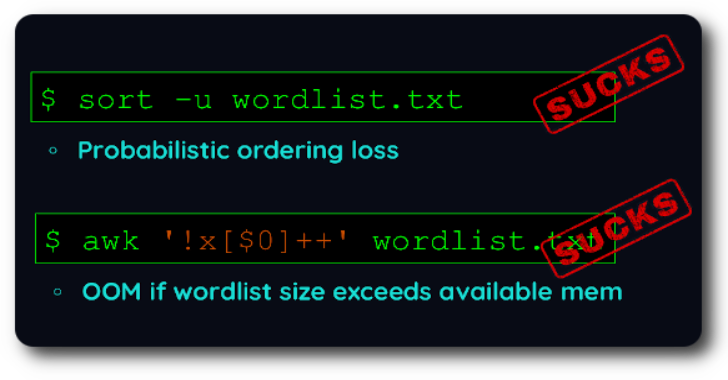
Duplicut is a modern password wordlist creation usually implies concatenating multiple data sources. Ideally, most probable passwords should stand at start of the wordlist, so most common passwords are cracked instantly. With existing dedupe tools you are forced to choose if you prefer to preserve the order OR handle massive wordlists. Unfortunately, wordlist creation requires both: So i wrote duplicut in highly …
Continue reading “Duplicut : Remove Duplicates From MASSIVE Wordlist, Without Sorting It”