APPLICATIONS
HOT NEWS
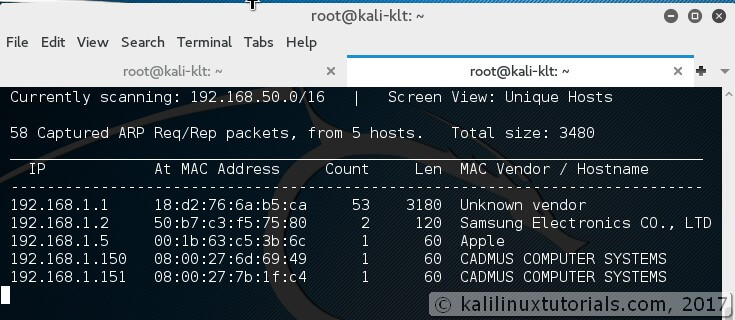
The Spy’s Job – Mastering OSINT With XDeadHackerX’s Comprehensive Toolkit
Buenas, soy XDeadHackerX y quiero presentaros mi nueva herramienta llamada The_Spy´s_Job.
Esta Tool está enfocado al OSINT de casi todos los ámbitos (Personas, Nicknames, Redes Sociales, Emails, Números de Teléfono, Páginas...
© kalilinuxtutorials.com 2025











.webp)