Faraday : Open Source Vulnerability Management Platform
Security has two difficult tasks: designing smart ways of getting new information, and keeping track of findings to improve remediation efforts. With Faraday, you may focus on discovering vulnerabilities while we help you with the rest. Just use it in your terminal and get your work organized on the run. Faraday was made to let you take advantage of...
Upload_Bypass_Carnage : File Upload Restrictions Bypass, By Using Different Bug Bounty Techniques!
Upload_bypass,File upload restrictions bypass, by using different bug bounty techniques! POC video: https://www.youtube.com/watch?v=quFoDysbDto&ab_channel=SagivMichael Installation: pip3 install -r requirements.txt Usage: upload_bypass.py Options: -h, --help show this help message and exit -u URL, --url=URL Supply the login page, for example: -u http://192.168.98.200/login.php' -s , --success Success message when upload an image, example: -s 'Image uploaded successfully.' -e , --extension Provide server backend extension, for example: --extension php...
OffensivePipeline : To Download And Build C# Tools, To Improve Their Evasion For Red Team Exercises
OffensivePipeline allows you to download and build C# tools, applying certain modifications in order to improve their evasion for Red Team exercises.A common use of OffensivePipeline is to download a tool from a Git repository, randomise certain values in the project, build it, obfuscate the resulting binary and generate a shellcode. Features Currently only supports C# (.Net Framework) projects Allows to clone...
Misp-Extractor : Tool That Connects To A MISP Instance And Retrieves Attributes Of Specific Types (Such As IP Addresses, URLs, And Hashes)
Misp-Extractor is a simple Python script that connects to a MISP instance and retrieves attributes of specific types (such as IP addresses, URLs, and hashes). The retrieved attributes are then written to separate files. MISP Extractor This code connects to a given MISP (Malware Information Sharing Platform) server and parses a given number of events, writing the IP addresses, URLs, and...
Invoke-Transfer : PowerShell Clipboard Data Transfer
Invoke-Transfer is a PowerShell Clipboard Data Transfer. This tool helps you to send files in highly restricted environments such as Citrix, RDP, VNC, Guacamole.. using the clipboard function. As long as you can send text through the clipboard, you can send files in text format, in small Base64 encoded chunks. Additionally, you can transfer files from a screenshot, using the native...
Web-Hacking-Playground : Web Application With Vulnerabilities Found In Real Cases, Both In Pentests And In Bug Bounty Programs
Web Hacking Playground is a controlled web hacking environment. It consists of vulnerabilities found in real cases, both in pentests and in Bug Bounty programs. The objective is that users can practice with them, and learn to detect and exploit them. Other topics of interest will also be addressed, such as: bypassing filters by creating custom payloads, executing chained attacks...
Email-Vulnerablity-Checker : Find Email Spoofing Vulnerability Of Domains
Email Vulnerablity Checker v1.1.1 verifies whether the domain is vulnerable to spoofing by Email-vulnerablity-checker Features This tool will automatically tells you if the domain is email spoofable or not you can do single and multiple domain input as well (for multiple domain checker you need to have text file with domains in it) Usage: Clone the package by running: git clone https://github.com/BLACK-SCORP10/Email-Vulnerablity-Checker.git Step 1. Install...
DNSrecon-gui : DNSrecon Tool With GUI For Kali Linux
DNSRecon is a DNS scanning and enumeration tool written in Python, which allows you to perform different tasks, such as enumeration of standard records for a defined domain (A, NS, SOA, and MX). Top-level domain expansion for a defined domain. With this graph-oriented user interface, the different records of a specific domain can be observed, classified and ordered in a...
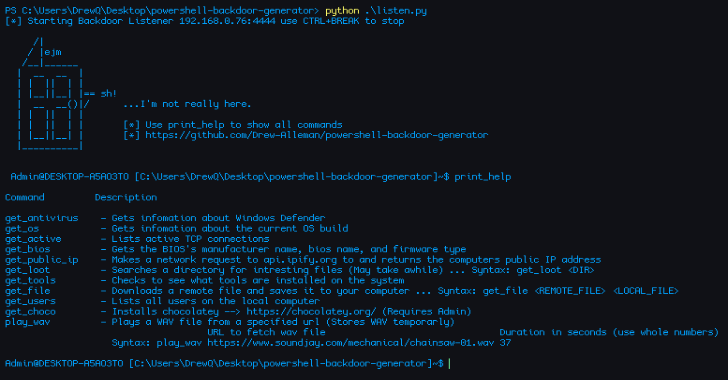
Powershell-Backdoor-Generator : To Create A Flipper Zero/ Hak5 USB Rubber Ducky Payload
Powershell-Backdoor-Generator is a reverse backdoor written in Powershell and obfuscated with Python. Allowing the backdoor to have a new signature after every build. With the capabilties to create a Flipper Zero/ Hak5 USB Rubber ducky payload. usage: listen.py [-h] [--ip-address IP_ADDRESS] [--port PORT] [--random] [--out OUT] [--verbose] [--delay DELAY] [--flipper FLIPPER] [--ducky] ...
Winevt_logs_analysis : Searching .evtx Logs For Remote Connections
Winevt logs analysis is a simple script for the purpose of finding remote connections to Windows machine and ideally some public IPs. It checks for some EventIDs regarding remote logins and sessions. You should pip install -r requirements.txt so the script can work and parse some of the .evtx files inside winevt folder. The winevt/Logs folders and the script must have...


















.webp)