration files quite frequently contain sensitive data, including phone SSH/admin credentials. There is also an …