EasyEASM : Your Zero-Dollar Solution For Attack Surface Management
Easy EASM is just that... the easiest to set-up tool to give your organization visibility into its external facing assets. The industry is dominated by $30k vendors selling "Attack Surface Management," but OG bug bounty hunters and red teamers know the truth. External ASM was born out of the bug bounty scene. Most of these $30k vendors use this open-source...
PMKID WPA2 Cracker – Decrypting WPA2 WiFi Networks The Easy Way
This program is a tool written in Python to recover the pre-shared key of a WPA2 WiFi network without any de-authentication or requiring any clients to be on the network. It targets the weakness of certain access points advertising the PMKID value in EAPOL message 1. Program Usage python pmkidcracker.py -s <SSID> -ap <APMAC> -c <CLIENTMAC> -p <PMKID> -w <WORDLIST> -t...
CloudRecon – Uncovering Hidden Cloud Assets With SSL Certificate Analysis
In the ever-evolving landscape of cybersecurity, red teamers and bug hunters are constantly seeking new tools to aid in their campaigns and hunts. CloudRecon, a powerful suite of tools presented at DEFCON 31 by Gunnar Andrews and Jason Haddix, is one such solution. This article explores how CloudRecon empowers security professionals to discover ephemeral and development assets within cloud...
PipeViewer – Exploring Windows Named Pipes For Security And Permissions
PipeViewer is a GUI tool that allows users to view details about Windows Named pipes and their permissions. It is designed to be useful for security researchers who are interested in searching for named pipes with weak permissions or testing the security of named pipes. With PipeViewer, users can easily view and analyze information about named pipes on their...
MetaHub – Revolutionizing Vulnerability Management With Contextual Impact Evaluation
MetaHub is an automated contextual security findings enrichment and impact evaluation tool for vulnerability management. You can use it with AWS Security Hub or any ASFF-compatible security scanner. Stop relying on useless severities and switch to impact scoring definitions based on YOUR context. Table Of Contents Description Quick Run Context Impact High Level Architecture Use Cases Configuration Run with Python Run with Docker Run with Lambda Run with Security Hub Custom Action AWS...
Nysm : Unveiling The Art Of Stealthy eBPF Post-Exploitation Containers
In the ever-evolving landscape of cybersecurity, offensive tools based on eBPF (Extended Berkeley Packet Filter) have gained popularity, from credential stealers to rootkits. This article delves into the realm of "Nysm," a stealthy post-exploitation container designed to make eBPF-based offensive tools invisible to the watchful eyes of System Administrators. Nysm not only conceals eBPF but also shields a wide...
Exploring Best EDR Of The Market (BEOTM) : Unveiling User-Mode Evasion Techniques and Defensive Strategies
BestEDROfTheMarket is a naive user-mode EDR (Endpoint Detection and Response) project, designed to serve as a testing ground for understanding and bypassing EDR's user-mode detection methods that are frequently used by these security solutions.These techniques are mainly based on a dynamic analysis of the target process state (memory, API calls, etc.), Feel free to check this short article I wrote...
Valid8Proxy: Streamlining Proxy Management for Web Scraping and Network Security
Valid8Proxy is a versatile and user-friendly tool designed for fetching, validating, and storing working proxies. Whether you need proxies for web scraping, data anonymization, or testing network security, Valid8Proxy simplifies the process by providing a seamless way to obtain reliable and verified proxies. Features: Proxy Fetching: Retrieve proxies from popular proxy sources with a single command. Proxy Validation: Efficiently validate proxies using multithreading to...
CATSploit: Revolutionizing Automated Penetration Testing with Cyber Attack Techniques Scoring (CATS) Method
CATSploit is an automated penetration testing tool using Cyber Attack Techniques Scoring (CATS) method that can be used without pentester. Currently, pentesters implicitly made the selection of suitable attack techniques for target systems to be attacked. CATSploit uses system configuration information such as OS, open ports, software version collected by scanner and calculates a score value for capture eVc...
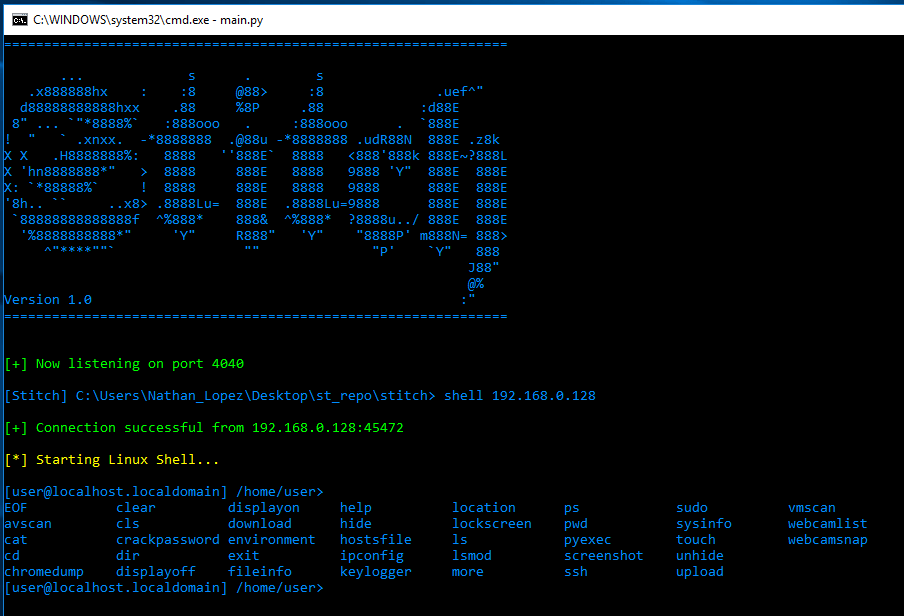
Demonized Shell: Advancing Linux Persistence Techniques and Security Implications.
The article "Demonized Shell: Advancing Linux Persistence Techniques and Security Implications" goes into great detail about D3m0n1z3dShell, a complex tool made for making things persistent in Linux settings. The opening would probably talk about how this tool is a big step forward in Linux system security and how it has many features for keeping access and control over Linux...











.webp)

.webp)
.webp)
.webp)