AdvPhishing : This Is Advance Phishing Tool! OTP PHISHING
AdvPhishing is a advance phishing tool with OTP phishing Bypass. SPECIAL OTP BYPASS VIDEO WORKED Social Media HackLinkInstallation Termuxhttps://www.youtube.com/watch?v=LO3hX1lLBjIWhatsapp OTPhttps://www.youtube.com/watch?v=pyB63ym3QYsGoogle OTPhttps://www.youtube.com/watch?v=MhSb4My1lZoPaytm OTPhttps://www.youtube.com/watch?v=3TB_sISTw9UInstagram OTPhttps://www.youtube.com/watch?v=VmkV1rrw2-wPhone Pay OTPhttps://www.youtube.com/watch?v=ZgaoLubKBBoTelegram OTPhttps://www.youtube.com/watch?v=BhGyGkIDhO0 TECHNIQUE When victim enter his credentials, you need to go to original website and use those credentials to send real OTP to victim. Once he enter that OTP such OTP will also be there with you and...
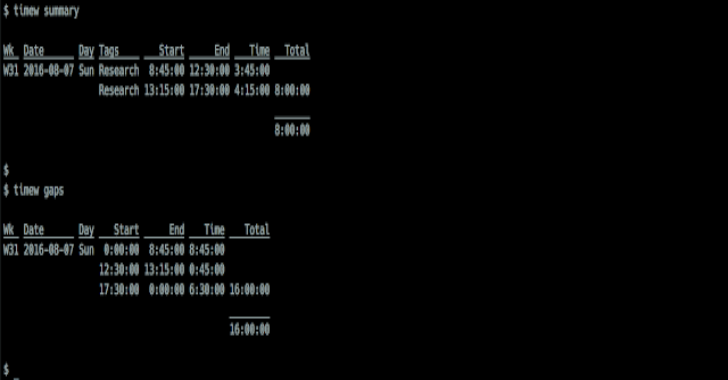
TimeWarrior : Commandline Time Reporting
Timewarrior is a time tracking utility that offers simple stopwatch features as well as sophisticated calendar-based backfill, along with flexible reporting. It is a portable, well supported and very active Open Source project. Installing From Package Thanks to the community, there are binary packages available here. Building Timewarrior Building Timewarrior yourself requires gitcmakemakeC++ compiler, currently gcc 4.8.1+ or clang 3.3+ for full C++11 supportPython 3,...
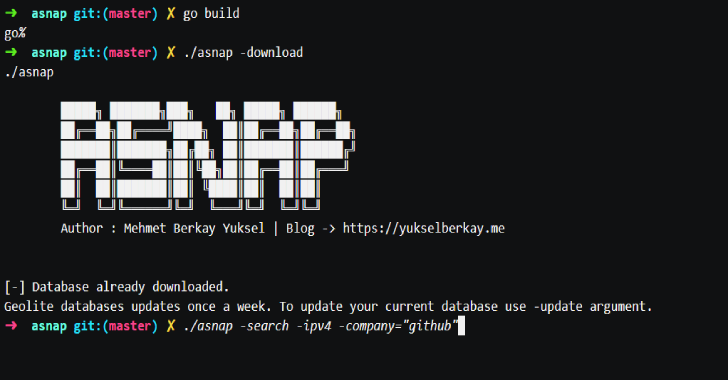
Asnap : Tool To Render Recon Phase Easier
Asnap aims to render recon phase easier by providing regularly updated data about which companies owns which ipv4 or ipv6 addresses and allows the user to automate initial port and service scanning. Installation Precompiled Binary If you have Go installed and configured in your $PATH enviroment variable, simply run: go get -u github.com/paradoxxer/asnap If you want to use precompiled binary, you also need...
SMB AutoRelay : Automation Of SMB/NTLM Relay Technique For Pentesting & Red Teaming Exercises
SMB AutoRelay provides the automation of SMB/NTLM Relay technique for pentesting and red teaming exercises in active directory environments. Usage Syntax: ./smbAutoRelay.sh -i <interface> -t <file> . Example: ./smbAutoRelay.sh -i eth0 -t ./targets.txt. Notice that the targets file should contain just the IP addresses of each target, one per line, to which you want to try the SMB/NTLM Relay technique. Run ./smbAutoRelay.sh ...
Powerglot : Encodes Offensive Powershell Scripts Using Polyglots
Powerglot encodes several kind of scripts using polyglots, for example, offensive powershell scripts. It is not needed a loader to run the payload. In red-team exercises or offensive tasks, masking of payloads is usually done by using steganography, especially to avoid network level protections, being one of the most common payloads scripts developed in powershell. Recent malware and APTs make...
Pastego : Scrape/Parse Pastebin Using GO And Expression Grammar
Pastego is a scrape/Parse Pastebin using GO and grammar expression (PEG). Installation $ go get -u github.com/notdodo/pastego Usage Search keywords are case sensitive pastego -s "password,keygen,PASSWORD" You can use boolean operators to reduce false positive pastego -s "quake && ~earthquake, password && ~(php || sudo || Linux || '<body>')" This command will search for bins with quake but not earthquake words and for bins with password but...
h2cSmuggler : HTTP Request Smuggling Over HTTP/2 Cleartext (H2C)
h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c) communications with h2c-compatible back-end servers, allowing a bypass of proxy rules and access controls. See my detailed write-up below for: Technical breakdown of the vulnerabilityInsecure-by-default servicesRemediation guidance Here: https://labs.bishopfox.com/tech-blog/h2c-smuggling-request-smuggling-via-http/2-cleartext-h2c How to test? Any proxy endpoint that forwards h2c upgrade headers can be affected. Because h2c is intended to be performed...
MapCIDR : Small Utility Program To Perform Multiple Operations For A Given sub-net/CIDR Ranges
MapCIDR is a small utility program to perform multiple operations for a given subnet/CIDR ranges. The tool was developed to ease load distribution for mass scanning operations, it can be used both as a library and as independent CLI tool. Features Simple and modular code base making it easy to contribute.CIDR distribution for distributed scanning.Stdin and stdout support for integrating in workflows Installation From...
Lil PWNY : Auditing Active Directory Passwords Using Multiprocessing In Python
Lil Pwny is a Python application to perform an offline audit of NTLM hashes of users' passwords, recovered from Active Directory, against known compromised passwords from Have I Been Pwned. The usernames of any accounts matching HIBP will be returned in a .txt file There are also additional features: Ability to provide a list of your own passwords to check AD...
Polypyus : Locate Functions In Raw Binaries By Extracting Known Functions
Polypyus learns to locate functions in raw binaries by extracting known functions from similar binaries. Thus, it is a firmware historian. Polypyus works without disassembling these binaries, which is an advantage for binaries that are complex to disassemble and where common tools miss functions. In addition, the binary-only approach makes it very fast and run within a few seconds....