Erlik 2 is a vulnerable Flask Web App. It is a lab environment created for people who want to improve themselves in the field of web penetration testing. Features It contains the following vulnerabilities. -HTML Injection-XSS-SSTI-SQL Injection-Information Disclosure-Command Injection-Brute Force-Deserialization-Broken Authentication-DOS-File Upload Installation git clone https://github.com/anil-yelken/Vulnerable-Flask-Appcd Vulnerable-Flask-Appsudo pip3 install -r requirements.txt Usage python3 vulnerable-flask-app.py
Tag Archives: Vulnerable
Erlik : Vulnerable Soap Service
Erlik is a vulnerable SOAP web service. It is a lab environment created for people who want to improve themselves in the field of web penetration testing. Features It contains the following vulnerabilities. -LFI -SQL Injection -Informaion Disclosure -Command Inejction -Brute Force -Deserialization Installation git clone https://github.com/anil-yelken/Vulnerable-Soap-Service cd Vulnerable-Soap-Service sudo pip3 install requirements.txt Usage sudo python3 …
TerraGoat : Vulnerable Terraform Infrastructure
TerraGoat is Bridgecrew’s “Vulnerable by Design” Terraform repository. TerraGoat is a learning and training project that demonstrates how common configuration errors can find their way into production cloud environments. Introduction TerraGoat was built to enable DevSecOps design and implement a sustainable misconfiguration prevention strategy. It can be used to test a policy-as-code framework like Bridgecrew & Checkov, inline-linters, …
Continue reading “TerraGoat : Vulnerable Terraform Infrastructure”
Log4J-Detector : Detects Log4J versions on your file-system within any application that are vulnerable to CVE-2021-44228 and CVE-2021-45046
Log4J-Detector is a Scanner that detects vulnerable Log4J versions to help teams assess their exposure to CVE-2021-44228 (CRITICAL), CVE-2021-45046, CVE-2021-45105, and CVE-2021-44832. Can search for Log4J instances by carefully examining the complete file-system, including all installed applications. It is able to find Log4J instances that are hidden several layers deep. Works on Linux, Windows, and Mac, and everywhere else Java …
Allsafe : Intentionally Vulnerable Android Application
Allsafe is an intentionally vulnerable application that contains various vulnerabilities. Unlike other vulnerable Android apps, this one is less like a CTF and more like a real-life application that uses modern libraries and technologies. Additionally, I have included some Frida based challenges for you to explore. Have fun and happy hacking! Useful Frida Scripts I …
Continue reading “Allsafe : Intentionally Vulnerable Android Application”
Regexploit : Find Regular Expressions Which Are Vulnerable To ReDoS (Regular Expression Denial Of Service)
Regexploit a tool to Find regexes which are vulnerable to Regular Expression Denial of Service (ReDoS). More info on the Doyensec blog Regexploit: DoS-able Regular Expressions When thinking of Denial of Service (DoS), we often focus on Distributed Denial of Service (DDoS) where millions of zombie machines overload a service by launching a tsunami of data. …
Damn Vulnerable GraphQL Application
Damn Vulnerable GraphQL Application is an intentionally vulnerable implementation of Facebook’s GraphQL technology, to learn and practice GraphQL Security. About DVGA Damn Vulnerable GraphQL is a deliberately weak and insecure implementation of GraphQL that provides a safe environment to attack a GraphQL application, allowing developers and IT professionals to test for vulnerabilities. DVGA has numerous …
Fawkes : Tool To Search For Targets Vulnerable To SQL Injection
Fawkes is a tool to search for targets vulnerable to SQL Injection. Performs the search using Google search engine. Options -q, –query – Dork that will be used in the search engine.-r, –results – Number of results brought by the search engine.-s, –start-page – Home page of search results.-t, –timeout – Timeout of requests.-v, –verbose …
Continue reading “Fawkes : Tool To Search For Targets Vulnerable To SQL Injection”
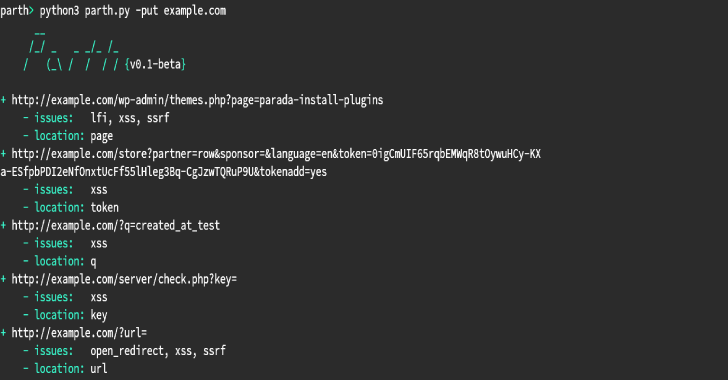
Parth : Heuristic Vulnerable Parameter Scanner
Some HTTP parameter names are more commonly associated with one functionality than the others. For example, the parameter ?url= usually contains URLs as the value and hence often falls victim to file inclusion, open redirect and SSRF attacks. Parth can go through your burp history, a list of URLs or it’s own disocovered URLs to …
Continue reading “Parth : Heuristic Vulnerable Parameter Scanner”
OpenRelayMagic : Tool To Find SMTP Servers Vulnerable To Open Relay
OpenRelayMagic is a tool to test for vulnerable open relays on SMTP servers. Features Check single target/ domain list Port 587 and 465 Implemented Multithreaded Also Read – Pytm : A Pythonic Framework For Threat Modeling