AngrgDB use angr inside GDB. Create an angr state from the current debugger state. Install pip install angrgdb echo “python import angrgdb.commands” >> ~/.gdbinit Usage AngrgDB implements the angrdbg API in GDB. You can use it in scripts like this: from angrgdb import * gdb.execute(“b *0x004005f9”)gdb.execute(“r aaaaaaaa”) sm = StateManager()sm.sim(sm[“rax”], 100) m = sm.simulation_manager()m.explore(find=0x00400607, avoid=0x00400613) …
Tag Archives: GDB
Pylane : An Python VM Injector With Debug Tools, Based On GDB
Pylane is a python vm injector with debug tools, based on gdb and ptrace. Pylane uses gdb to trace python process, inject and run some code in its python vm. Usage use inject command to inject a python script in an process: pylane inject <PID><YOUR_PYTHON_FILE>+ Also Read – Lazyrecon : Automate Your Reconnaissance Process In …
Continue reading “Pylane : An Python VM Injector With Debug Tools, Based On GDB”
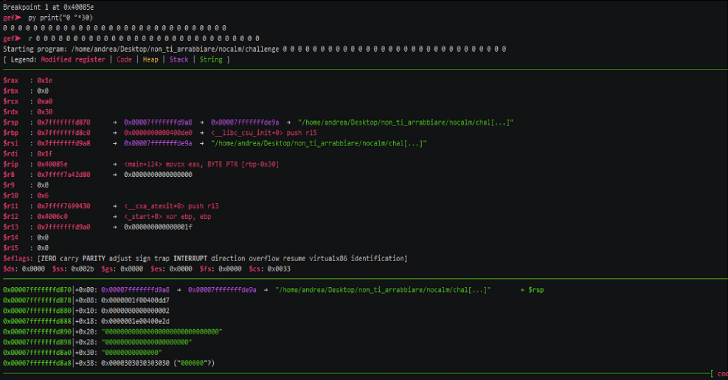
Peda – Python Exploit Development Assistance for GDB
PEDA is a python exploit development assistance for GDB. Features Enhance the display of gdb: colorize and display disassembly codes, registers, memory information during debugging. Add commands to support debugging and exploit development (for a full list of commands use peda help): aslr — Show/set ASLR setting of GDB checksec — Check for various security …
Continue reading “Peda – Python Exploit Development Assistance for GDB”