APPLICATIONS
HOT NEWS
HiddenVM – A Revolutionary Approach To Maximizing Digital Privacy
HiddenVM is an innovation in computing privacy. Imagine you're entering a country at the airport.
The border agents seize your laptop and force you to...
© kalilinuxtutorials.com 2025













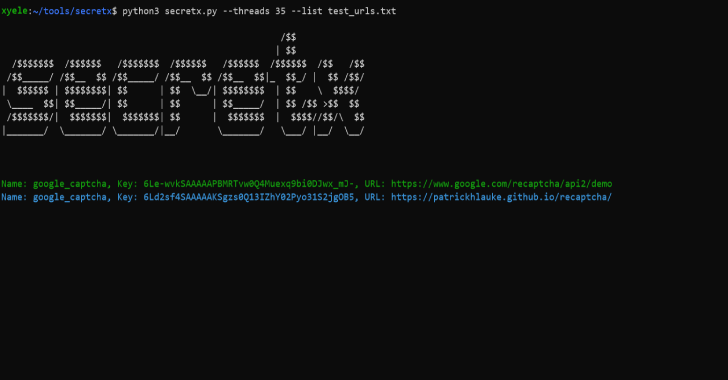
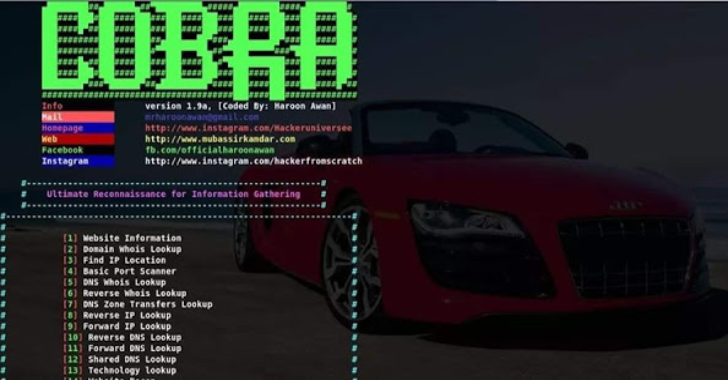
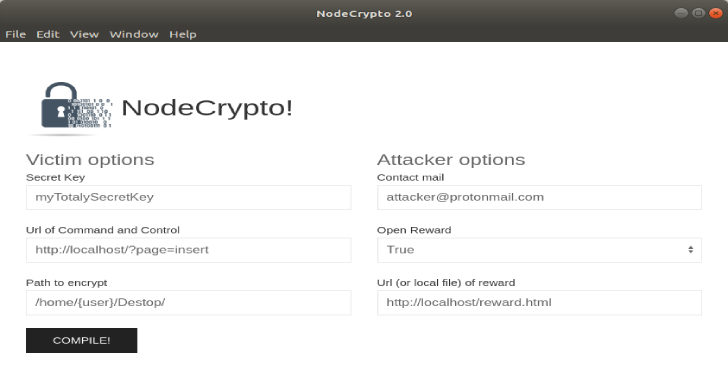

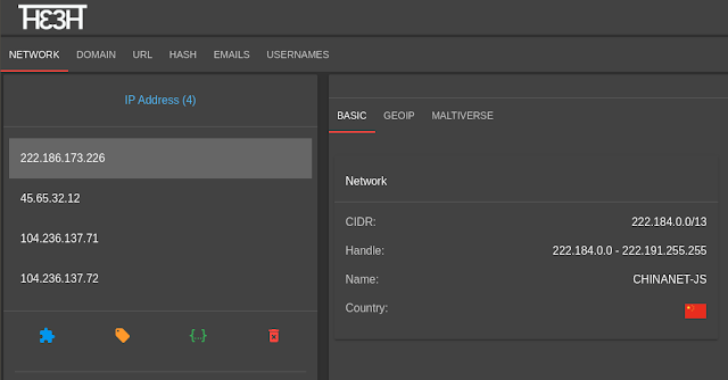

.webp)