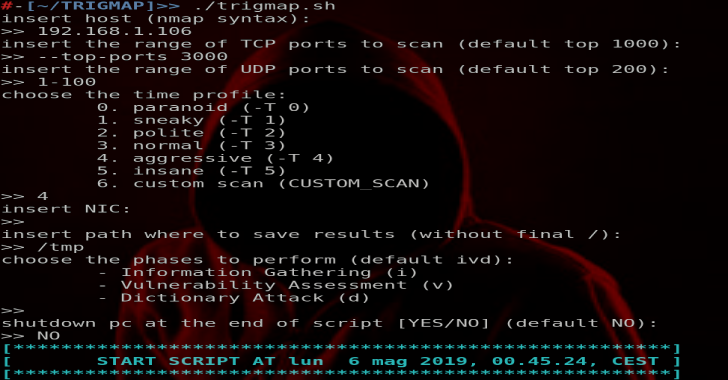
TrigMap : A Wrapper For Nmap To Automate The Pentest
Trigmap is a wrapper for Nmap. You can use it to easily start Nmap scan and especially to collect information into a well organised directory hierarchy. The use of Nmap makes the script portable (easy to run not only on Kali Linux) and very efficient thanks to the optimised Nmap algorithms. Trigmap can performs several tasks using Nmap scripting...
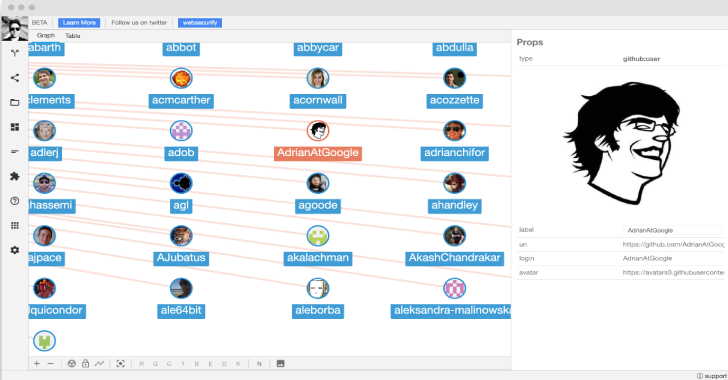
Pown Recon : A Powerful Target Reconnaissance Framework Powered By Graph Theory
Pown Recon is a target reconnaissance framework powered by graph theory. The benefit of using graph theory instead of flat table representation is that it is easier to find the relationships between different types of information which comes quite handy in many situations. Graph theory algorithms also help with diffing, searching, like finding the shortest...
LNK-KISSER : AutoIt HackTool, Shortcuts.lnk Payloads Generator
LNK-KISSER is an autoIt hackTool, shortcuts.lnk payloads generator. Exploiting Powershell to make ShortCut Payloads .There is too much of awsome tricks there , u can make it better ^_^.For Ex : Killing tcpview , taskmanager ..etc while downloading.Set hidden attribs to the malware after downloading....etcG00d by3../9aylas Also Read - Horn3t : Powerful Visual Subdomain Enumeration at the Click of a Mouse Download
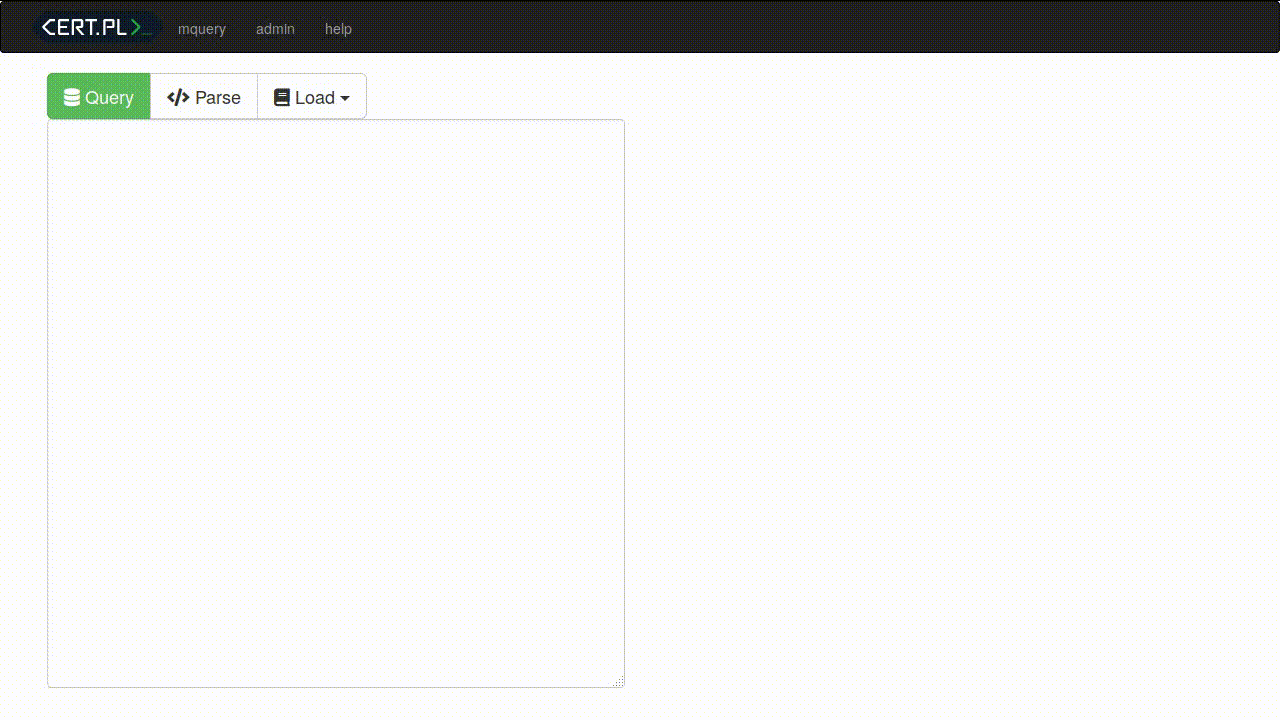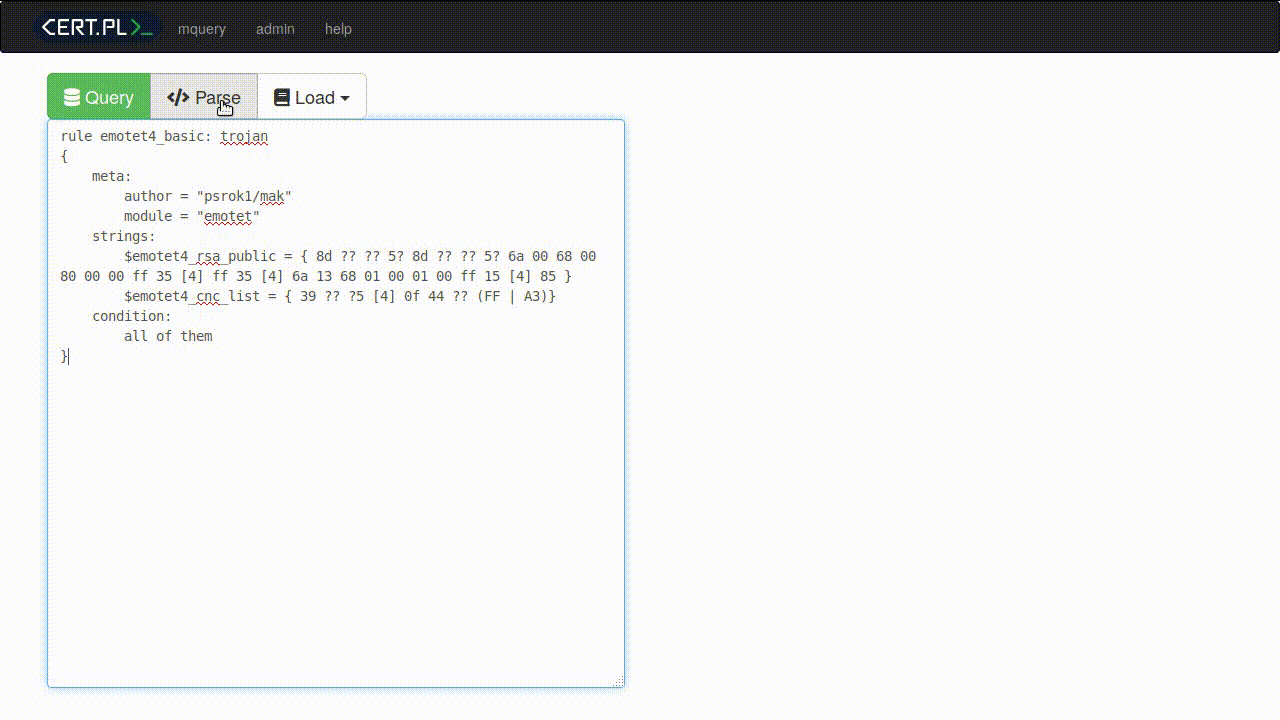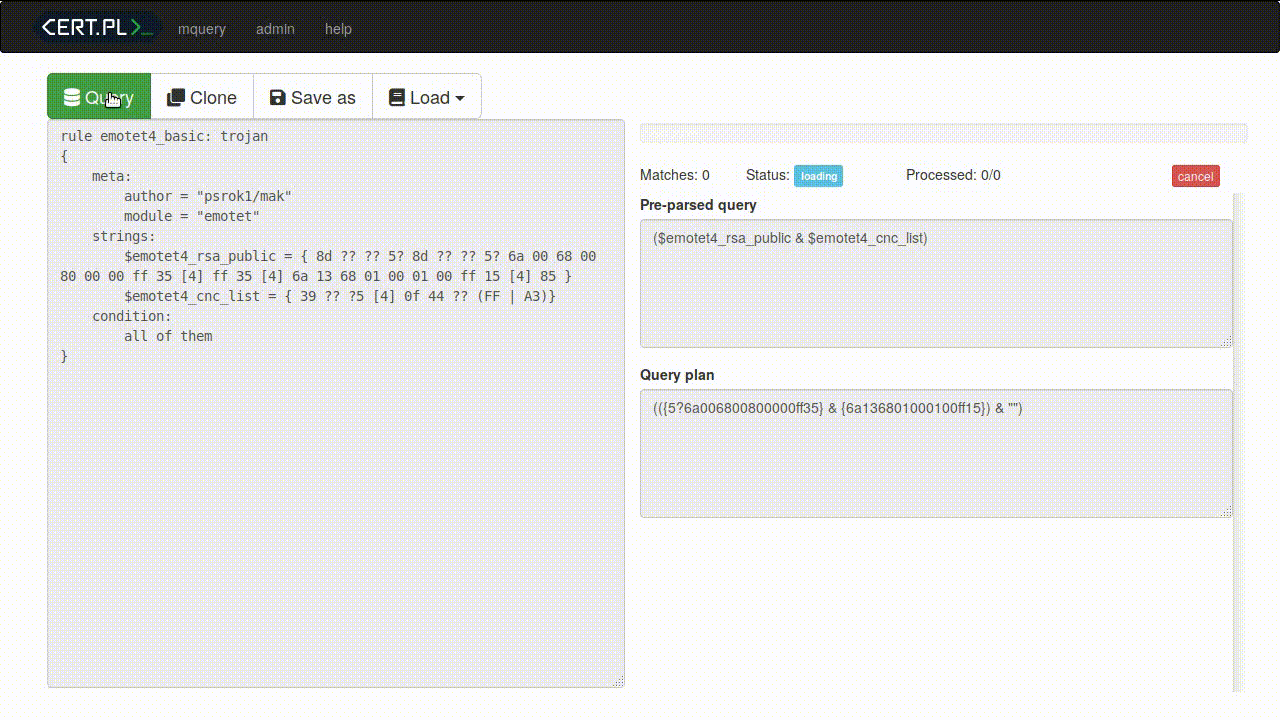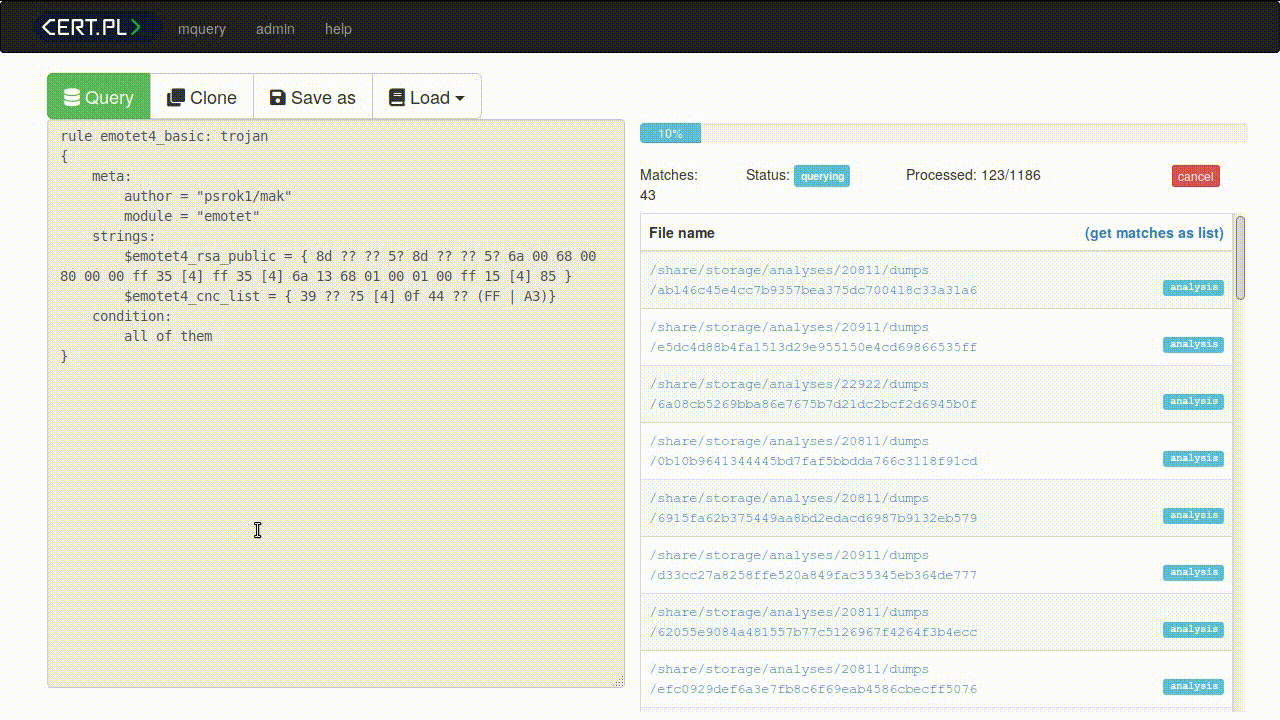
Mquery : YARA Malware Query Accelerator
Mquery can be used to search through terabytes of malware in a blink of an eye: Ever had trouble searching for particular malware samples? Our project is an analyst-friendly web GUI to look through your digital warehouse. Demo Take a look at https://mquery.tailcall.net for a quick demo. Unfortunately, you won't find any actual malware there. For demo purposes we have indexed...
Ph0neutria : Malware Zoo Builder That Sources Samples Straight From The Wild
Ph0neutria is a malware zoo builder that sources samples straight from the wild. Everything is stored in Viper for ease of access and manageability. It aims to: Limit the scope of crawling to only frequently updated and reliable sources.Maximise the effectiveness of individual indicators.Offer a single, reliable and well organised storage mechanism.Not do work that can instead be done by Viper. What...
Ustealer : Steal Ubuntu Information In Local PC
Ustealer is a Ubuntu stealer, steal Ubuntu information in local PC. This tool is always good to go with the USB key. Requirements G++ sudo apt-get install g++ libsqlite3 sudo apt-get install libsqlite3-dev Compilation Go in Ustealer/ folder and run makefile make Also Read - PacBot : Platform For Continuous Compliance & Security Automation For The Cloud Usage ./ustealer Download
Pe-Sieve : Recognizes & Dumps A Variety Of Potentially Malicious Implants
PE-sieve is a light-weight tool that helps to detect malware running on the system, as well as to collect the potentially malicious material for further analysis. Recognizes and dumps variety of implants within the scanned process: replaced/injected PEs, shellcodes, hooks, and other in-memory patches. Detects inline hooks, Process Hollowing, Process Doppelgänging, Reflective DLL Injection, etc. Also Read - OSINT-SPY : Performs OSINT...
Horn3t : Powerful Visual Subdomain Enumeration at the Click of a Mouse
Horn3t is your number one tool for exploring subdomains visually. Tested on Windows 10 and Debian with Google Chrome/Chromium 73. Recon your targets at blazing speedEnhance your productivity by focusing on interesting looking sitesEnumerate critical sites immediatelySting your target Building on the great Sublist3r framework (or extensible with your favorite one) it searches for subdomains and generates awesome picture previews. Get a fast overview of...
PacBot : Platform For Continuous Compliance & Security Automation For The Cloud
PacBot is a platform for continuous compliance monitoring, compliance reporting and security automation for the cloud. In PacBot, security and compliance policies are implemented as code. All resources discovered by PacBot are evaluated against these policies to gauge policy conformance. The PacBot auto-fix framework provides the ability to automatically respond to policy violations by taking predefined actions. PacBot...
OSINT-SPY : Performs OSINT Scan On Email/Domain/IP_Address/Organisation
Performs OSINT scan on email/domain/ip_address/organization using OSINT-SPY. It can be used by Data Miners, Infosec Researchers, Penetration Testers and cyber crime investigator in order to find deep information about their target. Overview Of This Tool Perform scan on IP Address / domain / email address / BTC(bitcoin) address / deviceFind out latest bitcoin block informationList out all the ciphers supported...