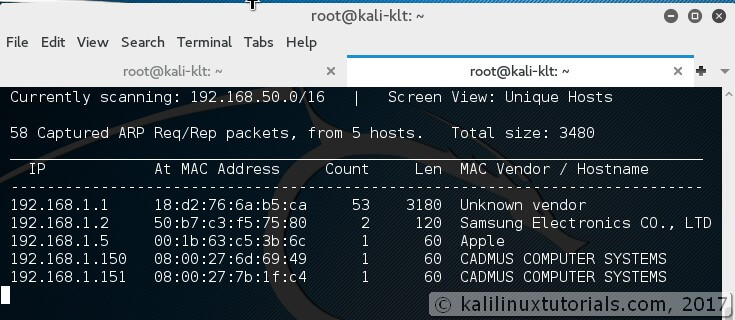
Kali Linux
Home Kali Linux
Learn Kali Linux with step-by-step ethical hacking tutorials. Explore penetration testing, information gathering, exploitation, password attacks, wireless security, and advanced cybersecurity tools. Perfect for beginners and professionals looking to master Kali Linux for ethical hacking and security assessments.