Gosec : Golang Security Checker To Inspects Source Code
Gosec is a inspects source code for security problems by scanning the Go AST. Licensed under the Apache License, Version 2.0 (the "License"). You may not use this file except in compliance with the License. You may obtain a copy of the License here. Install CI Installation # binary will be $GOPATH/bin/goseccurl -sfL https://raw.githubusercontent.com/securego/gosec/master/install.sh | sh -s -- -b $GOPATH/bin vX.Y.Z#...
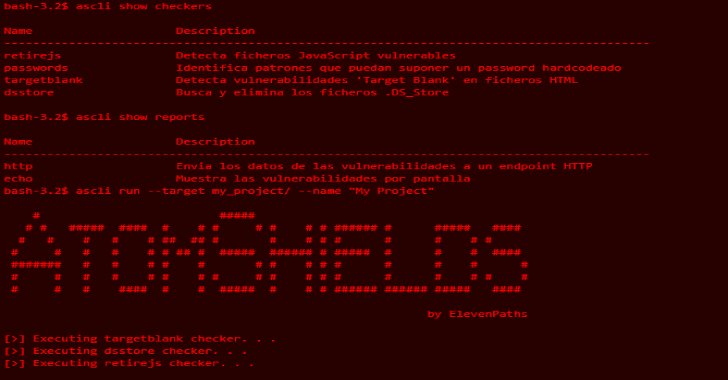
AtomShields CLI : Security Testing Framework For Repositories & Source Code
AtomShields Cli is a Command-Line Interface to use the software AtomShields. AtomShields is a security testing framework for repositories and source code. This system has different modules that detect different vulnerabilities or files that may expose a risk, and the results obtained can be obtained or sent thanks to the reporting modules. For developers: There is also the possibility to develop your...
Virtuailor : IDAPython Tool For Creating Automatic C++ Virtual Tables In IDA Pro
Virtuailor is an IDAPython tool that reconstructs vtables for C++ code written for intel architecture, both 32bit and 64bit code and AArch64 (New!). The tool constructed from 2 parts, static and dynamic. The first is the static part, contains the following capabilities: Detects indirect calls.Hooks the value assignment of the indirect calls using conditional breakpoints (the hook code). The second is the...
PESTO – PE (Files) Statistical Tool
PESTO is a Python script that extracts and saves in a database some PE file security characteristics or flags searching for every PE binary in a whole directory, and saving results in a database. PESTO checks for architecture flag in the header, and for the following security flags: ASLR, NO_SEH, DEP and CFG. Code is clear enough to modify flags...
What to Look for in the Right SOC Program – A Complete Guide
SOC stands for "security operations center", and it's important to every business, no matter what it's size. It doesn’t matter how big or small your business, everyone needs some kind of SOC program to keep everything secure, which means finding the right program for your needs. A very small business may use a few applications to keep systems and...
UBoat : HTTP Botnet Project
UBoat is a POC HTTP Botnet designed to replicate a full weaponised commercial botnet. What is a Botnet ? When the HTTP protocol was born in 1999, no one ever thought it will be used by one of the most dangerous Cyber threats called Botnet. A bot is an application that can perform and repeat a particular task faster than a...
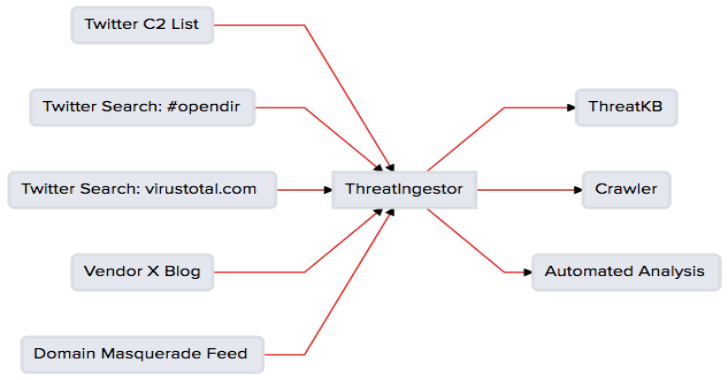
ThreatIngestor : Extract & Aggregate Threat Intelligence
ThreatIngestor is an extendable tool to extract and aggregate IOCs from threat feeds. Integrates out-of-the-box with ThreatKB and MISP, and can fit seamlessly into any existing worflow with SQS, Beanstalk, and custom plugins. Overview It can be configured to watch Twitter, RSS feeds, or other sources, extract meaningful information such as malicious IPs/domains and YARA signatures,...
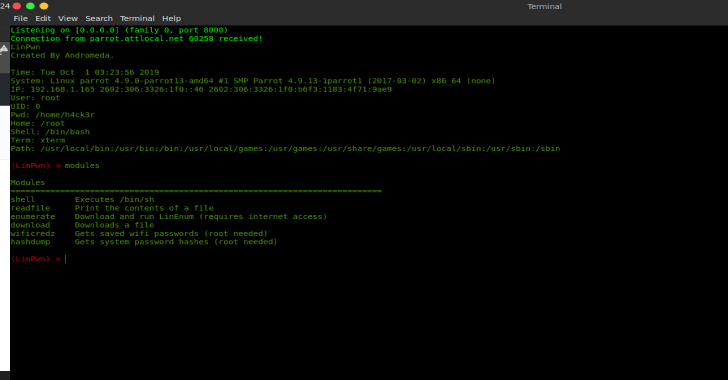
LinPwn : Interactive Post Exploitation Tool
LinPwn is a interactive tool created to assist you in post exploitation enumeration and privilege escalation. Connection Set your IP and port you want it to connect to in the Connection class.Place the LinPwn binary on the target machine.Run nc -lvp PORT on your machine and then run LinPwn on the target machine to get a connection. Also Read - JSONBee : A...
Pockint : A Portable OSINT Swiss Army Knife for DFIR/OSINT Professionals
POCKINT (a.k.a. Pocket Intelligence) is the OSINT swiss army knife for DFIR/OSINT professionals. Designed to be a lightweight and portable GUI program (to be carried within USBs or investigation VMs), it provides users with essential OSINT capabilities in a compact form factor: POCKINT's input box accepts typical indicators (URL, IP, MD5) and gives users...
XORpass : Encoder To Bypass WAF Filters Using XOR Operations
XORpass is an encoder to bypass WAF filters using XOR operations. Installation & Usage git clone https://github.com/devploit/XORpass cd XORpass $ php encode.php STRING $ php decode.php "XORed STRING" Example of bypass Using clear PHP function: Also Read - JSONBee : A Ready To Use JSONP Endpoints/Payloads To Help Bypass Content Security Policy Of Different Websites Using XOR bypass of that function: $ php encode.php system...