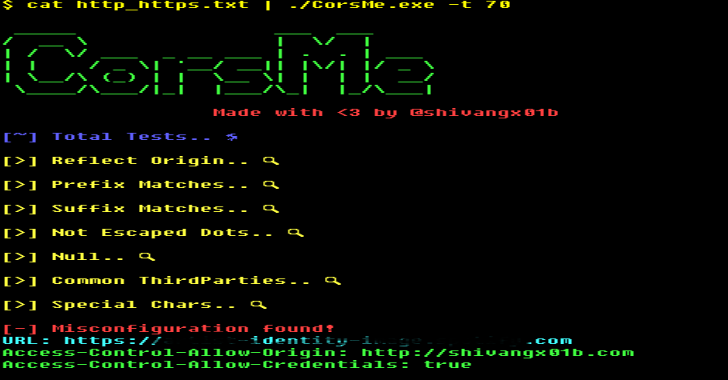
CorsMe : Cross Origin Resource Sharing MisConfiguration Scanner
A CorsMe misconfiguration scanner tool based on golang with speed and precision in mind ! Misconfiguration type this scanner can check for Reflect Origin checksPrefix MatchSuffix MatchNot Esacped DotsNullThirdParties (Like => github.io, repl.it etc.)Taken from Chenjj's github repoSpecialChars (Like => "}","(", etc.)See more in Advanced CORS Exploitation Techniques How to Install? $ go get -u github.com/shivangx01b/CorsMe Usage Single Url echo "https://example.com" | ./CorsMe Multiple...
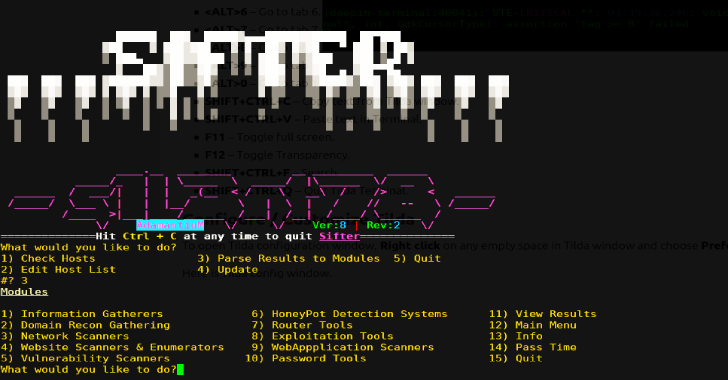
Sifter : OSINT, Recon & Vulnerability Scanner
Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to quickly perform recon tasks, check network firewall, enumerate remote and local hosts, and scan for the 'blue' vulnerabilities within microsft and if unpatched, exploit them. It uses tools like blackwidow and konan for webdir enumeration and attack surface...
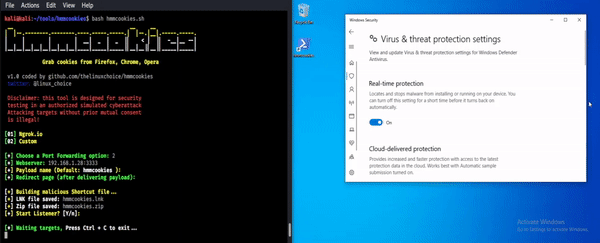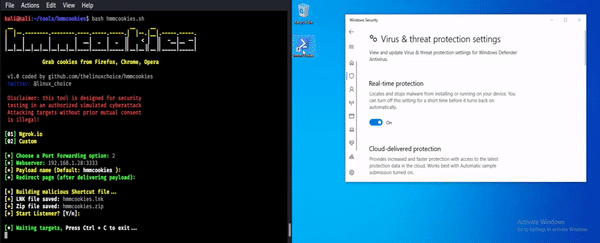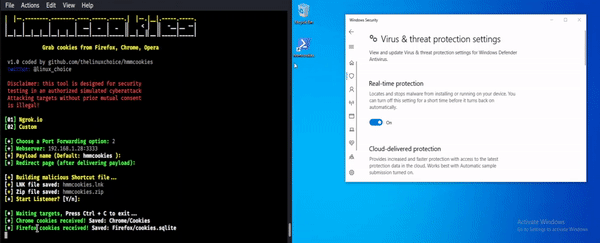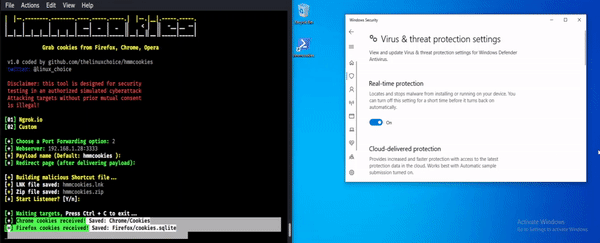
Hmmcookies – Grab Cookies From Firefox, Chrome & Opera
Hmmcookies is a tool used to grab cookies from Firefox, Chrome, Opera using a shortcut file (bypass UAC). Install git clone https://github.com/thelinuxchoice/hmmcookies cd hmmcookies bash hmmcookies.sh Disclaimer Usage of HMMCOOKIES for attacking targets without prior mutual consent is illegal. It's the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any...
Business Secure: How AI is Sneaking into our Restaurants
Prior to pandemic days, the restaurant industry talked of computers that might end up taking over their daily responsibilities. They’d joke about how a kiosk can communicate orders to the kitchen, much like they can. Well, now that we live in a global world that will be reluctant to dine with others, a shift in how we eat at...
InQL : A Burp Extension For GraphQL Security Testing
InQL is a security testing tool to facilitate GraphQL technology security auditing efforts. InQL can be used as a stand-alone script or as a Burp Suite extension. InQL Stand-Alone CLI Running inql from Python will issue an Introspection query to the target GraphQL endpoint in order fetch metadata information for: Queries, mutations, subscriptionsIts fields and argumentsObjects and custom object types InQL can inspect...
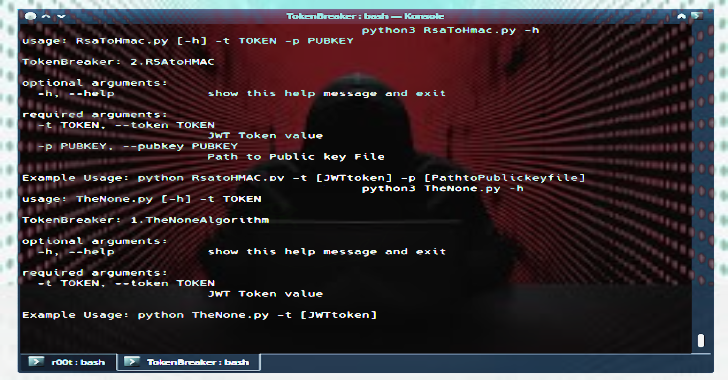
Token Breaker : JSON RSA To HMAC & None Algorithm Vulnerability POC
Token Breaker is focused on 2 particular vulnerability related to JWT tokens. None AlgorithmRSAtoHMAC Refer to this link about insights of the vulnerability and how an attacker can forge the tokens Try out this vulnerability here TheNone Usage Usage: TheNone.py -t TOKENTokenBreaker: 1.TheNoneAlgorithmOptional Arguments:-h, --help show this help message and exitRequired Arguments:-t TOKEN, --token TOKENJWT Token valueExample Usage: python TheNone.py -t Output $ ./TheNone.py...
Pythem – Penetration Testing Framework
Pythem is a multi-purpose pentest framework written in Python. It has been developed to be used by security researchers and security professionals. The tool intended to be used only for acts within the law. I am not liable for any undue and unlawful act practiced by this tool, for more information, read the license. Linux Installation Dependenciesbuild-essentialpython-devpython-capstonelibnetfilter-queue-devlibffi-devlibssl-devtcpdump Dependencies Installation NOTE: Tested only with...
The Role of Digital Forensics in Solving Cyber Crimes
Your mobile app developers today have to understand more than simply putting together some code. They have to understand cybersecurity practices so that they can prevent their apps from being hacked and compromised. Criminals today have quickly realized that the internet has opened up some very rich pickings. From phishing emails to gather your personal data through to actual...
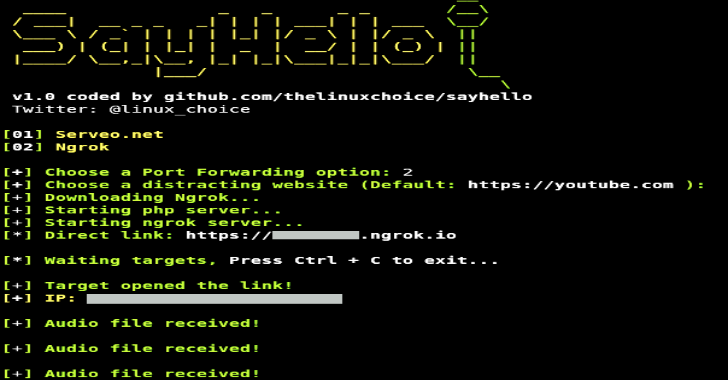
SAyHello – Capturing Audio (.Wav) From Target Using A Link
SAyHello is a tool used to capturing audio (.Wav) from target using a link. How it works? After the user grants microphone permissions, a website redirect button of your choice is released to distract the target while small audio files (about 4 seconds in wav format) are sent to the attacker. It uses Recorderjs, plugin for recording/exporting the output of Web...
Lynis 3.0.0 – Security Auditing Tool for Unix/Linux Systems
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next of simplification improvements we made. There is a risk of breaking your existing configuration.Lynis is an open source security auditing tool. Used by system administrators, security professionals, and auditors, to evaluate...