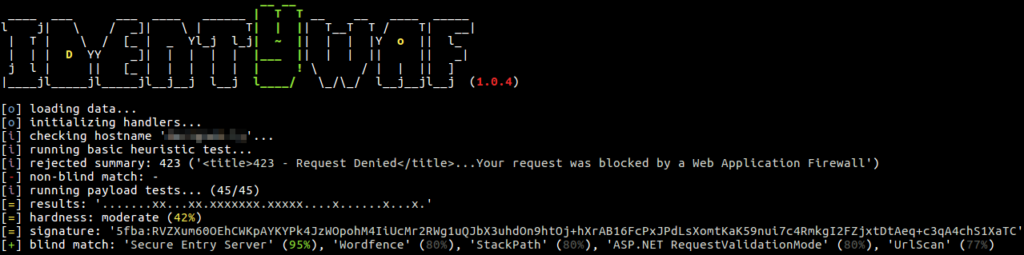
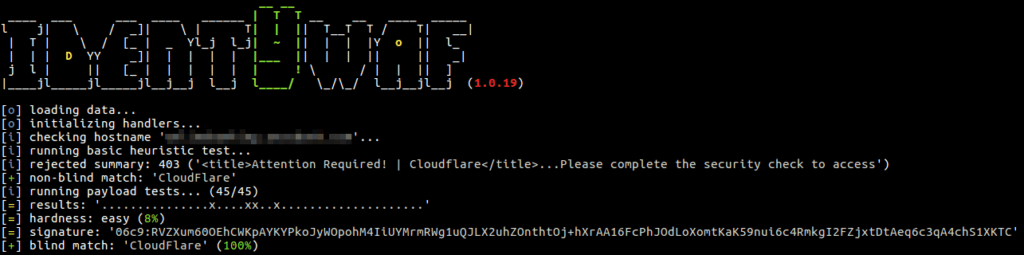
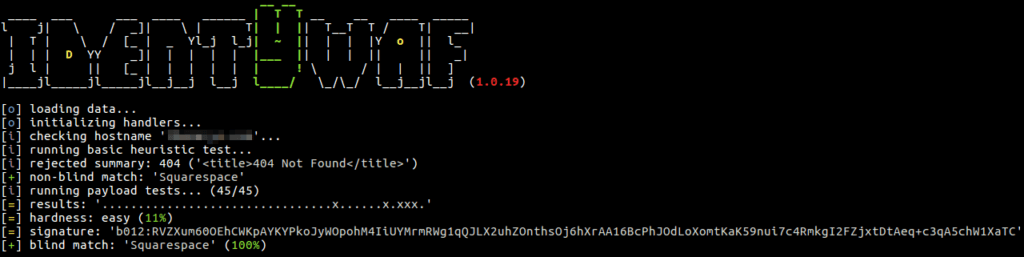
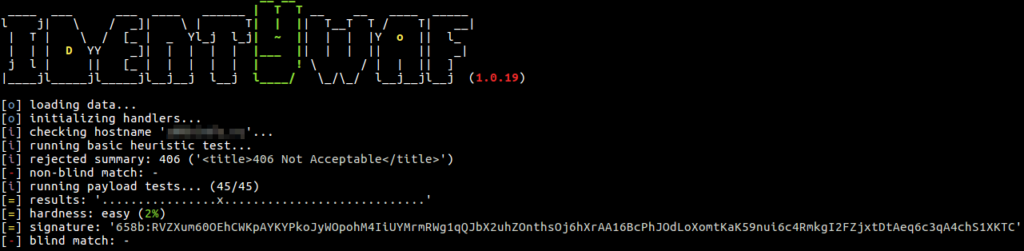
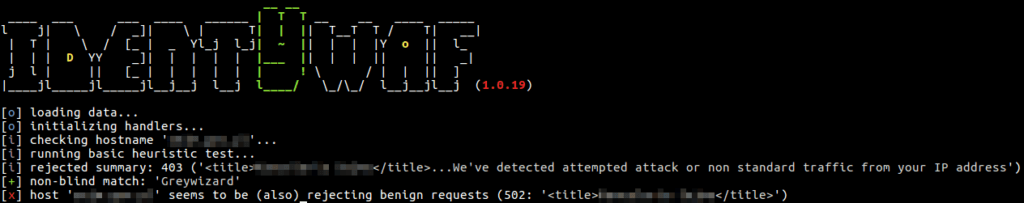
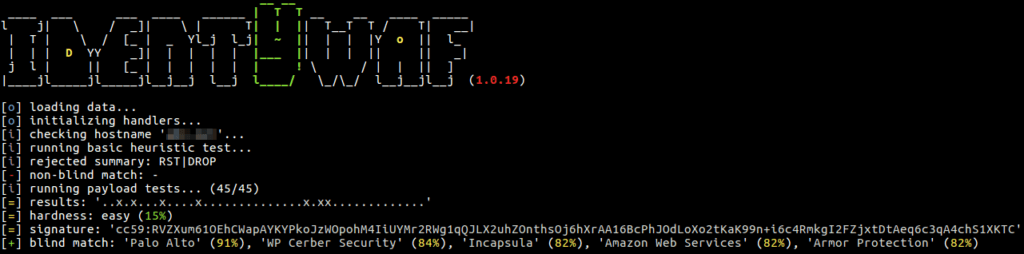
identYwaf is an identification tool that can recognise web protection type (i.e. WAF) based on blind inference.
Blind inference is being done by inspecting responses provoked by a set of predefined offensive (non-destructive) payloads, where those are used only to trigger the web protection system in between (e.g. http://<host>?aeD0oowi=1 AND 2>1).
Currently it supports more than 70 different protection products (e.g. aeSecure, Airlock, CleanTalk, CrawlProtect, Imunify360, MalCare, ModSecurity, Palo Alto, SiteGuard, UrlScan, Wallarm, WatchGuard, Wordfence, etc.), while the knowledge-base is constantly growing.
Also Read:H8mail – Email OSINT And Password Breach Hunting
Installation
You can download the latest zipball by clicking here.
Preferably, you can download it by cloning the Git repository:
git clone –depth 1 https://github.com/stamparm/identYwaf.git
It works out of the box with any Python version from 2.6.x to 3.7.x on any platform.
Usage
$ python identYwaf.py
__ __
____ ___ ___ ____ ______ | T T __ __ ____ _____
l j| \ / _]| \ | T| | || T__T T / T| __|
| T | \ / [_ | _ Yl_j l_j| ~ || | | |Y o || l_
| | | D YY _]| | | | | |___ || | | || || _|
j l | || [_ | | | | | | ! \ / | | || ]
|____jl_____jl_____jl__j__j l__j l____/ \_/\_/ l__j__jl__j (1.0.62)
Usage: python identYwaf.py [options] <host|url>
Options:
--version Show program's version number and exit
-h, --help Show this help message and exit
--delay=DELAY Delay (sec) between tests (default: 0)
--timeout=TIMEOUT Response timeout (sec) (default: 10)
--proxy=PROXY HTTP proxy address (e.g. "http://127.0.0.1:8080")
--random-agent=R.. Use random HTTP User-Agent header value
--string=STRING String to search for in rejected responsesScreenshots