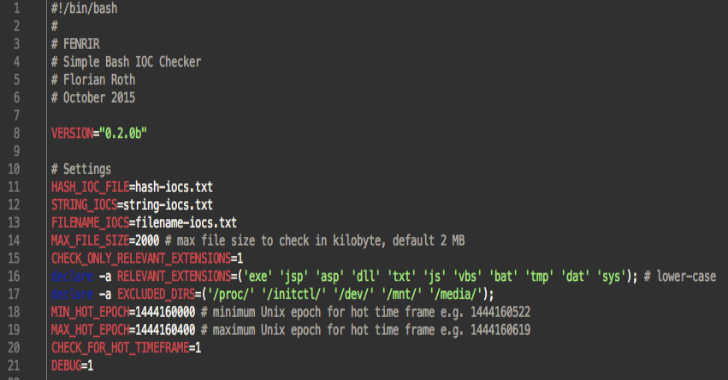
Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise (IOCs): HashesMD5, SHA1 and SHA256 (using md5sum, sha1sum, sha -a 256) File Namesstring – checked for substring of the full path, e.g. “temp/p.exe” in “/var/temp/p.exe” Stringsgrep in files C2 Serverchecking for C2 server strings in ‘lsof …