The AWS Cobalt Redirector is a tool designed to streamline the deployment of a command-and-control (C2) infrastructure for red team operations using AWS services.
It leverages Terraform and Ansible for automation and integrates AWS resources like CloudFront, Lambda, and EC2 to create a robust redirector setup.
Functionality
The AWS Cobalt Redirector simplifies the process of deploying a redirector for Cobalt Strike, a popular red teaming tool.
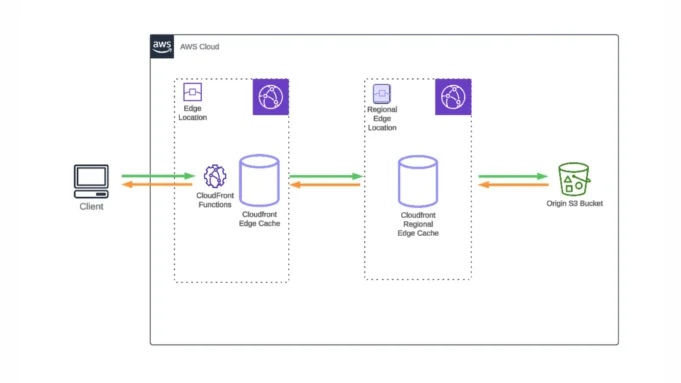
The redirector acts as an intermediary between the attacker’s team server and the target systems, obfuscating traffic and enhancing operational security. The setup uses:
- AWS CloudFront: A content delivery network (CDN) that masks the origin of traffic.
- AWS Lambda: A serverless compute service that processes incoming HTTP requests and forwards them to the team server.
- AWS EC2: Hosts the Cobalt Strike team server.
The Lambda function is configured to consume minimal resources (125 MB memory), ensuring cost-effectiveness during operations.
- Configure variables in the
terraform.tfvarsfile. - Deploy infrastructure using Terraform.
- Update the Ansible inventory with the host details (
ansible/inventory/hosts.yml). - Place your Cobalt Strike archive (
cobaltstrike.tgz) inansible/roles/cobaltstrike/files/. - Add your malleable profile file to
ansible/roles/cobaltstrike/files/. - Define mandatory variables in
ansible/inventory/redteam.yml. - Execute the playbook
playbook/cobaltstrike.ymlto finalize the setup.
Once completed, this automated process deploys a fully functional redirector infrastructure.
- Automation: The use of Terraform and Ansible ensures rapid and error-free deployment.
- Obfuscation: CloudFront and Lambda add layers of redirection, making it harder to trace back to the team server.
- Scalability: AWS services provide flexibility to scale resources as needed.
This tool is particularly valuable for red teams seeking efficient, secure, and scalable C2 infrastructure without manual configuration complexities.













.webp)
