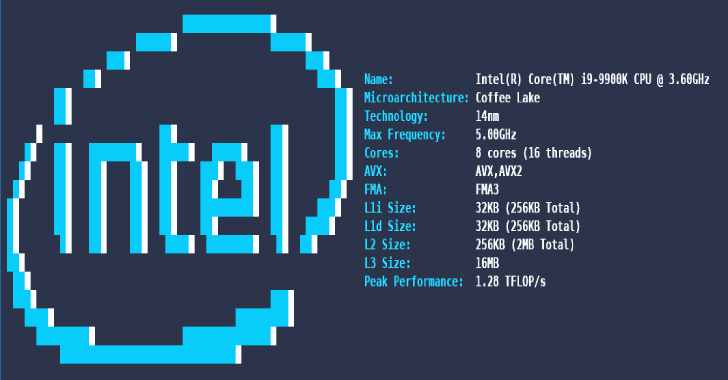
CPUFetch is a simple yet fancy CPU architecture fetching tool. Support cpufetch supports x86, x86_64 (Intel and AMD) and ARM. Platform x86_64 ARM Notes GNU/Linux ✔️ ✔️ Best support Windows ✔️ ❌ Some information may be missing.Colors will be used if supported Android ❗ ✔️ Some information may be missing.Not tested under x86_64 macOS ✔️ …
Continue reading “CPUFetch : Simplistic Yet Fancy CPU Architecture Fetching Tool”