- Accessories
- Android
- Apple
- Applications
- Blog
- Bluetooth
- Cyber security
- Database Assessment
- Exploitation Tools
- Forensics
- Geeks
- Hacking Courses
- Hacking Tools
- Information Gathering
- iphone
- Kali Linux
- Kali Linux Tools
- Linux
- Malware
- New Post
- nsfw
- Password Attacks
- PCI
- Pentesting Tools
- Phishing
- Post Exploitation
- Sec Dictionary
- Security Hacker
- Sniffing/Spoofing
- software
- Stress Testing
- TECH
- Tech today
- Tutorials
- VPN
- Vulnerability Analysis
- Web Application Analysis
- Wi-Fi
- Windows
- Wireless Attacks
- YECH
APPLICATIONS
HOT NEWS
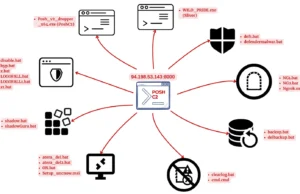
Identifying Accounts Used From A Threat Actor Device
In cybersecurity, identifying accounts accessed by a threat actor's device is a critical aspect of incident response and threat hunting.
This process is particularly...
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2024