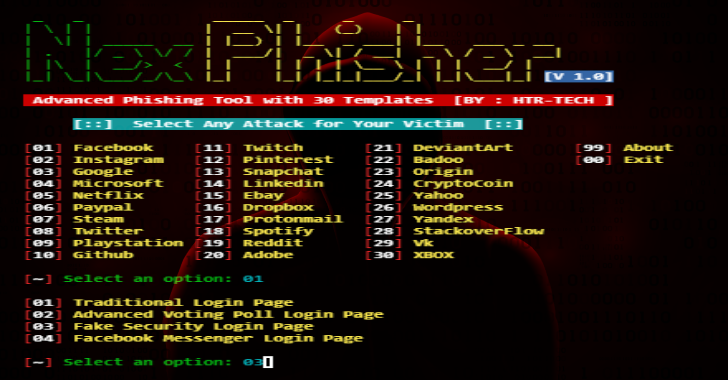
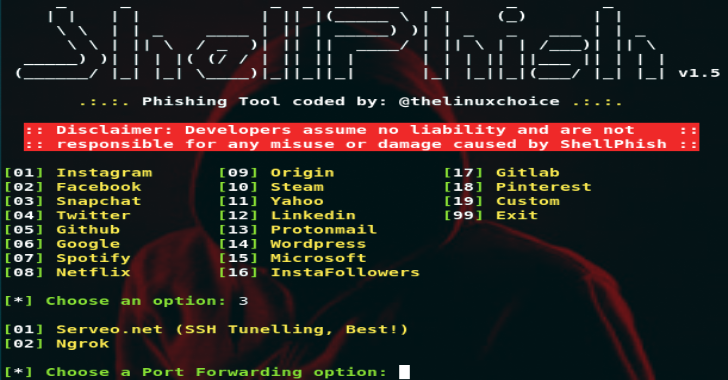
Zphisher is an upgraded form of Shellphish. The main source code is from Shellphish. But I have not fully copied it. I have upgraded it & cleared the Unnecessary Files. It has 37 Phishing Page Templates ; including Facebook , Twitter & Paypal. It also has 4 Port Forwarding Tools . Installation apt updateapt install …
Continue reading “ZPhisher : Automated Phishing Tool For Pentesters”

%20(1).png)