APPLICATIONS
HOT NEWS
Process-Dump : Windows Tool For Dumping Malware PE Files From Memory...
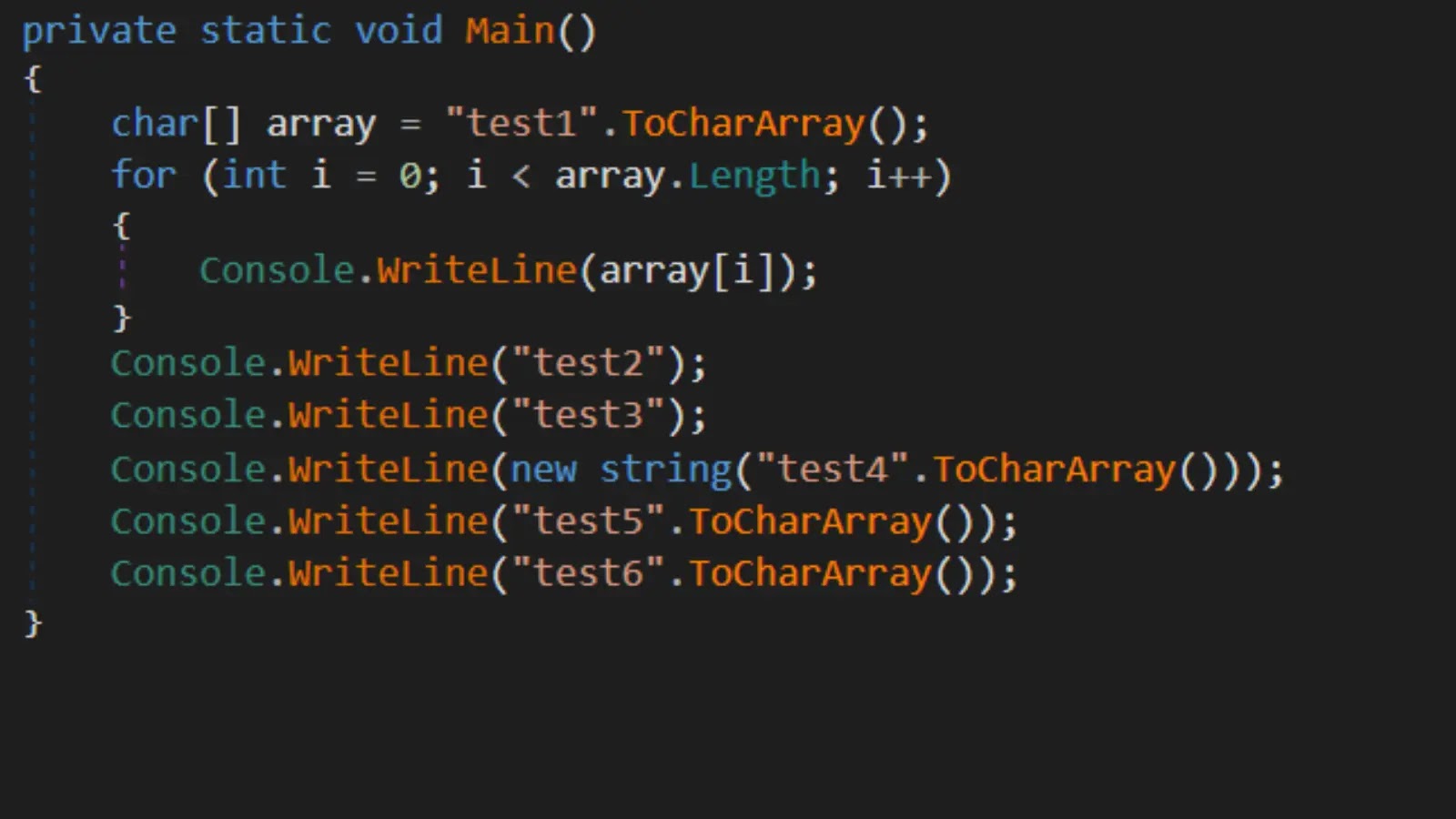
Process Dump is a Windows reverse-engineering command-line tool to dump malware memory components back to disk for analysis. Often malware files are packed and...
Latest Updates on Hacking Tools, Cybersecurity News & Writeups
Contact us: admin@kalilinuxtutorials.com
© ©kalilinuxtutorials.com 2025