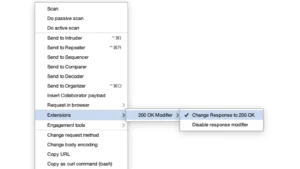
Web Application Security
Web application security focuses on protecting websites and online platforms from cyber threats and vulnerabilities. This category features tutorials, tools, and best practices for securing applications against common attacks like SQL injection, cross-site scripting (XSS), insecure authentication, and misconfigurations.
We cover security testing frameworks, vulnerability scanners, and penetration testing tools designed to help developers, testers, and security professionals strengthen their applications. Our guides also include OWASP Top 10 practices, threat modeling, and compliance strategies to safeguard sensitive data and maintain user trust.
Whether you’re a beginner learning web app security or an advanced professional improving security posture, this section provides actionable resources to detect, prevent, and respond to threats effectively.
Latest News

How AI Puts Data Security at Risk

The Evolution of Cloud Technology: Where We Started and Where We’re Headed
.jpg)
The Evolution of Online Finance Tools In a Tech-Driven World

A Complete Guide to Lenso.ai and Its Reverse Image Search Capabilities
%20Works.jpg)
How Web Application Firewalls (WAFs) Work

How to Send POST Requests Using curl in Linux

What Does chmod 777 Mean in Linux

How to Undo and Redo in Vim or Vi

How to Unzip and Extract Files in Linux