UBoat HTTP is a POC HTTP Botnet designed to replicate a full weaponized commercial botnet.
UBoat Uses
- Coded in C++ with no dependencies
- Encrypted C&C Communications
- Persistence to prevent your control being lost
- Connection Redundancy (Uses a fallback server address or domain )
- DDoS methods (TCP & UDP Flood)
- Task Creation System ( Altering system HWID,Country,IP,OS.System )
- Remote Commands
- Update and Uninstall other malware
- Download and Execute other malware
- Active as well as Passive Keylogger
- Enable Windows RDP
- Plugin system for easy feature updates
Download
Also Read WAF-Buster : Disrupt WAF by abusing SSL/TLS Ciphers
Installation
Bot Compilation
Change the URL’s in gate.h including the fallback domain if you are intending to use it
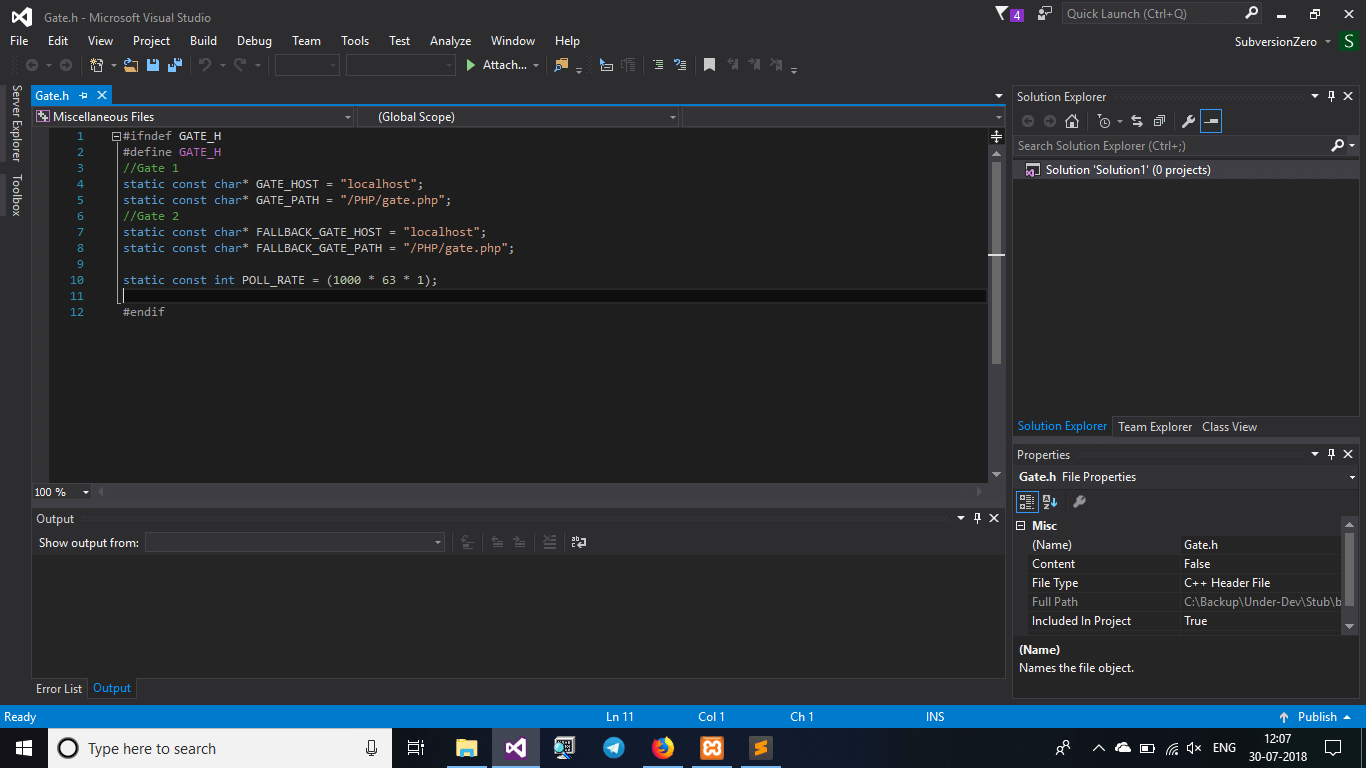
Panel Setup
Installation :
- Install lamp in unix / Xampp in Win Boxes
- You need PHP 7.0 strictly don’t complain later
- Install PMA because we are lazy ( thank me later )
Database Config :
- Make a database named ‘uboat’
- Rename uboat.sql located in /Panel/uboat.sql to uboat.sql.zip
- Now import uboat.sql.zip in PhpMyAdmin to the database uboat you created
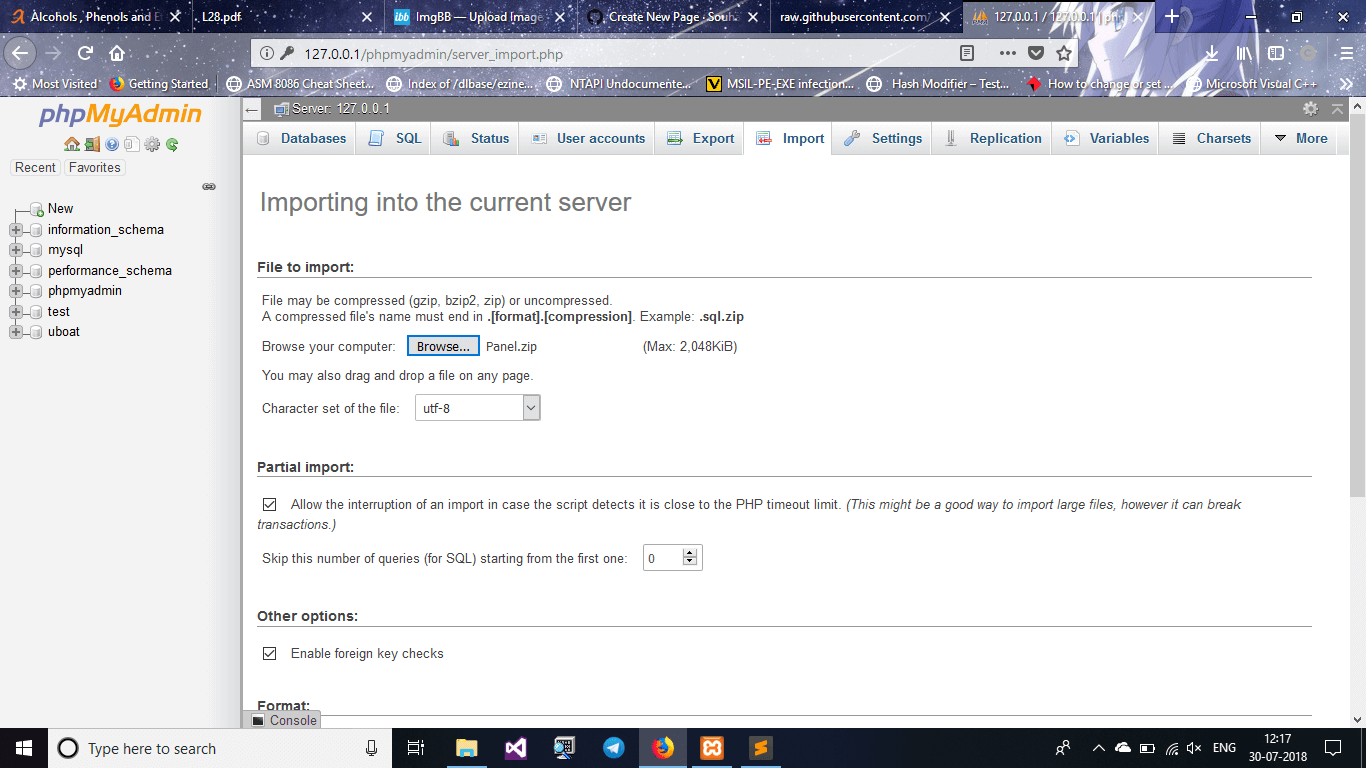
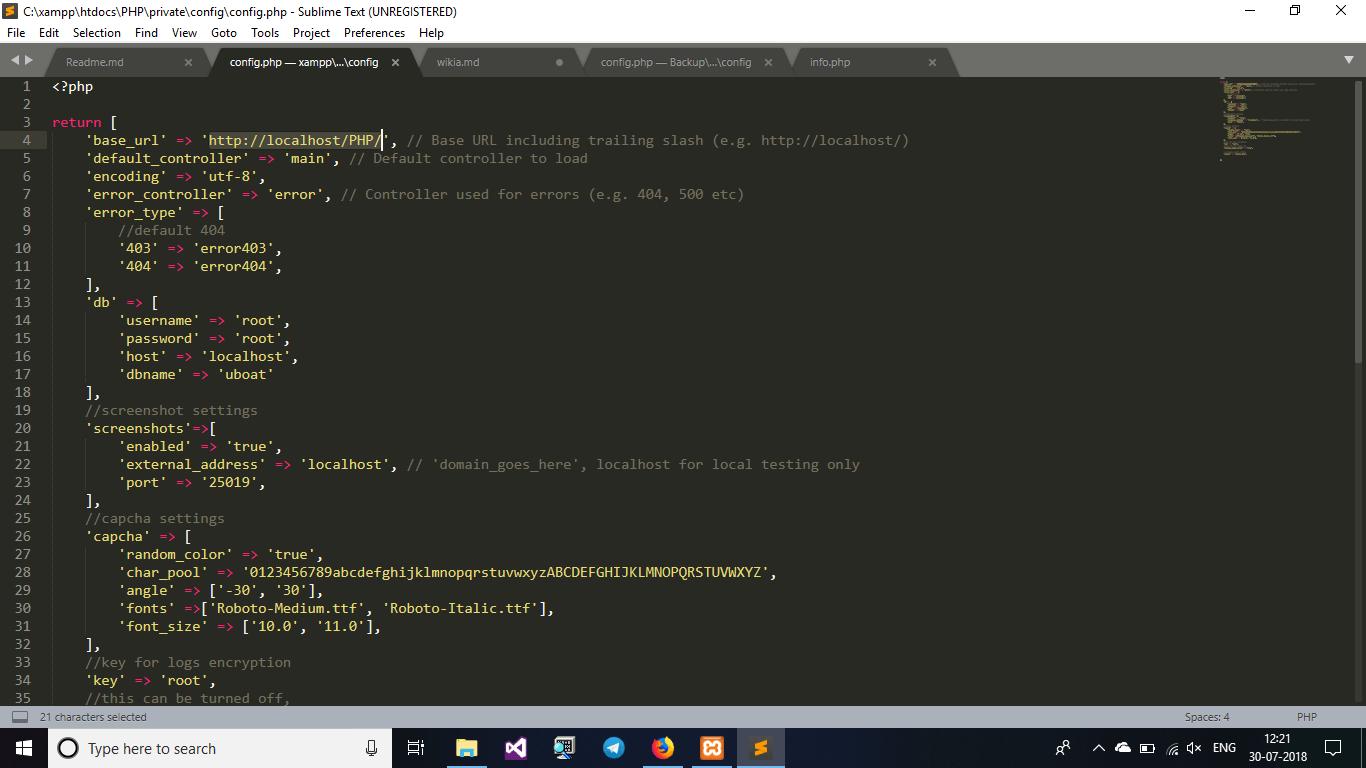
Panel Config :
- Locate /Panel/private/config/config.php
- Now edit it the url localhost/PHP/ with your C2 host url
** now look for the keyword “db” **
- username :- your mysql user
- password :- your mysql password
- host :- leave it as it is
- dbname :- It’s the database you created earlier remember ” uboat ” ?
Login Config :
Now choose a user/password credential for the login
- Say for example :-
- user :- root
- password :- root Kay ?
- For generating the password locate to /Panel/test.php
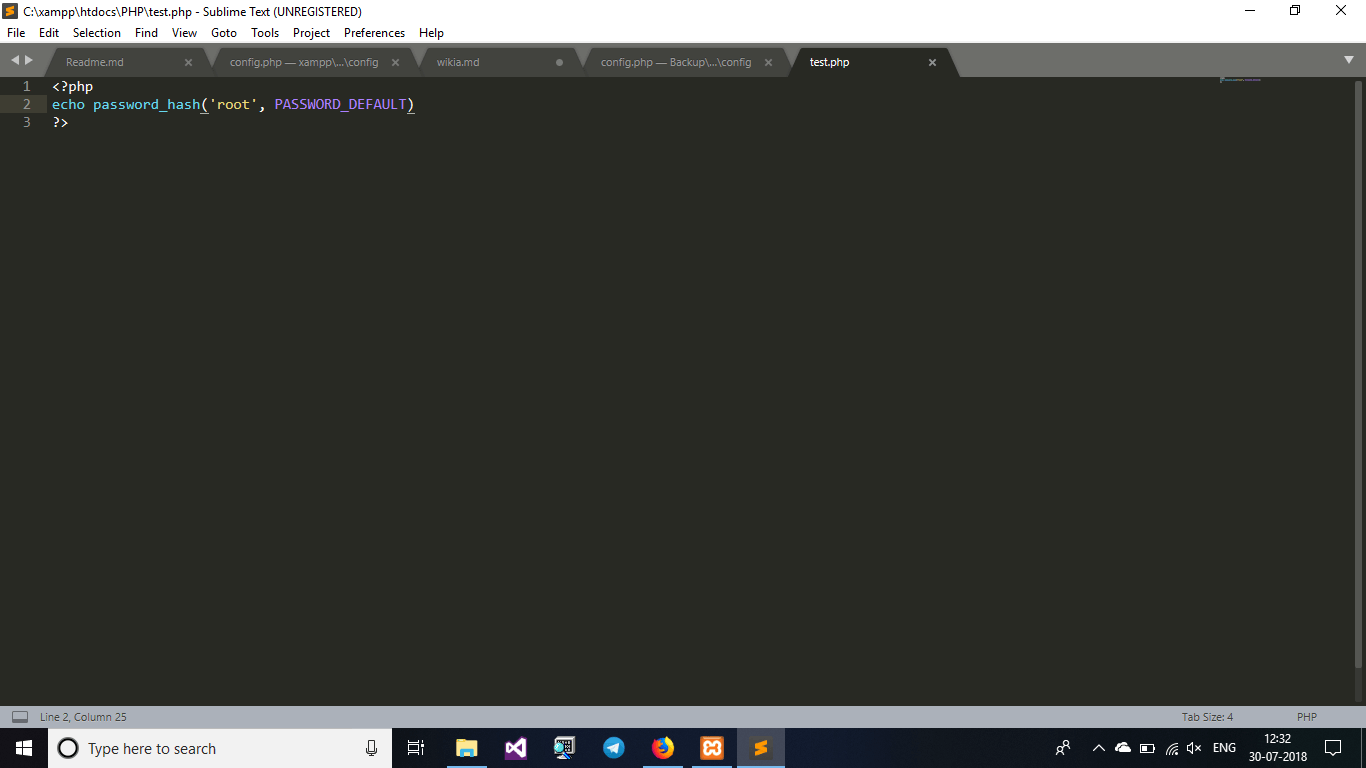
You can change the keyword root to your desired password We are using root since we chose to here :p
- Visit www.url.com/Panel/test.php from your browser and copy the generated hash
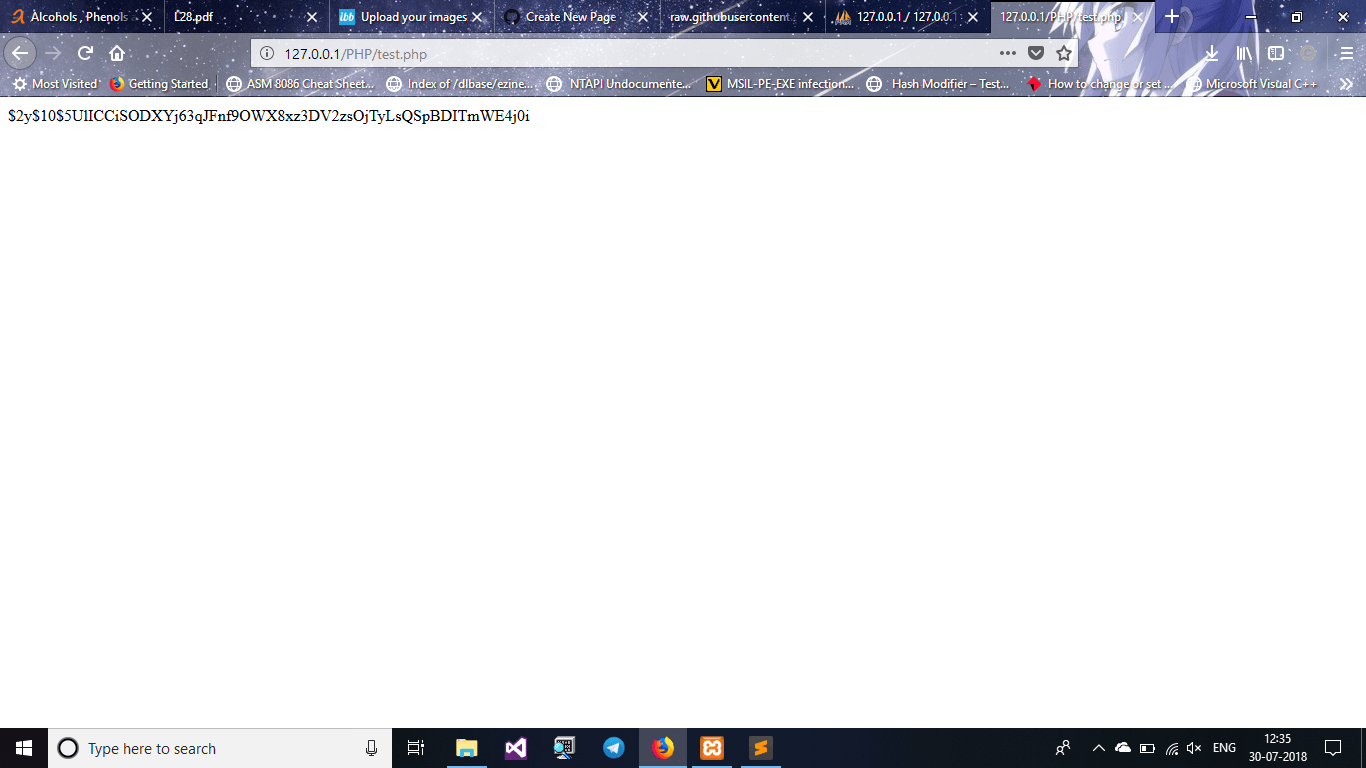
You are almost done !!
- Now open PhpMyAdmin and locate the table user in database you created uboat
- Change the hash in the password column
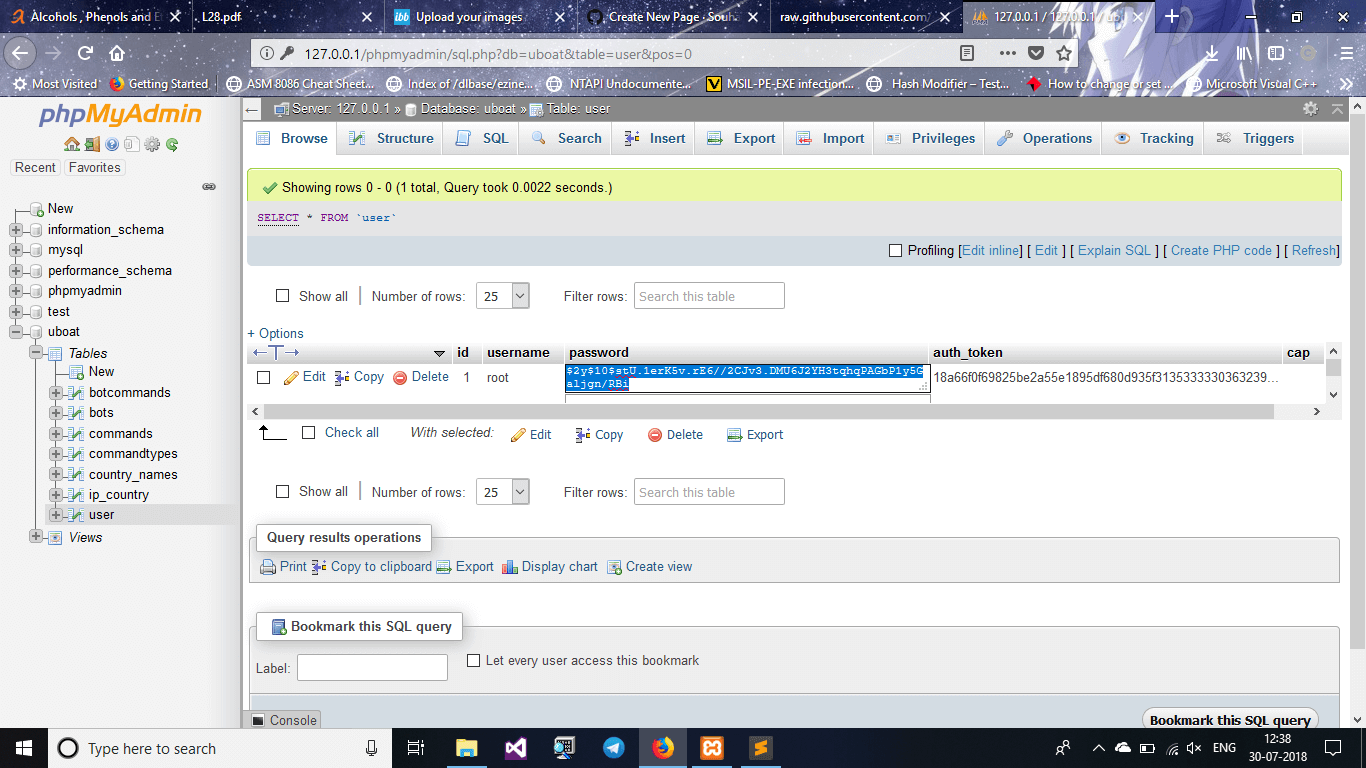
** Yay everything done **
- -> Now login by visiting http://url.com/Panel/login
Once you login you’ll get something like this
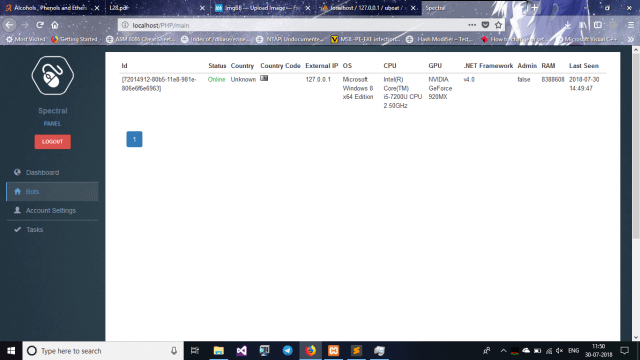
![]() Credit : Souhardya Sardar, Tuhinshubhra & Team Virtually Unvoid Defensive
Credit : Souhardya Sardar, Tuhinshubhra & Team Virtually Unvoid Defensive














