ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely. Usage examples of ODAT: Tested on Oracle Database 10g, 11g, 12c, 18c and 19c. Features Thanks to ODAT, you can: This list is not exhaustive. Supported Platforms and dependencies ODAT is compatible with Linux only. …
Tag Archives: database
Assless-Chaps : Crack MSCHAPv2 Challenge/Responses Quickly Using A Database Of NT Hashes
Assless-CHAPs is an efficient way to recover the NT hash used in a MSCHAPv2/NTLMv1 exchange if you have the challenge and response (e.g. from a WiFi EAP WPE attack). It requires a database of NT hashes, instructions on how to make these from existing lists or using hashcat with wordlists and rules are available below. …
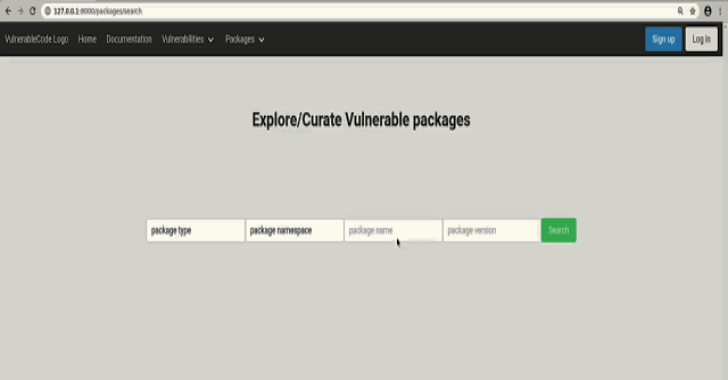
Vulnerablecode : A Free And Open Vulnerabilities Database
VulnerableCode is a free and open database of FOSS software package vulnerabilities and the tools to create and keep the data current. It is made by the FOSS community to improve and secure the open source software ecosystem. Why? The existing solutions are commercial proprietary vulnerability databases, which in itself does not make sense because …
Continue reading “Vulnerablecode : A Free And Open Vulnerabilities Database”
SnitchDNS : Database Driven DNS Server With A Web UI
SnitchDNS is a database driven DNS Server with a Web UI, written in Python and Twisted, that makes DNS administration easier with all configuration changed applied instantly without restarting any system services. One of its main features is the logging of all DNS queries allowing the discovery of network traffic endpoints, and it can also …
Continue reading “SnitchDNS : Database Driven DNS Server With A Web UI”
Pagodo : Automate Google Hacking Database Scraping And Searching
PaGoDo goal is to develop a passive Google dork script to collect potentially vulnerable web pages and applications on the Internet. There are 2 parts. The first is ghdb_scraper.py that retrieves Google Dorks and the second portion is pagodo.py that leverages the information gathered by ghdb_scraper.py. What are Google Dorks? The awesome folks at Offensive …
Continue reading “Pagodo : Automate Google Hacking Database Scraping And Searching”
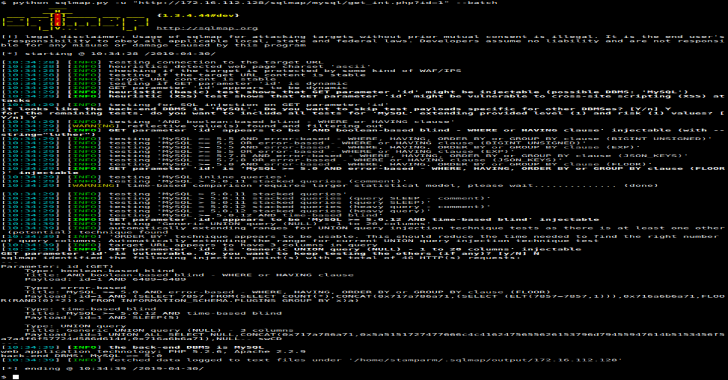
SQLMap : Automatic SQL Injection & Database Takeover Tool
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the …
Continue reading “SQLMap : Automatic SQL Injection & Database Takeover Tool”
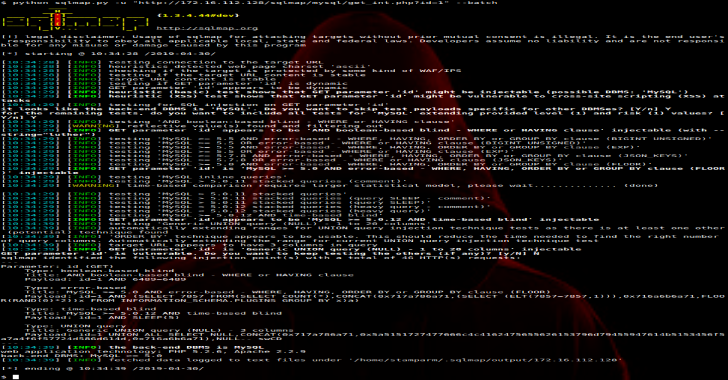
SQLMap : Automatic SQL Injection & Database Takeover Tool
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the …
Continue reading “SQLMap : Automatic SQL Injection & Database Takeover Tool”
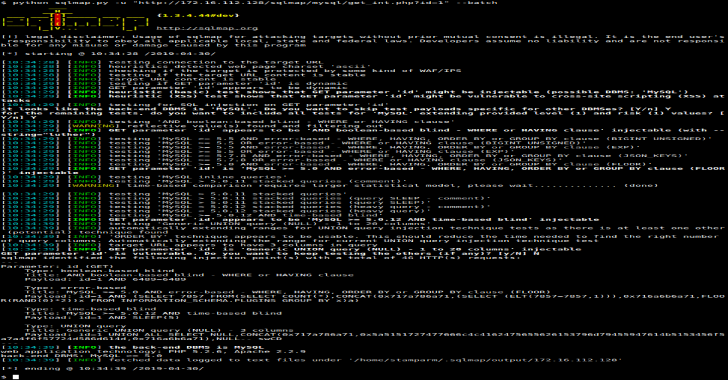
SQLMap : Automatic SQL Injection & Database Takeover Tool
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the …
Continue reading “SQLMap : Automatic SQL Injection & Database Takeover Tool”
Lst2x64dbg : Extract Labels From IDA .lst or Ghidra .csv File & Export x64dbg Database
lst2x64dbg script extracts all the labels found in the LST file that is given as the script’s single argument. An x64dbg database is created in the current directory based on the extracted labels. The LST file can be generated in IDA from the File menu: Produce file -> Create LST file… Example $ python3 lst2x64dbg.py …
WhatBreach : OSINT Tool To Find Breached Emails & Databases
WhatBreach is a tool to search for breached emails and their corresponding database. It takes either a single email or a list of emails and searches them leveraging haveibeenpwned.com‘s API, from there (if there are any breaches) it will search for the query link on Dehashed pertaining to the database, and output all breaches along …
Continue reading “WhatBreach : OSINT Tool To Find Breached Emails & Databases”