Windows Hacks : Creative & Unusual Things That Can Be Done With The Windows API
Windows Hacks is a creative and unusual things that can be done with the Windows API. Shrinking Windows Any window can be shrunk down. Shrinking the Calculator: Shrinking Google Chrome: Even Microsoft Word is not safe from being shrunk: Also Read - Simplify : Generic Android Deobfuscator Hue Shifter Any window can be selected to have its colors shifted. Hue shifting Microsoft Paint: Hue shifting Microsoft Word: Writing Directly To...
SwiftMonkey : A Framework For Doing Randomised UI Testing Of iOS Apps
SwiftMonkey project is a framework for generating randomised user input in iOS apps. This kind of monkey testing is useful for stress-testing apps and finding rare crashes. It also contains a related framework called SwiftMonkeyPaws, which provides visualisation of the generated events. This greatly increases the usefulness of your randomised testing, as you can see what touches caused any crash...
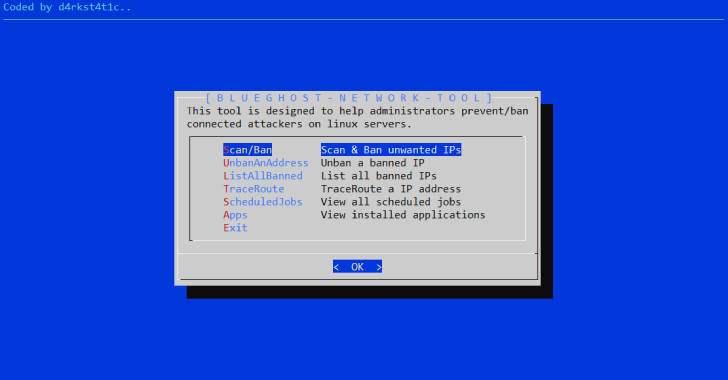
BlueGhost : Network Tool Designed To Assist Blue Teams In Banning Attackers From Linux Servers
BlueGhost tool utilises various Linux network tools and bash scripting to assist blue teams on defending Debian and Ubuntu based servers from malicious attackers. Scan/Ban shows connected IPs, scans IP addresses for open ports using nmap and whois search to gather reconnaissance on connected IPs, shows activity on the system, checks abuseipdb.com for reports and offers a ban function...
Simplify : Generic Android Deobfuscator
Simplify virtually executes an app to understand its behaviour and then tries to optimise the code so that it behaves identically but is easier for a human to understand. Each optimisation type is simple and generic, so it doesn't matter what the specific type of obfuscation is used. Before and After The code on the left is a decompilation of an...
WhatBreach : OSINT Tool To Find Breached Emails & Databases
WhatBreach is a tool to search for breached emails and their corresponding database. It takes either a single email or a list of emails and searches them leveraging haveibeenpwned.com's API, from there (if there are any breaches) it will search for the query link on Dehashed pertaining to the database, and output all breaches...
BoomER : Framework For Exploiting Local Vulnerabilities
BoomER is an open source framework, developed in Python. The tool is focused on post-exploitation, with a main objective, the detection and exploitation of local vulnerabilities, as well as the collection of information from a system, such as the installed applications they have. The framework allows the extension by third parties, through the development of modules, for...
Sliver : Implant Framework
Sliver is a general purpose cross-platform implant framework that supports C2 over Mutual-TLS, HTTP(S), and DNS. Implants are dynamically compiled with unique X.509 certificates signed by a per-instance certificate authority generated when you first run the binary. The server, client, and implant all support MacOS, Windows, and Linux (and possibly every Golang compiler target but we've...
MozDef: Mozilla Enterprise Defense Platform
The inspiration for MozDef comes from the large arsenal of tools available to attackers. Suites like metasploit, armitage, lair, dradis and others are readily available to help attackers coordinate, share intelligence and finely tune their attacks in real time. Defenders are usually limited to wikis, ticketing systems and manual tracking databases attached to the end of a Security Information...
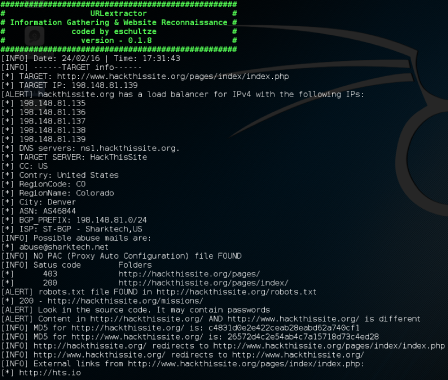
URLextractor : Information Gathering & Website Reconnaissance
URLextractor is a tool for Information Gathering & Website Reconnaissance. Following are some of the features of this tool; IP and hosting info like city and country (using FreegeoIP)DNS servers (using dig)ASN, Network range, ISP name (using RISwhois)Load balancer testWhois for abuse mail (using Spamcop)PAC (Proxy Auto Configuration) fileCompares hashes to diff coderobots.txt (recursively looking for hidden stuff)Source code (looking for passwords and users)External...
BackBox : Tool To Perform Penetration Tests & Security Assessments
BackBox is a Linux distribution based on Ubuntu. It has been developed to perform penetration tests and security assessments. Designed to be fast, easy to use and provide a minimal yet complete desktop environment, thanks to its own software repositories, always being updated to the latest stable version of the most used and best known ethical hacking tools. ...