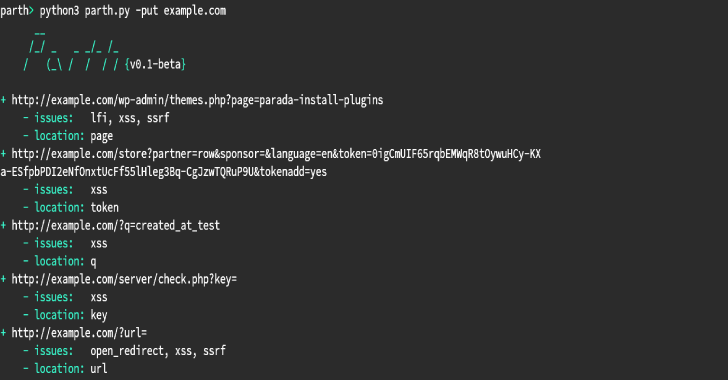
Some HTTP parameter names are more commonly associated with one functionality than the others. For example, the parameter ?url= usually contains URLs as the value and hence often falls victim to file inclusion, open redirect and SSRF attacks. Parth can go through your burp history, a list of URLs or it’s own disocovered URLs to …
Continue reading “Parth : Heuristic Vulnerable Parameter Scanner”