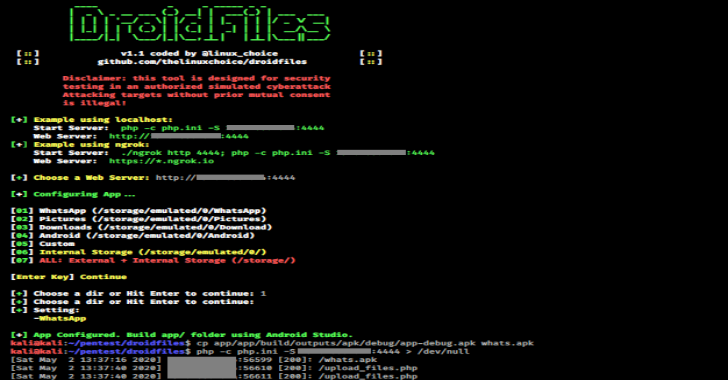
DroidFiles is a tool used to get files from Android directories, internal and external storage (Pictures, Downloads, Whatsapp, Videos, …) Requirements Android Studio (https://developer.android.com/studio) Also Read – Locator : Geolocator, IP Tracker, Device Info by URL (Serveo & Ngrok) Usage # git clone https://github.com/thelinuxchoice/droidfiles# cd droidfiles# bash droidfiles.sh