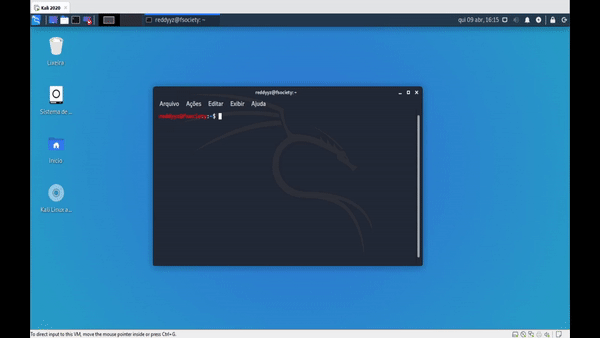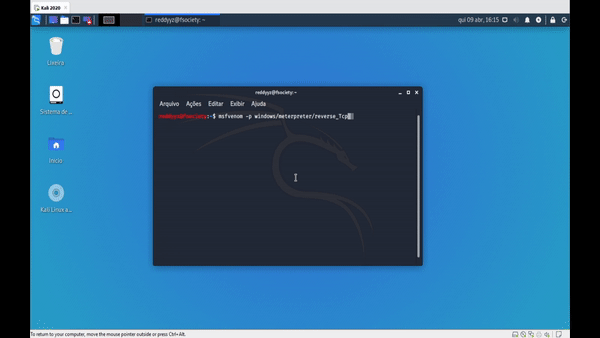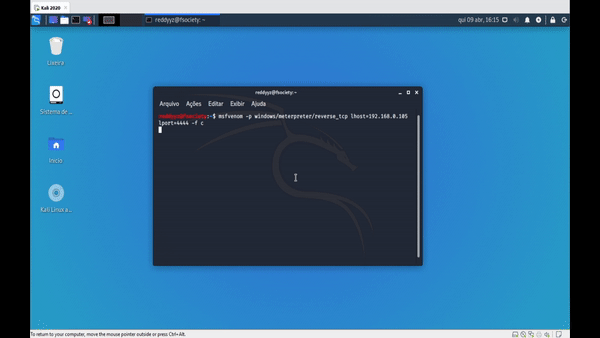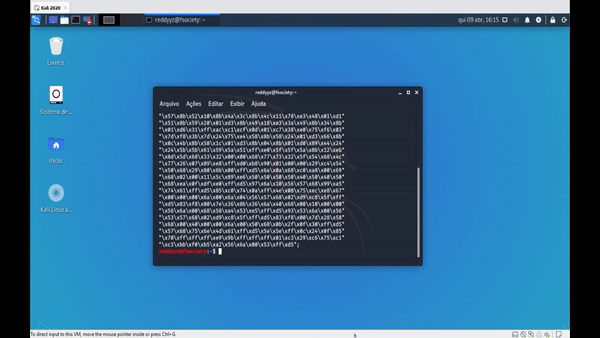
APPLICATIONS
HOT NEWS
Assless-Chaps : Crack MSCHAPv2 Challenge/Responses Quickly Using A Database Of NT...
Assless-CHAPs is an efficient way to recover the NT hash used in a MSCHAPv2/NTLMv1 exchange if you have the challenge and response (e.g. from...
© kalilinuxtutorials.com 2025









.png)
.png)