Wifiphisher is a security device that performs Wi-Fi programmed affiliation attack to drive wireless customers to unwittingly interface with an attacker-controlled Access Point. It is a maverick Access Point system that can be utilized to mount robotized casualty altered phishing assaults against WiFi customers keeping in mind the end goal to acquire qualifications or taint the casualties with malwares.
It can function as social designing attack instrument that not at all like different strategies it does exclude any brute driving. It is a simple route for getting accreditations from hostage gateways and outsider login pages (e.g. in informal communities) or WPA/WPA2 pre-shared keys to hack WiFi password behalf of WiFi Hacker to achieve this task.
Wifiphisher chips away at Kali Linux and is authorized under the GPL permit.
Also Read Best Hacking Tools List for Hackers & Security Professionals 2018
How wifiphisher works ?
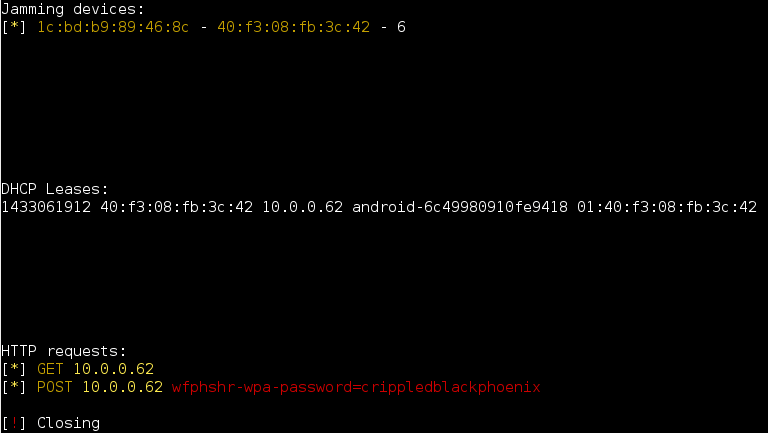
In the wake of accomplishing a man-in-the-middle position utilizing Wi-Fi programmed affiliation systems (counting “KARMA” and “Known Beacons” attacks), Wifiphisher of course diverts all HTTP solicitations to an attacker-controlled phishing page.
From the victim’s point of view, the assault makes use in three stages:
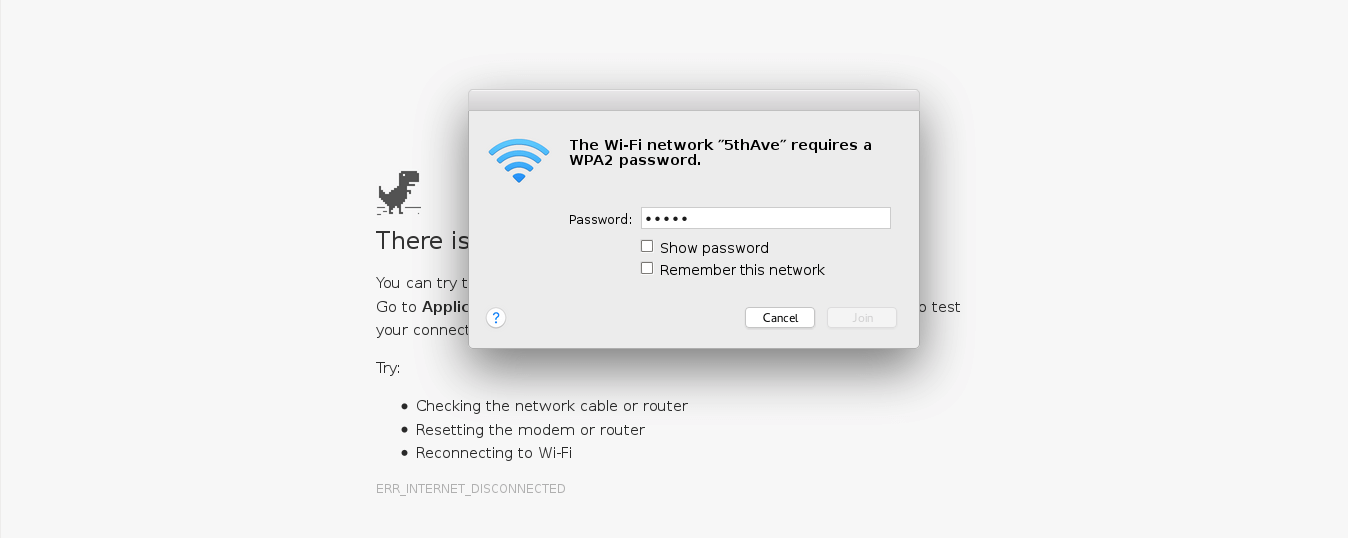
- Victim is being deauthenticated from her access point.
- Victim joins a rogue access point.
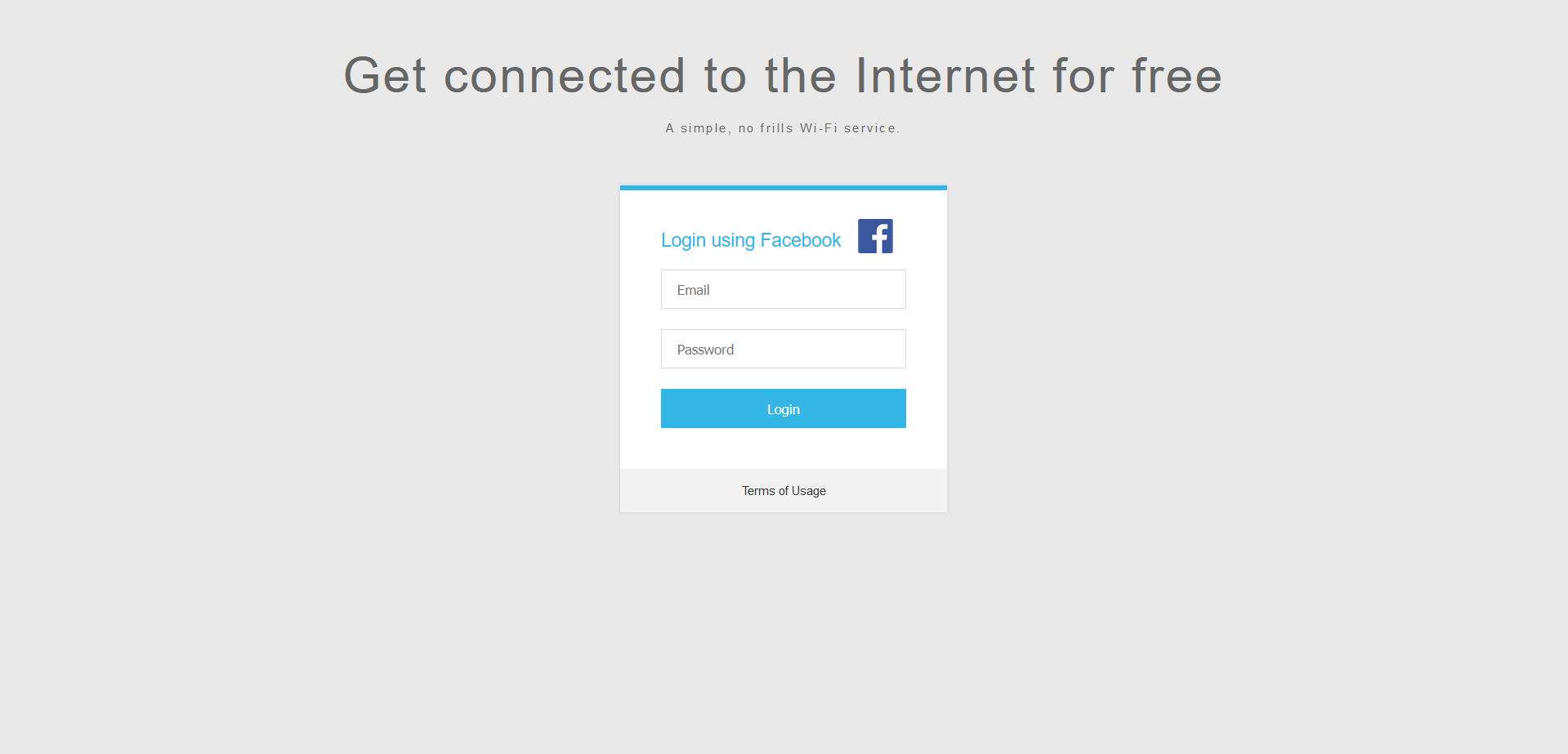
- Victim is being served a realistic specially-customized phishing page.

Installation of wifiphisher
To install the latest development version type the following commands:
git clone https://github.com/wifiphisher/wifiphisher.git # Download the latest revision
cd wifiphisher # Switch to tool's directory
sudo python setup.py install # Install any dependencies
Alternatively, you can download the latest stable version from the Releases page.
Following are all the options along with their descriptions (also available with wifiphisher -h):
Short form |
Long form |
Explanation |
|---|---|---|
| -h | –help | show this help message and exit |
| -eI EXTENSIONSINTERFACE | –extensionsinterface EXTENSIONSINTERFACE | Manually choose an interface that supports monitor mode for running the extensions. Example: -eI wlan1 |
| -aI APINTERFACE | –apinterface APINTERFACE | Manually choose an interface that supports AP mode for spawning an AP. Example: -aI wlan0 |
| -nJ | –noextensions | Do not load any extensions. |
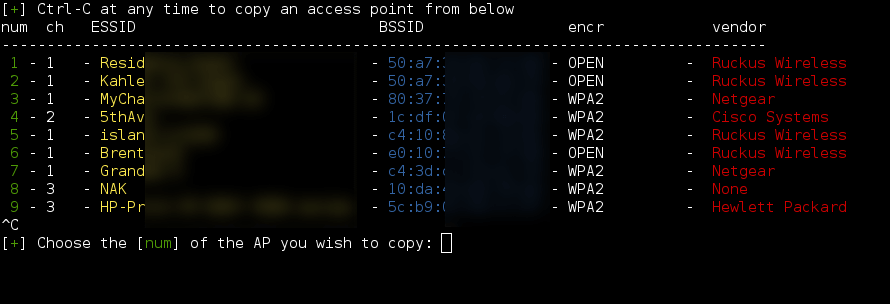
| -e ESSID | –essid ESSID | Enter the ESSID of the rogue Access Point. This option will skip Access Point selection phase. Example: –essid ‘Free WiFi’ |
| -p PHISHINGSCENARIO | –phishingscenario PHISHINGSCENARIO | Choose the phishing scenario to run.This option will skip the scenario selection phase. Example: -p firmware_upgrade |
| –pK PRESHAREDKEY | –presharedkey PRESHAREDKEY | Add WPA/WPA2 protection on the rogue Access Point. Example: -pK s3cr3tp4ssw0rd |
| -qS | –quitonsuccess | Stop the script after successfully retrieving one pair of credentials. |
| -lC | –lure10-capture | Capture the BSSIDs of the APs that are discovered during AP selection phase. This option is part of Lure10 attack. |
| -lE LURE10_EXPLOIT | –lure10-exploit LURE10_EXPLOIT | Fool the Windows Location Service of nearby Windows users to believe it is within an area that was previously captured with –lure10-capture. Part of the Lure10 attack. |
| -iAM | –mac-ap-interface | Specify the MAC address of the AP interface. Example: -iAM 38:EC:11:00:00:00 |
| -iEM | –mac-extensions-interface | Specify the MAC address of the extensions interface. Example: -iEM E8:2A:EA:00:00:00 |
| -iNM | –no-mac-randomization | Do not change any MAC address. |
| -hC | –handshake-capture | Capture of the WPA/WPA2 handshakes for verifying passphrase. Example: -hC capture.pcap |
| -dE | –deauth-essid | Deauth all the BSSIDs having same ESSID from AP selection or the ESSID given by -e option. |
| –logging | Enable logging. Output will be saved to wifiphisher.log file. | |
| -cM | –channel-monitor | Monitor if the target access point changes the channel. |
| –payload-path | Enable the payload path. Intended for use with scenarios that serve payloads. | |
| -wP | –wps-pbc | Monitor if the button on a WPS-PBC Registrar side is pressed. |
| -wAI | –wpspbc-assoc-interface | The WLAN interface used for associating to the WPS AccessPoint. |
| -kb | –known-beacons | Perform the known beacons Wi-Fi automatic association technique. |
| -fH | –force-hostapd | Force the usage of hostapd installed in the system. |
Screenshots

Credits
The script is based on an idea from Dan McInerney back in 2015.
A full list of contributors lies here.
Disclaimer
- Usage of Wifiphisher for attacking infrastructures without prior mutual consistency can be considered as an illegal activity. It is the final user’s responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.
Note: Be aware of sites pretending to be related with the Wifiphisher Project. They may be delivering malware.