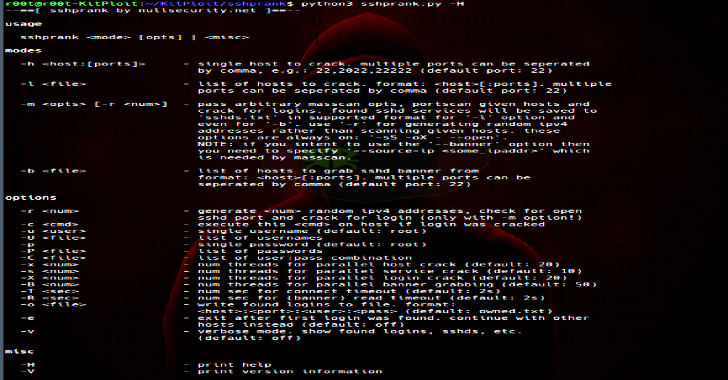
Secure Shell Bruteforcer – A faster & simpler way to bruteforce SSH server. In the evolving world of cybersecurity, speed and efficiency are paramount. Enter Kitabisa SSB, a Go-powered tool designed to revolutionize the approach to SSH bruteforcing. Offering a streamlined installation process and user-friendly options, it’s a must-have for professionals seeking a faster and simpler way to …
Continue reading “SSB – A Faster & Simpler Way to Bruteforce SSH Server.”