APPLICATIONS
HOT NEWS
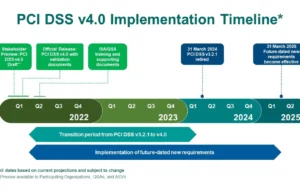
PCI-SegTest : Streamlining PCI DSS v4.0 Compliance Through Advanced Network Segmentation...
The "PCI-SegTest" tool is a specialized utility designed to ensure compliance with PCI DSS v4.0 by testing network segmentation and egress controls within the...
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2025