Passwords are the first line of defense for most computer systems and online accounts. A strong, complex password can help thwart hackers and unauthorized access. However, many users choose weak, easy-to-guess passwords that provide little security.
Password cracking tools, like John the Ripper, are designed to break into weak passwords.
These tools use a variety of techniques like dictionary attacks, brute force attacks, and hash cracking to guess passwords.
A dictionary attack uses a list of common words and passwords to guess a password. A brute force attack tries all possible combinations of letters, numbers, and symbols to crack a password.
Hash cracking deciphers the cryptographic hash of a password into the original password. With increasing computing power, longer, more complex passwords are needed to avoid password cracking
What is John The Ripper?
John the Ripper, commonly just called “John,” is a free open-source password-cracking software tool.
Initially created for Unix systems, John now runs on a variety of platforms and is popular with cybersecurity professionals and hackers alike.
Let’s have a look at a practical demonstration of the same.
It can be used to crack passwords, hashes, ZIP files, sshkeys, password-protected documents,etc. John supports three modes to crack the passwords:
1. Single Crack Mode: In this mode, John the Ripper focuses on cracking a single password hash at a time. It inputs a specific hash and applies various techniques, such as dictionary attacks, brute force attacks, and rule-based attacks, to crack the password.
2. Wordlist Crack Mode: In wordlist mode, John the Ripper uses a predefined list of words (commonly known as a wordlist or dictionary) to attempt to crack passwords. It systematically checks each word in the list against the given password hashes to find a match.
3. Incremental Mode: The incremental mode of John the Ripper systematically generates and tests all possible password combinations within a specified length range. It starts with the shortest passwords and progressively moves towards longer ones. This mode is useful when there is no specific information about the password and need to exhaustively search all possible combinations.
John is mostly installed by default on the Linux system; if not it can be easily installed using the command:
sudo apt install john
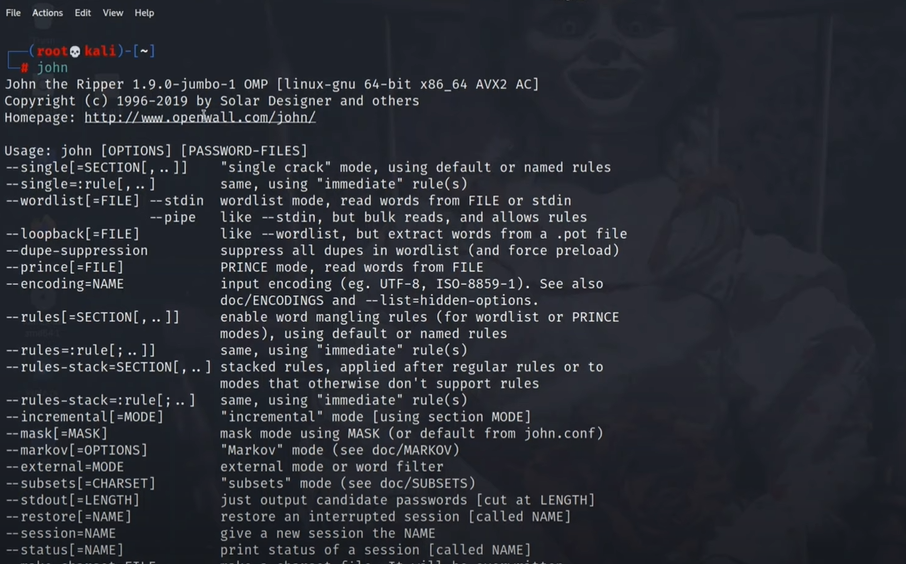
–> John has multiple flags, which can be seen either using “man john” or just typing “john” in the terminal.
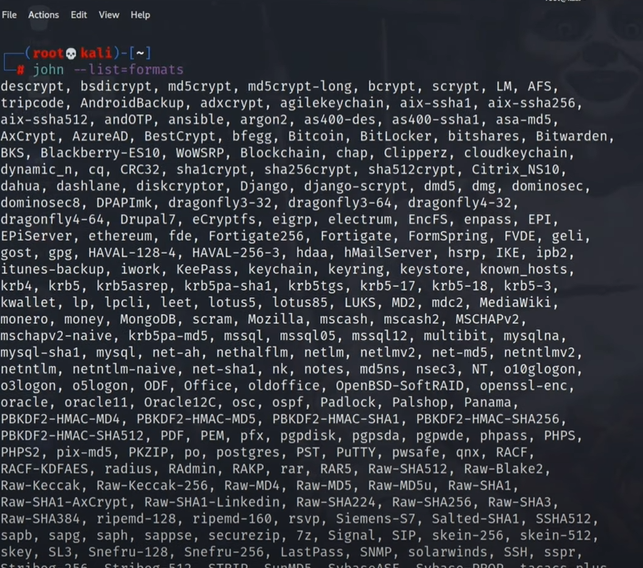
–> JohnTheRipper can deal with a large number of hash or file formats. john –list=formats displays all the supported option by the tool.
Cracking Hashes With John The Ripper
With this tool, it is possible to crack multiple variants of hashes such as MD5, SHA1, SHA-256, Bcrypt, NTLM, etc. For example:
MD5
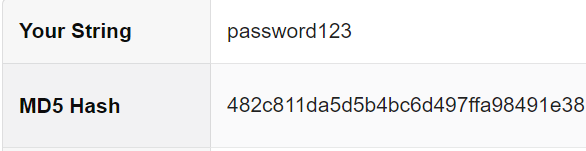
Plain text: password123
MD5 of plaintext: 482c811da5d5b4bc6d497ffa98491e38
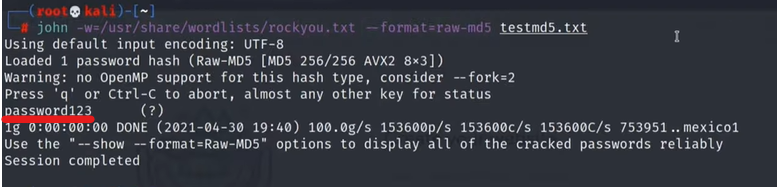
The next step would be to save the hash in a textfile and crack it using the command:
john -w=/usr/share/wordlists/rockyou.txt --format=raw-md5 testmd5.txtCommand explanation:
john : the name of tool
-w : It tells the location of wordlist to be used against the hash.
--format : It specifies the type of hash need to be cracked. ( It can detect automatically too.)
testmd5.txt : file that contains the hash.Note: Either you can use the default wordlist or make your wordlist as per the requirement.
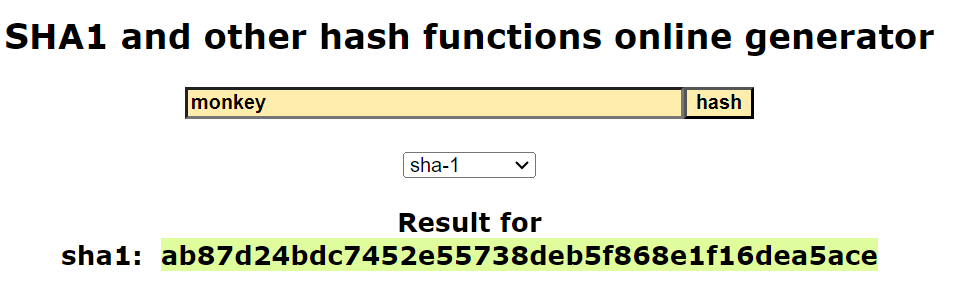
SHA1
Plaintext: monkey
SHA1: ab87d24bdc7452e55738deb5f868e1f16dea5ace
Again following the same command format:
john -w=/usr/share/wordlists/rockyou.txt --format=raw-sha1 testsha1.txt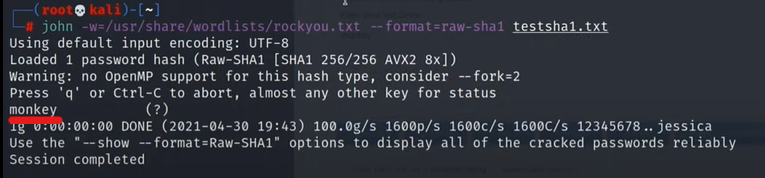
Cracking ZIP, SSH, and others
–> Cracking ZIP files
zip2john <location to zip file> <output.txt> john -w=<wordlist> --format=<format> output.txt
Here, the zip2john package is first used to generate a hash of the given zip file. In this it is being saved as output.txt. Then by the traditional method, the hash can be cracked, and finally, zip can be unlocked with the cracked password.
–> Cracking SSH passwords
ssh2john <location to id_rsa> <output.txt> john -w=<wordlist> --format=<format> output.txt
Similarly, there are multiple more packages and binaries supported by John The Ripper for different tasks, some of them are:
- SIPdump
- base64conv
- bitlocker2john
- calc_stat
- cprepair
- dmg2john
- eapmd5tojohn
- genmkvpwd
- gpg2john
Increasing computing power requires longer, more complex passwords to avoid password cracking. Some key tips for choosing a secure password are:
•Use at least 8-12 characters or more: the longer the better
•Use a mix of letters, numbers and symbols
•Don’t use common dictionary words or personal information
•Don’t reuse the same password across sites
•Change your passwords regularly
Strong password security is one aspect of maintaining a robust overall security posture. Implementing other security measures, such as using antivirus software, practicing safe browsing habits, and being mindful of the websites you visit, will further enhance your protection against cyber threats.
Please consider following and supporting us to stay updated with the latest info