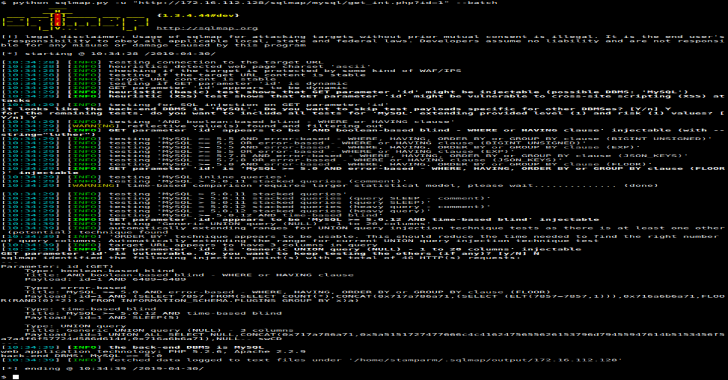
SQLMap : Automatic SQL Injection & Database Takeover Tool
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the...
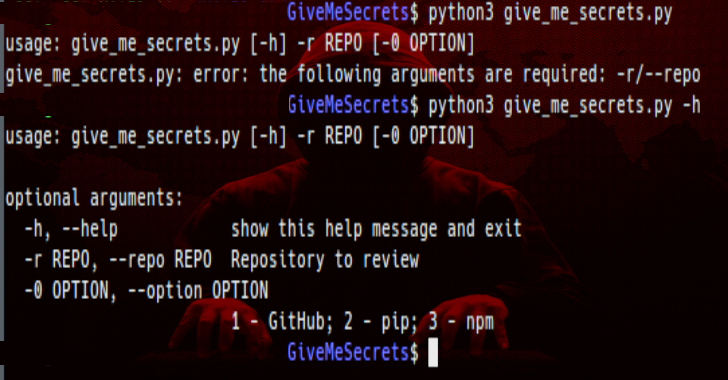
GiveMeSecrets : Use Regular Expressions To Get Sensitive Information
GiveMeSecrets use regular expressions to get sensitive information from a given repository (GitHub, pip or npm). You only need to have python 3.6 or higher installed to launch this script. In addition you must have installed in the system git, pip and npm. How to use? It's very easy to use, just run the script and pass the option...
Hardening Kubernetes Security with Falco: Runtime Threat Detection
Kubernetes has become a cornerstone of modern cloud-native applications, offering powerful orchestration capabilities for containerized applications. However, its complexity also introduces security challenges. Falco, an open-source runtime security tool, can help mitigate these challenges by providing real-time threat detection capabilities. This guide will delve into the technical details of using Falco to enhance Kubernetes security. What is Falco? Falco is an...
Lockdoor Framework : A Penetration Testing Framework with Cyber Security Resources
LockDoor is a Framework aimed at helping penetration testers, bug bounty hunters And cyber security engineers. This tool is designed for Debian/Ubuntu/ArchLinux based distributions to create a similar and familiar distribution for Penetration Testing. But containing the favorite and the most used tools by Pentesters. As pentesters, most of us has his personal ' /pentest/ ' directory so this Framework is...
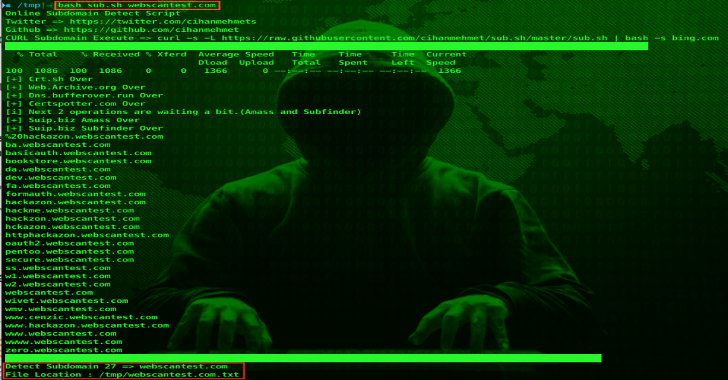
Sub.sh : Online Subdomain Detect Script
Sub.sh is a script to detect subdomain online. So let us have a look on it usage. Script bash sub.sh webscantest.com./sub.sh webscantest.com Curl curl -s -L https://raw.githubusercontent.com/cihanmehmet/sub.sh/master/sub.sh | bash -s webscantest.com Also Read - Re-composer : Randomly Changes Win32/64 PE Files For ‘Safer’ Uploading To Malware & Sandbox Sites Subdomain Alive Check bash sub_alive.sh bing.comcurl -s -L https://raw.githubusercontent.com/cihanmehmet/sub.sh/master/sub_alive.sh | bash -s bing.com" Fping Required Nmap -sn (No...
Cryptondie : A Ransomware Developed For Study Purposes
CryptonDie is a ransomware developed for study purposes. Options --key key used to encrypt and decrypt files, default is random string(recommended) --dir Home directory for the attack, default is / --encrypt Encrypt all files...
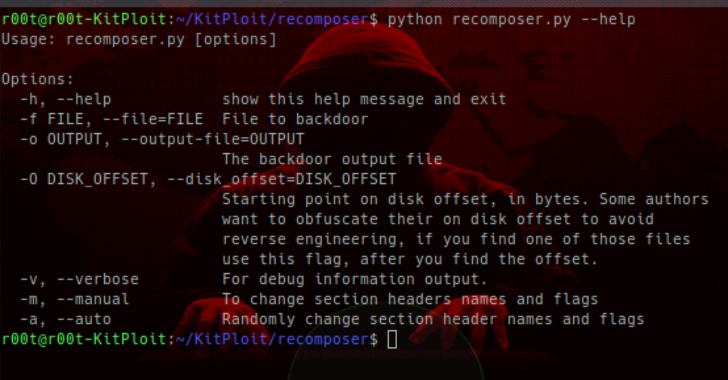
Re-composer : Randomly Changes Win32/64 PE Files For ‘Safer’ Uploading To Malware & Sandbox Sites
Ever have that not so safe feeling uploading your malware binaries to VirusTotal or other AV sites because you can look up binaries by hashes? Recomposer will take your binary and randomly do the following: Change the file nameChange the section namesChange the section flagsInjection random number of five different types of nops into each available code cave over 20...
DumpsterFire : Toolset – Security Incidents In A Box!
The DumpsterFire Toolset is a modular, menu-driven, cross-platform tool for building repeatable, time-delayed, distributed security events. Easily create custom event chains for Blue Team drills and sensor / alert mapping. Red Teams can create decoy incidents, distractions, and lures to support and scale their operations. Turn paper tabletop exercises into controlled "live fire" range events. Build event sequences ("narratives")...
Terraform AWS Secure Baseline : To Set Up Your AWS Account
Terraform Aws Secure Baseline is a terraform module to set up your AWS account with the secure baseline configuration based on CIS Amazon Web Services Foundations. Terraform Module Registry A terraform module to set up your AWS account with the reasonably secure configuration baseline. Most configurations are based on CIS Amazon Web Services Foundations v1.2.0. Starting from v0.10.0, this module requires Terraform...
SecurityNotFound : 404 Page Not Found Webshell
Clone or download the project: git clone https://github.com/CosasDePuma/SecurityNotFound.git SecurityNotFoundcd SecurityNotFound Installation The src/404.php file should be located on the target server.That server must have the ability to execute .php files.Here is an example of some of the most common routes on which servers are located: # 🏁 Windows (Xampp) C:Xampphtdocs# 🐧 Linux /var/www/html/ Note: Obviously, you and I know that you have legitimate...










.png)