APPLICATIONS
HOT NEWS
Hack The Box Reporting Using SysReptor – Streamline Your Pentesting Documentation
Discover the power of SysReptor, a versatile tool designed to simplify Hack The Box reporting.
Whether you prefer cloud-based solutions or self-hosting, SysReptor makes...
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2024

.webp)








.webp)


.png)




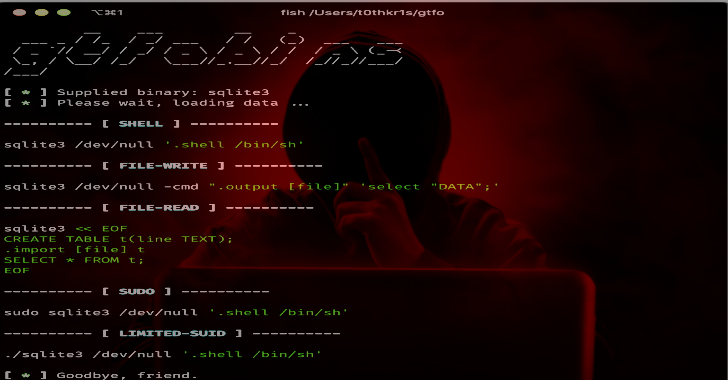
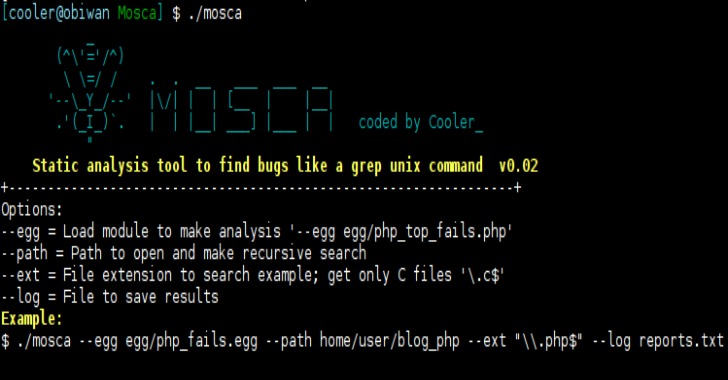
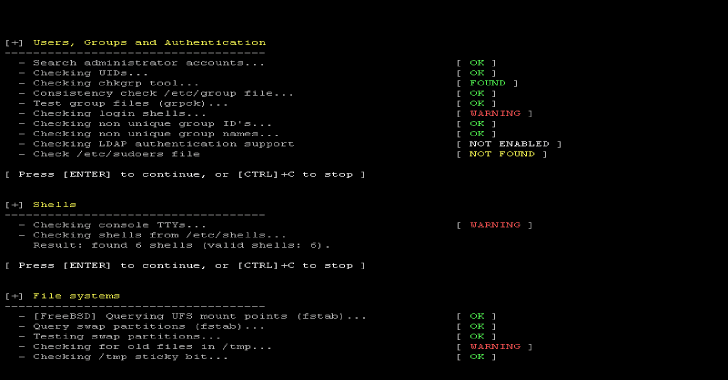

.webp)


