APPLICATIONS
HOT NEWS
Arena-Hard-Auto : Advancing LLM Evaluation With Style Control Integration
Arena-Hard-Auto-v0.1 (See Paper) is an automatic evaluation tool for instruction-tuned LLMs. It contains 500 challenging user queries sourced from Chatbot Arena.
We prompt GPT-4-Turbo...
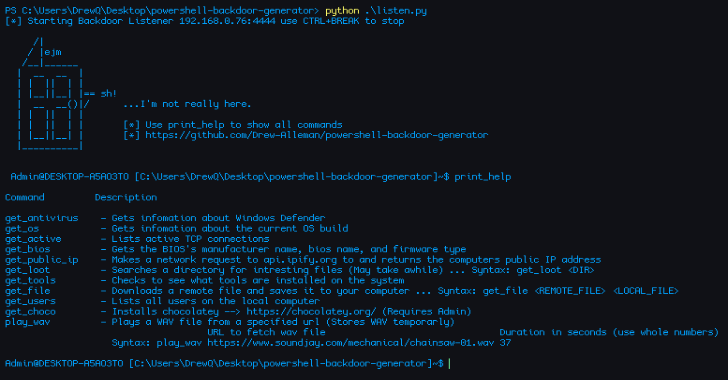
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2025


















.png)


.png)


.webp)



