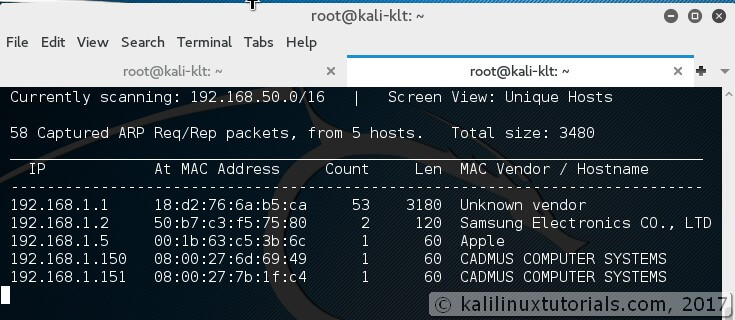
Netdiscover – simple ARP Scanner to scan for live hosts in a network
Netdiscover is a simple ARP scanner that can be used to scan for live hosts in a network. It can scan for multiple subnets also. It simply produces the output in a live display(ncurse). This can be used in the first phases of a pentest where you have access to a network. Netdiscover is a simple initial-recon tool that can be very handy.
Features:
- Simple Arp Scanner
- Works in both Active & Passive modes
- Produces a live display of identified hosts
- Able to scan multiple subnets
- Timing Options
Options:
-i device: your network device -r range: scan a given range instead of auto scan. 192.168.6.0/24,/16,/8 -l file: scan the list of ranges contained into the given file -p passive mode: do not send anything, only sniff -m file: scan the list of known MACs and host names -F filter: Customize pcap filter expression (default: "arp") -s time: time to sleep between each arp request (miliseconds) -n node: last ip octet used for scanning (from 2 to 253) -c count: number of times to send each arp reques (for nets with packet loss) -f enable fastmode scan, saves a lot of time, recommended for auto -d ignore home config files for autoscan and fast mode -S enable sleep time supression betwen each request (hardcore mode) -P print results in a format suitable for parsing by another program -N Do not print header. Only valid when -P is enabled. -L in parsable output mode (-P), continue listening after the active scan is completed
Lab: Simple Host discovery & Related Options
Netdiscover runs simply by calling executing the command in auto mode
Syntax: netdiscover <options>
Specifying Range
We can scan a specific range with -r option
Syntax: netdiscover -r <range> Command: netdiscover -r 192.168.1.0/24
Multiple Ranges from a File
We can also scan for multiple ranges. This is useful when you have a large network with multiple subnets & networks. For this, simply we need specify all the ranges we want to scan in a file line-by-line
Syntax: netdiscover -l <file containing ranges>
Command: netdiscover -l ranges
Passive Scanning
Sometimes it’s better to stay quiter. -p option helps on this but at the cost of patience.
Syntax: netdiscover -p -r <range,optional>
Parsable Outputs
There is a parsable output option also in case you want to pipe it to a file.
Syntax: netdiscover -P<parsable> -N<ommit headers> Command: netdiscover-r 192.168.1.1/24 -PN
Conclusion
Netdiscover is a simple arp scanner which can be used to enumerate hosts. I would like to share with you one of my experience. Out of curiosity, I tried running the tool in my company network. The network has a firewall & I am part of the monitoring team which needs to look for network traffic anomalies. So me & my team can get the info even if somebody is performing a ping between internal hosts. We have detected ping scans, web server scans with nikto etc from our internal network. So I had a clear idea about my target network. So I ran the tool in passive mode. It ran for about 7 hours & I got more than 100 IPs. I cross-checked this result with my monitoring tool and the numbers were about the same. But interestingly not even a single alert was generated from the monitoring tool. I also wondered why it didn’t detect that my interface was in promiscuous mode. So I got 2 major results out of this. One is that I got all the IPs in the network which were live over a period of time. The second is that my monitoring tool was not capable or was not configured to detect promiscuous interfaces in the network. So here are my suggestions.
- Never perform a scanning activity without having a clear knowledge of your network.
- As the Kali Linux slogan says “The quieter you are, the more you are able to hear”
- Use the results from such activities in a constructive way
So if you learned something new from this tutorial, please support me by sharing it with those whom this will benefit.



















.webp)