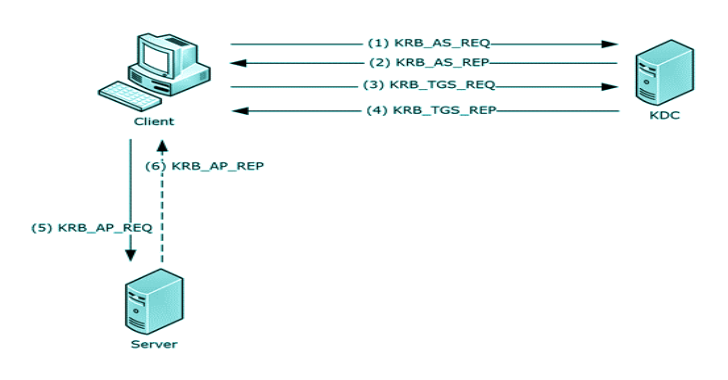
Heap_Detective is the simple way to detect heap memory pitfalls in C++ and C. Beta. This tool uses the taint analysis technique for static analysis and aims to identify points of heap memory usage vulnerabilities in C and C++ languages. The tool uses a common approach in the first phase of static analysis, using tokenization …
Continue reading “Heap_detective : To Detect Heap Memory Pitfalls In C++ And C”