Introduction
As cyber threats grow more sophisticated, organizations need more than just firewalls and antivirus tools. They require complete visibility into their IT environment, covering user activities, endpoint logs, application events, and network traffic.
This is where SIEM (Security Information and Event Management) comes in. A SIEM solution collects, normalizes, and correlates logs and events from across an organization’s infrastructure. It provides real-time threat detection, incident response, and compliance reporting, helping security teams stay ahead of attacks.
In this guide, we’ll cover:
- What SIEM is and how it works
- SIEM architecture with visual diagrams
- Real-world use cases and attack scenarios
- Business impact and compliance benefits
- Why SIEM is critical for modern enterprises
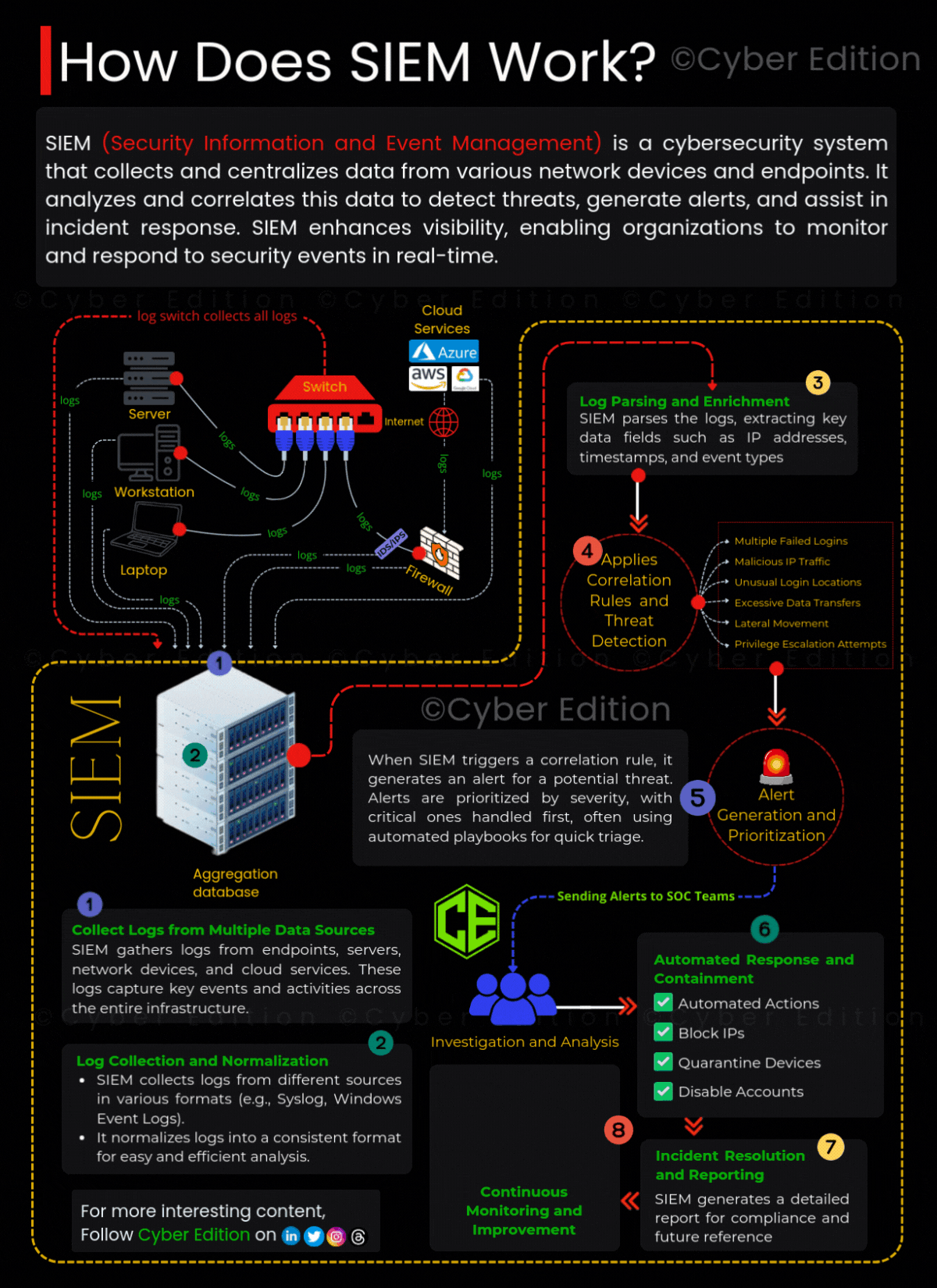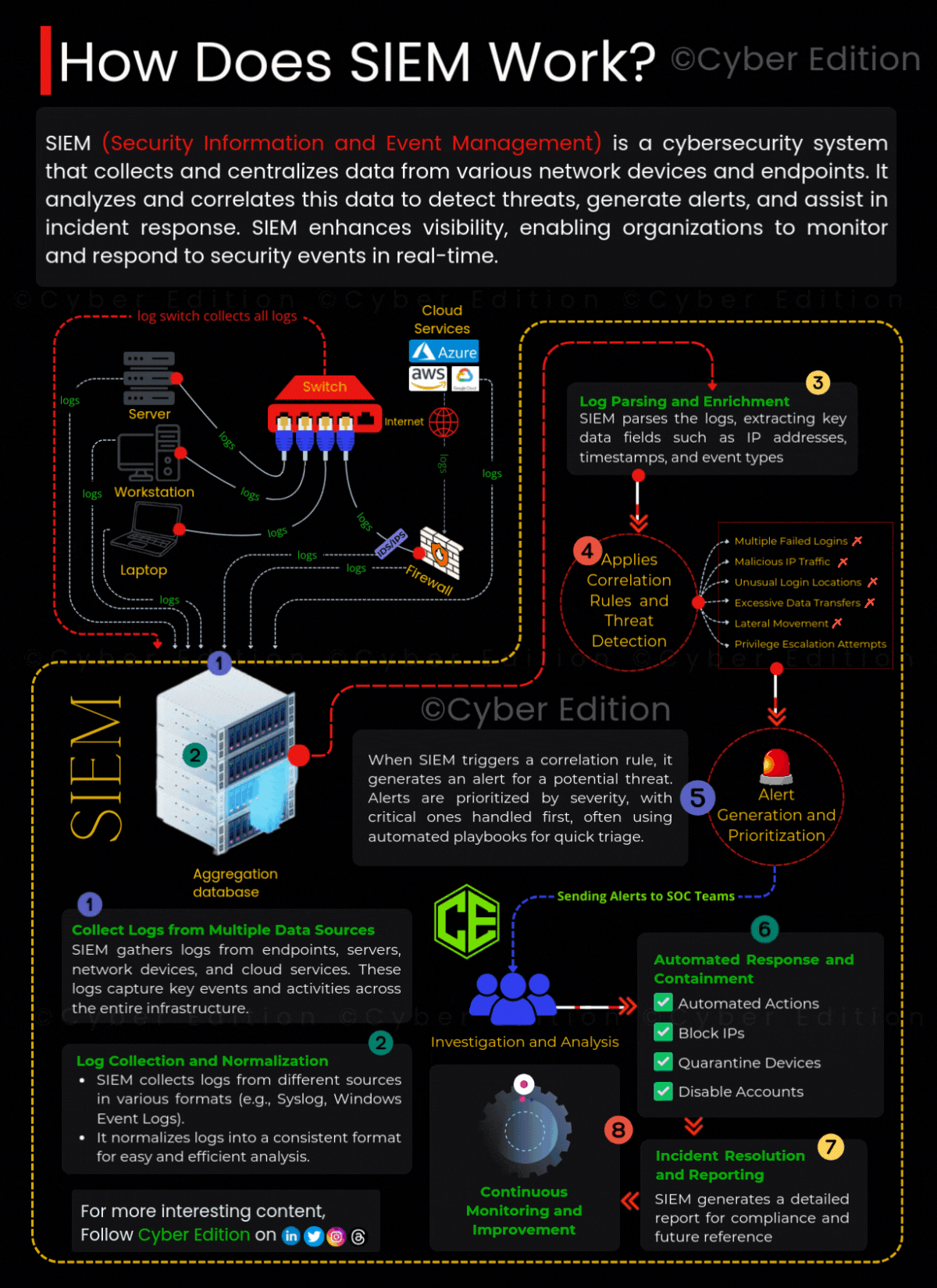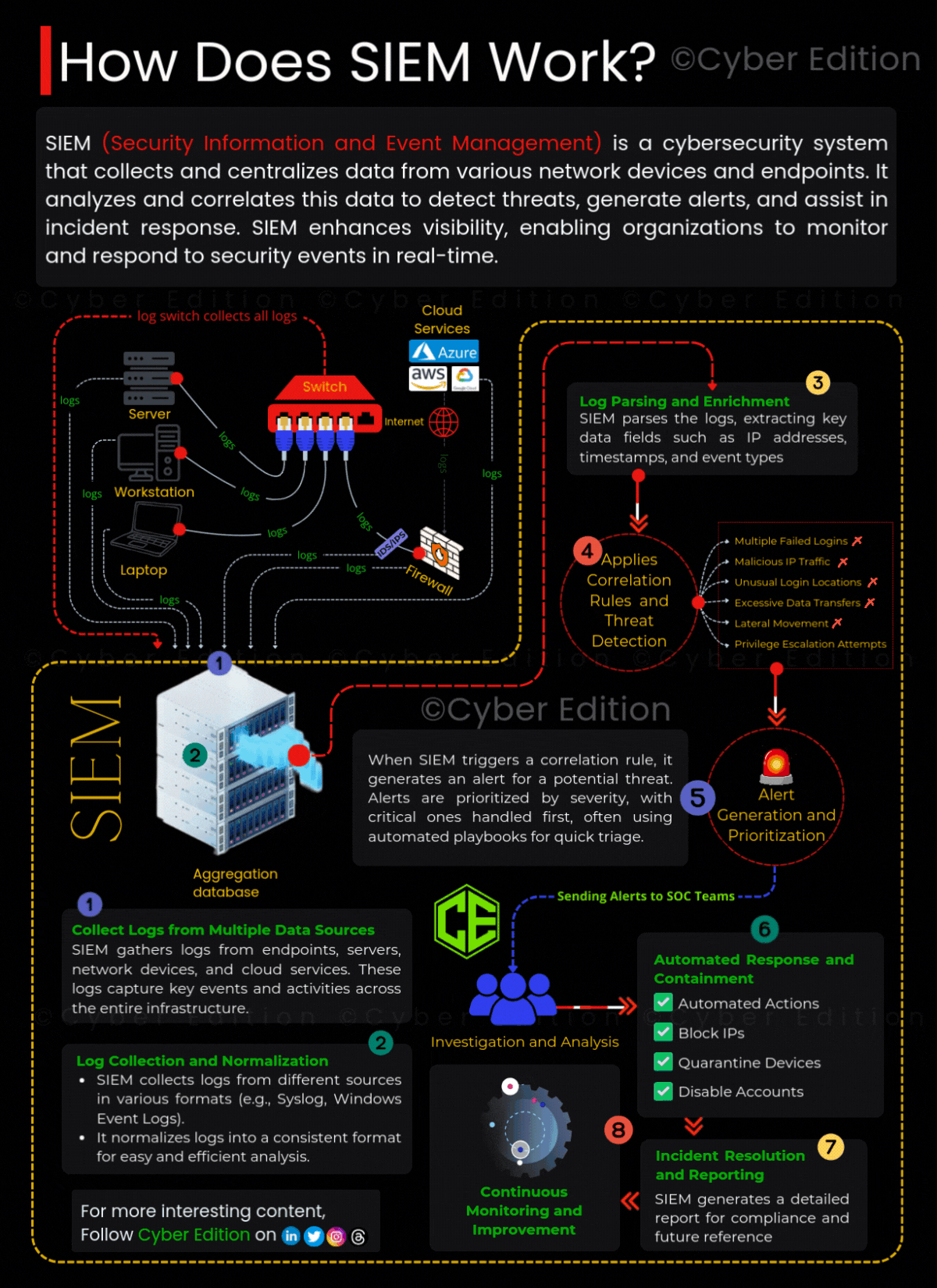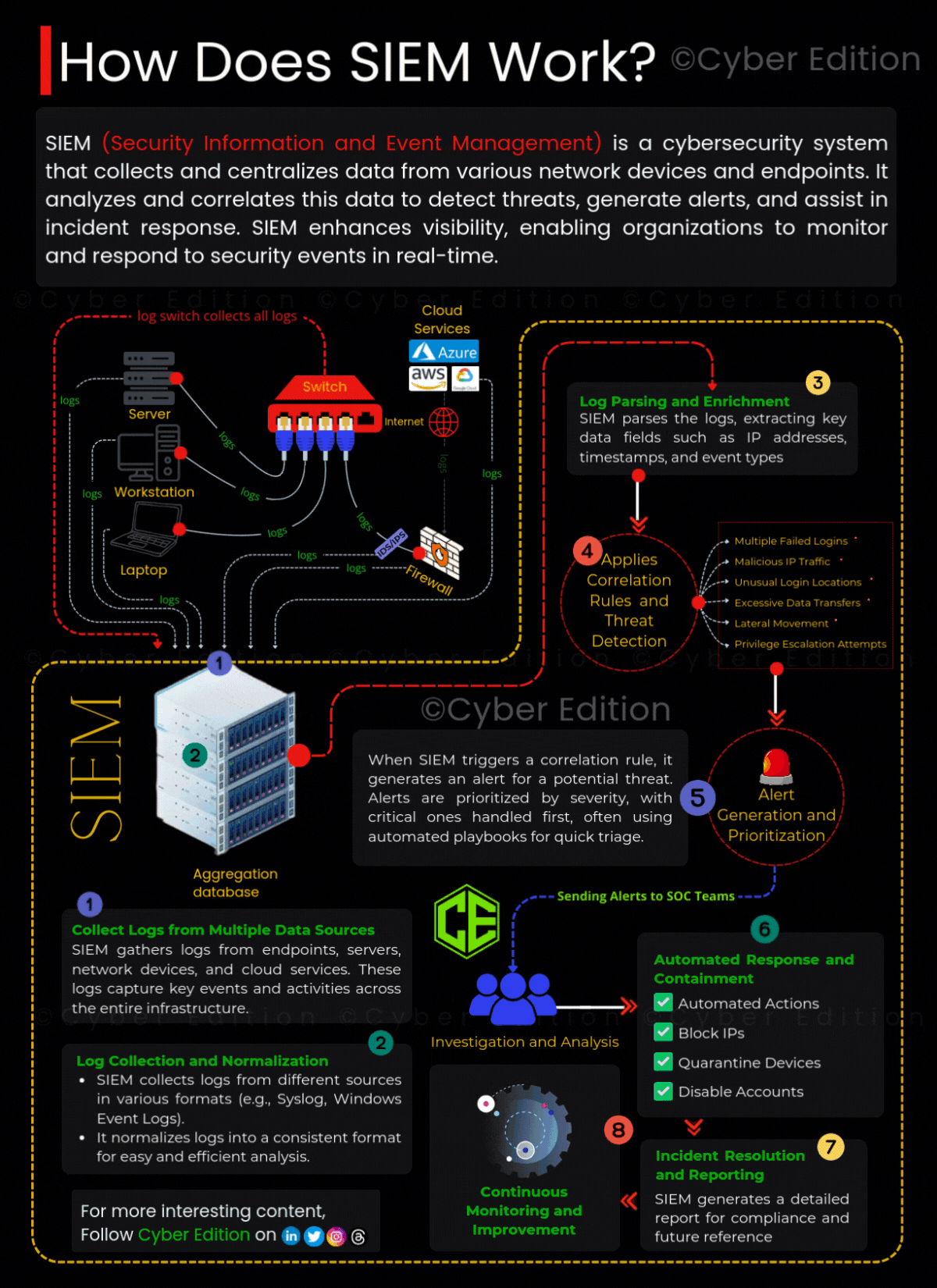
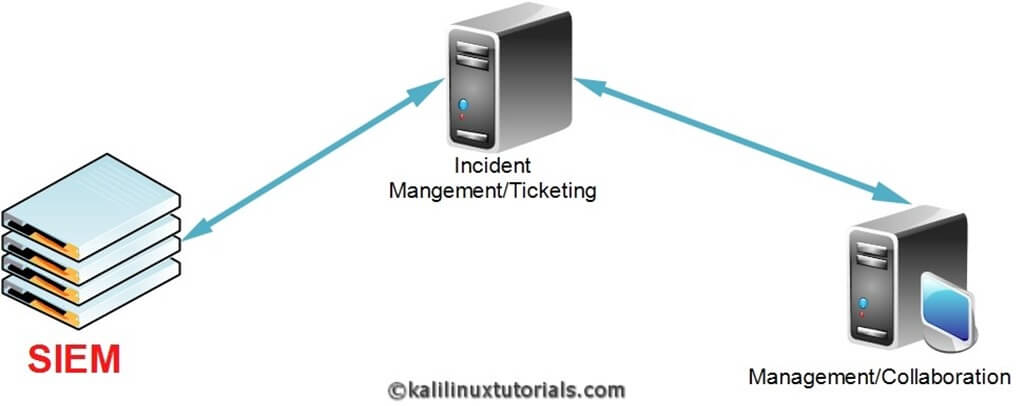
SIEM Architecture: How Logs Flow Into the System
SIEM collects data from a wide variety of sources:
- Network devices (routers, switches, firewalls)
- Servers and databases
- Applications (ERP, e-commerce, email systems, custom apps)
- Domain controllers and authentication systems
- Critical endpoints and user devices
- Cloud services (AWS, Azure, Google Cloud)
These logs are forwarded either via agent-based collection (installed software agents) or agentless collection (Syslog, APIs, Windows Event Forwarding).

Once collected, SIEM performs the following:
- Aggregation: Stores logs in a centralized database.
- Normalization: Converts logs into a consistent format.
- Correlation: Applies rules to identify patterns that indicate malicious activity.
- Alerting: Generates notifications for suspicious events.
- Reporting: Creates dashboards and compliance-ready reports.
How Does SIEM Work? Step by Step
To understand SIEM better, let’s break down the workflow:
1. Data Collection
SIEM gathers raw event data from multiple sources. This includes firewall logs, authentication attempts, DNS queries, and even cloud API logs.
2. Log Normalization
Each device produces logs in different formats. SIEM translates them into a standard schema, making them easy to analyze.
3. Parsing and Enrichment
Key details like IP addresses, user IDs, geolocation, and event types are extracted. Threat intelligence feeds enrich the data with context (e.g., identifying known malicious IPs).
4. Correlation and Threat Detection
Correlation rules connect seemingly unrelated events to detect threats.
- Example 1: A login from New York followed by a login from Europe within 5 minutes → impossible travel attack.
- Example 2: Multiple failed logins followed by a success → possible brute force attack.
5. Alerting and Prioritization
Alerts are categorized by severity, ensuring that SOC (Security Operations Center) teams focus on the most critical threats first.
6. Response and Containment
SIEM integrates with SOAR (Security Orchestration, Automation, and Response) platforms to take automated actions like:
- Blocking IP addresses
- Disabling compromised accounts
- Quarantining infected devices
7. Incident Investigation and Reporting
Analysts use SIEM dashboards to drill down into logs, trace attack paths, and generate compliance reports.
Real-World Examples of SIEM in Action
- Port Scan Detection:
An attacker scans a server for open ports. SIEM notices repeated failed connection attempts and flags it as reconnaissance. - Insider Threat:
A user downloads large volumes of data outside business hours. Correlation rules detect abnormal behavior and generate an alert. - Phishing Attack:
A user clicks on a malicious link, leading to unusual outbound traffic. SIEM correlates email logs, endpoint behavior, and DNS queries to identify the compromise. - DDoS Attack:
SIEM detects high traffic patterns targeting a web application and alerts security teams, helping them respond before service outage.
The Business Impact of SIEM
A strong SIEM solution doesn’t just improve IT security, it directly impacts business operations.
- Protects Revenue: Prevents costly breaches and downtime.
- Safeguards Reputation: Builds customer trust by avoiding high-profile security failures.
- Supports Compliance: Automates log collection, storage, and reporting for frameworks like ISO 27001, HIPAA, PCI DSS, GDPR, and NIST.
- Improves Decision Making: Provides CISOs and executives with real-time insights into risk and incident status.
Modern SIEMs also integrate with Governance, Risk, and Compliance (GRC) platforms, mapping technical security incidents to financial risk and business continuity.
SIEM and Compliance
Most industries are bound by strict security regulations. SIEM plays a key role in meeting them:
- ISO 27001: Requires log monitoring and retention with timestamps.
- PCI DSS: Mandates monitoring and reporting of cardholder data access.
- HIPAA: Requires healthcare organizations to log and audit access to patient data.
- GDPR: Demands accountability and logging of personal data processing.
By centralizing and securing logs, SIEM ensures organizations meet compliance requirements while also simplifying audit processes.
Benefits of SIEM
- Real-time threat detection across infrastructure
- Centralized log management with normalization
- Automated response capabilities to reduce Mean Time to Respond (MTTR)
- Compliance-ready reports for audits and regulators
- Improved SOC efficiency through correlation and prioritization
- Business risk reduction and better decision-making
Future of SIEM: Where It Is Heading
The next generation of SIEM is moving beyond traditional log collection and correlation. Key advancements include:
- Cloud-Native SIEMs designed for multi-cloud and hybrid infrastructures
- Artificial Intelligence and Machine Learning for anomaly detection without pre-configured rules
- Security Orchestration, Automation, and Response (SOAR) for faster and automated incident handling
- User and Entity Behavior Analytics (UEBA) to detect insider threats and compromised accounts based on activity patterns
These advancements ensure SIEM continues to be the nerve center of cybersecurity operations in modern enterprises.
Conclusion
A SIEM solution is a critical component of modern cybersecurity defense. By consolidating logs, correlating threats, and enabling fast response, SIEM protects not only networks but also business value.
With the rise of compliance mandates and increasingly complex IT environments, SIEM has become the central nervous system of enterprise security, providing visibility, intelligence, and action at scale.
Whether you are a financial institution, healthcare provider, or e-commerce platform, investing in SIEM is an investment in resilience, trust, and long-term security.














.webp)
