LabSync : Revolutionizing Collaboration In Laboratories And Reverse Engineering
LabSync is an innovative tool designed to enhance collaboration and efficiency in various laboratory and technical environments. Among the multiple implementations of LabSync, its application as an IDA plugin for reverse engineering stands out for its unique functionality. LabSync For IDA : Synchronizing Reverse Engineering Efforts LabSync serves as a plugin for the Interactive Disassembler (IDA), enabling multiple users to synchronize...
Rig : A Tool For LLM-Powered Applications
Rig is a cutting-edge Rust library designed to facilitate the development of scalable, modular, and ergonomic applications powered by large language models (LLMs). With its robust features and integrations, Rig simplifies the process of embedding LLM capabilities into applications, making it a valuable tool for developers working with AI technologies. Key Features Of Rig Rig offers several high-level features that make...
CVE-2024-55591 : Fortinet FortiOS Authentication Bypass Vulnerability
CVE-2024-55591 is a critical authentication bypass vulnerability affecting Fortinet's FortiOS and FortiProxy systems. This flaw, rated with a CVSS score of 9.8, allows unauthenticated attackers to gain super-admin privileges by exploiting improper handling of session tokens in the Node.js WebSocket module. The vulnerability has been actively exploited in the wild since November 2024, posing significant risks to enterprise networks. The...
Draugr : Advanced Tools For Synthetic Stack Frame Manipulation
The Draugr toolset provides a robust framework for performing synthetic stack frame manipulation, primarily designed to bypass modern Endpoint Detection and Response (EDR) systems. It includes two key components: Draugr-Template and Draugr-Strike, which enable developers to implement advanced techniques such as return address spoofing and remote process injection. Draugr-Template The Draugr-Template is a Cobalt Strike BOF (Beacon Object File) template that...
Awesome-Red-Team-Operation : A Comprehensive Toolkit For Advanced Cybersecurity
The "Awesome-Red-Team-Operation" repository is a comprehensive collection of tools designed to support red team operations, penetration testing, and cybersecurity assessments. These tools span various stages of an attack lifecycle, including reconnaissance, exploitation, privilege escalation, lateral movement, and post-exploitation. Below is a detailed overview of the tools and their functionalities: Key Tool Categories And Functions 1. Reconnaissance Tools like Spiderfoot, Shodan, and Crt.sh...
Mise : A Versatile Development Environment Tool
Mise is a powerful and versatile tool designed to streamline and enhance the development environment for programmers. It combines the functionality of several popular tools, making it an all-in-one solution for managing development workflows. Below is an overview of its key features, usage, and benefits. What Does Mise Do? Mise serves as a front-end to your development environment, offering three primary...
Tabby : Your Open-Source AI Coding Assistant
Tabby is an innovative, self-hosted AI coding assistant designed to provide developers with an open-source and on-premises alternative to proprietary tools like GitHub Copilot. By offering a robust set of features and seamless integration options, Tabby empowers teams to maintain full control over their development environments while leveraging the power of AI-assisted coding. Key Features Self-Contained Design: Tabby operates without requiring...
GoRedOps : A Golang Arsenal For Red Teamers And Security Professionals
GoRedOps is a comprehensive collection of Golang-based projects tailored for red teamers and offensive security professionals. This repository offers a wide array of tools and techniques essential for penetration testing, exploitation, and security research. Below is an overview of its structure and functionality. Project Structure And Tools GoRedOps is organized into multiple directories, each containing specialized tools for various offensive security...
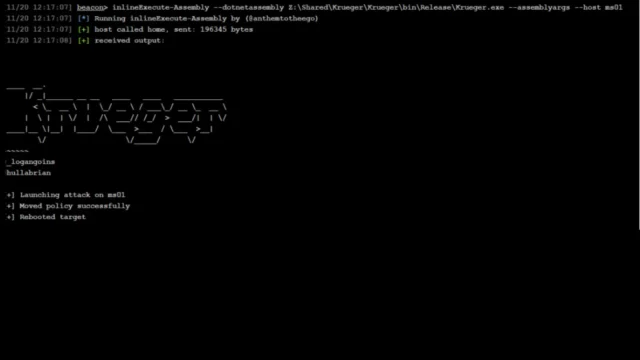
Krueger : Exploiting Windows Defender To Neutralize EDR Systems
Krueger is a Proof of Concept (PoC) .NET post-exploitation tool designed to disable Endpoint Detection and Response (EDR) systems during lateral movement in a network. Developed by security researcher Logan Goins, Krueger leverages Windows Defender Application Control (WDAC), a Microsoft utility originally intended to enhance security by controlling executable code on Windows devices. However, Krueger weaponizes this feature to...
Tokio : Unleashing Asynchronous Power In Rust For Network Applications
Tokio is a high-performance, asynchronous runtime designed for the Rust programming language. It provides the essential building blocks for creating reliable, scalable, and efficient asynchronous applications. Leveraging Rust's ownership model and type system, Tokio ensures thread safety and minimizes bugs, making it a preferred choice for network programming and other I/O-bound tasks. Core Features Multithreaded Task Scheduler: Tokio uses a work-stealing...