APPLICATIONS
HOT NEWS
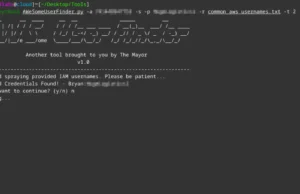
AWeSomeUserFinder : Harnessing AWS IAM For Username Enumeration And Password Security
AWS IAM Username Enumerator and Password Spraying Tool in Python3
In order to use the tool with the UpdateAssumeRolePolicy method, the IAM user account utilized...
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2025