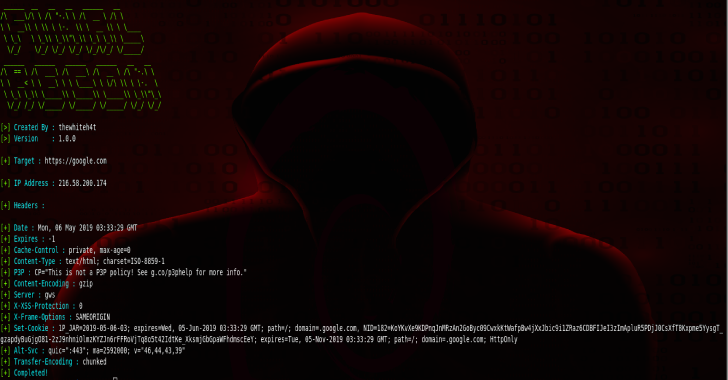
FinalRecon is an all in one automatic web reconnaissance tool written in python. Goal of FinalRecon is to provide an overview of the target in a short amount of time while maintaining the accuracy of results. Instead of executing several tools one after another it can provide similar results keeping dependencies small and simple. Available In Features FinalRecon provides detailed information such as : Configuration API …
Continue reading “FinalRecon : The Ultimate All-In-One Web Reconnaissance Tool”
.webp)