APPLICATIONS
HOT NEWS
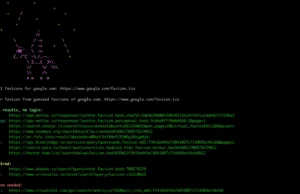
FAVICORN : A Comprehensive Tool For Favicon-Based Website Searches
Favicorn is an innovative tool designed to search websites by their favicons, offering a unique approach to online exploration and cybersecurity research.
By leveraging...
© kalilinuxtutorials.com 2025