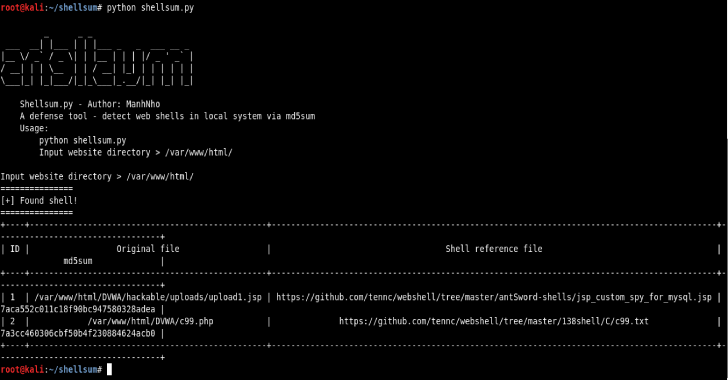
Shellsum : A Defense Tool – Detect Web Shells In Local Directories Via MD5Sum
Shellsum is a defense tool to detect web shells in local directories via md5sum. Following are some of the features of this tool; Fast speedLightweightBig databaseTabled output Usages Install git clone https://github.com/ManhNho/shellsum.gitchmod 755 -R shellsum/cd shellsum/pip install -r requirements.txt Also Read - Dwarf : Full Featured Multi Arch/OS Debugger Built On Top Of PyQt5 & Frida Run python shellsum.py ToDo Smooth outputExport file reportModularizationBigger database Download
BackBox Linux 6.0 – Ubuntu-Based Linux Distribution Penetration Test & Security Assessment
BackBox is a Linux distribution based on Ubuntu. It has been developed to perform penetration tests and security assessments. Designed to be fast, easy to use and provide a minimal yet complete desktop environment, thanks to its own software repositories, always being updated to the latest stable version of the most used and best known...
RedGhost : Linux Post Exploitation Framework Designed To Assist Red Teams In Gaining Persistence, Reconnaissance & Leaving No Trace
RedGhost is a Linux post exploitation framework designed to assist red teams in persistence, reconnaissance, privilege escalation and leaving no trace. Payloads Function to generate various encoded reverse shells in netcat, bash, python, php, ruby, perl SudoInject Function to inject sudo command with wrapper function to run a reverse root shell everytime "sudo" is run for privilege escalataion lsInject Function to...
UACME : Defeating Windows User Account Control
UACMe is a defeating windows user account control by abusing built-in windows autoElevate backdoor. System Requirements x86-32/x64 Windows 7/8/8.1/10 (client, some methods however works on server version too).Admin account with UAC set on default settings required. Usage Run executable from command line: akagi32 or akagi64 . See "Run examples" below for more info. First param is number of method to...
JShielder : Hardening Script for Linux Servers/ Secure LAMP-LEMP Deployer/ CIS Benchmark G
JSHielder is an Open Source Bash Script developed to help SysAdmin and developers secure there Linux Servers in which they will be deploying any web application or services. This tool automates the process of installing all the necessary packages to host a web application and Hardening a Linux server with little interaction from the...
iKy : OSINT Project To Collect Information From Mail
Project iKy is a tool that collects information from an email and shows results in a nice visual interface. We want to warn you that we have changed the Frontend from AngularJS to Angular 7. For this reason we left the project with AngularJS as Frontend in the iKy-v1 branch. The reason of changing the Frontend was to update the technology...
Passpie : Multiplatform Command-line Password Manager
Passpie is a command line tool to manage passwords from the terminal with a colorful and configurable interface. Use a master passphrase to decrypt login credentials, copy passwords to clipboard, syncronize with a git repository, check the state of your passwords, and more. Password files are encrypted using GnuPG and saved into yaml text files. Passpie supports Linux, OSX and Windows. What does it look like? Here...
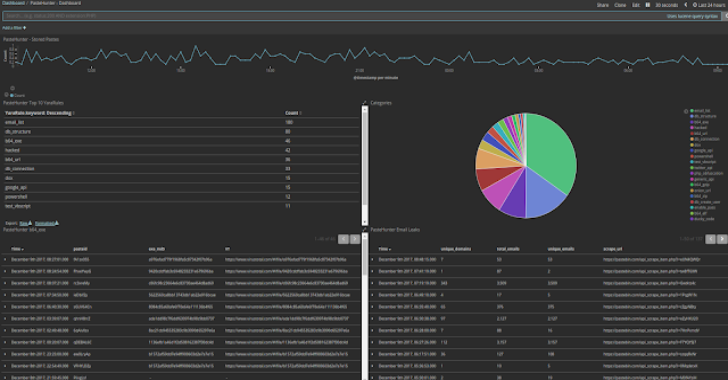
PasteHunter : Scanning Pastebin With Yara Rules
PasteHunter is a python3 application that is designed to query a collection of sites that host publicly pasted data. For all the pastes it finds it scans the raw contents against a series of Yara rules looking for information that can be used by an organisation or a researcher. Installation There are a few ways to install Local Installation Pastehunter If you want...
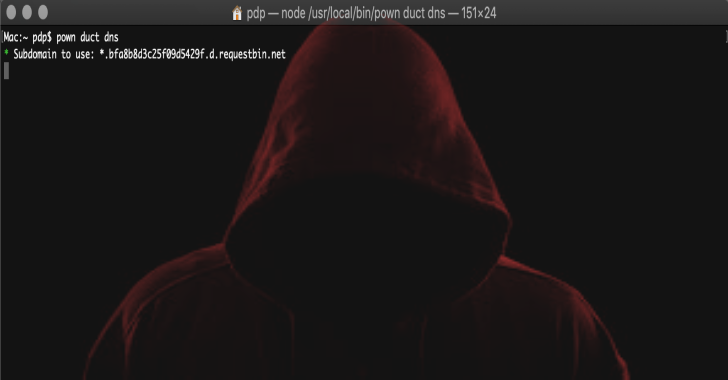
Pown Duct : Essential Tool For Finding Blind Injection Attacks
Pown Duct is an essential tool for finding blind injection attacks using DNS side-channels. This tool is part of secapps.com open-source initiative. Note : This tool is taking advantage of http://requestbin.net service. Future versions will use a dedicated, custom-built infrastructure. Quickstart This tool is meant to be used as part of Pown.js but it can be invoked separately as an independent tool. Install Pown first...
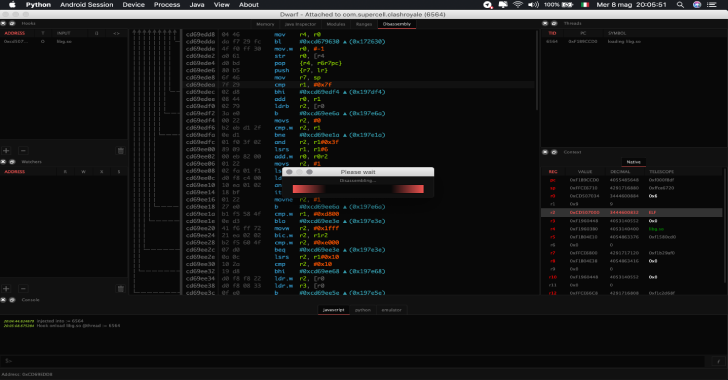
Dwarf : Full Featured Multi Arch/OS Debugger Built On Top Of PyQt5 & Frida
Dwarf is a debugger for reverse engineers, crackers and security analyst. Or you can call it damn, why are raspberries so fluffy or yet, duck warriors are rich as fuck. Whatever you like! Built on top of pyqt5, frida and some terrible code. Features breakpointswatchpoints without hardware supportvisual emulation with auto map from target, reporting memory accessesbreaks module loading cycle, java...